
Cover Pool Categories at Neptune Mutual
Explore Neptune Mutual's cover pools, and their benefits for cover creators and LPs.
Youtube Video
Playing the video that you've selected below in an iframe
Learn about EtherHiding, an attack on Web2 platforms by the use of BNB Smart Chain.
Blockchain technology, often hailed for its robust security features, has its own risks and vulnerabilities. However, the narrative takes an intriguing twist when the inherent features of blockchain are manipulated to orchestrate threats in the realm of Web2. This brings us to the forefront of a new and sophisticated cyber threat known as "EtherHiding."
In this article, we delve deep into the mechanics and implications of EtherHiding. This cyber threat involves merging the advanced capabilities of blockchain technology with the vulnerabilities of traditional web platforms. EtherHiding is a testament to how malicious actors can twist emerging technologies to create threats.
Let’s unravel the intricacies of EtherHiding, dissect its technical underpinnings, and discuss the broader implications of this cyber threat.
Guardio Labs, a cyber security-focused company, shared a report on October 15, 2023, explaining EtherHiding. As per the report, the attack leverages the unique properties of smart contracts in the BNB chain, turning them into trojan horses that infiltrate unsuspecting systems. But how does this sophisticated attack unfold?
The process begins with the compromise of WordPress websites, a popular target given their widespread use and inherent vulnerabilities. Attackers inject malicious code into these websites. But instead of hosting this malware directly on the servers, they ingeniously retrieve partial payloads from BNB smart contracts. These contracts, known for their transparency and immutability, are exploited to serve as anonymous and free hosting platforms for malicious payloads.
🚨 Guardio Labs exposes "EtherHiding" - a new threat hiding in Binance's Smart Chain, a technique that evades detection, targeting compromised WordPress sites. Read about this game-changing method! @BNBCHAIN #BNBChain #CyberSecurity https://t.co/alNI5KqKUO
— Guardio (@GuardioSecurity) October 15, 2023
What makes EtherHiding particularly daunting is its dynamic nature. The attacks are not static; they evolve and adapt. One of the most prevalent forms of this attack is the distribution of fake browser updates. Victims are lured to a fabricated landing page, where they are prompted to download updates. However, these updates are nothing but malware in disguise, leading to full site spoils and further propagation of the malicious code.
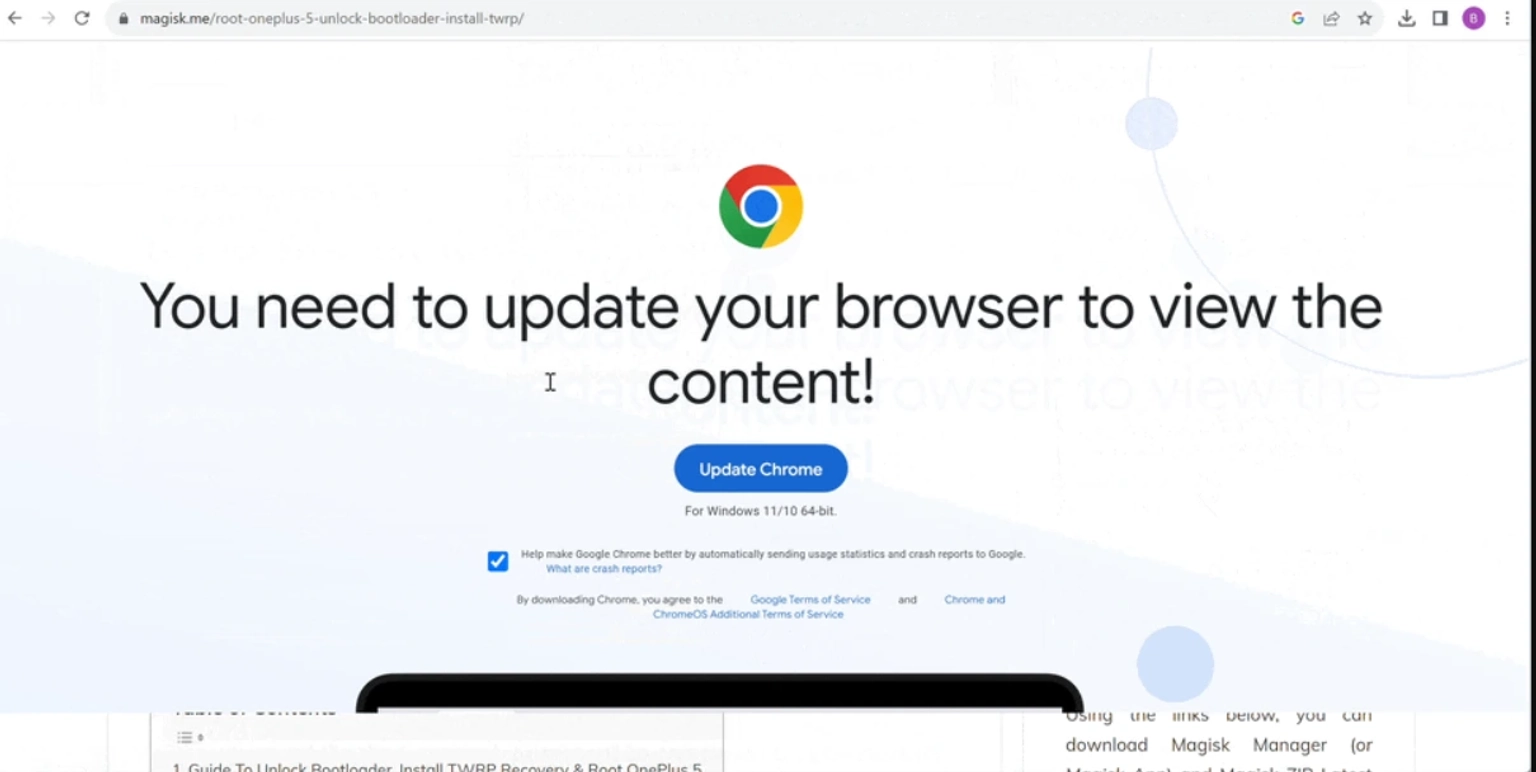
Fake Browser Update
Previously, attackers would host malicious code directly on compromised servers or use traditional hosting services, which, while effective, left a trail that security experts could trace and mitigate. With EtherHiding, attackers have found a new haven in BSC contracts. These contracts, designed for transparency and security in the blockchain realm, are repurposed as anonymous vessels for hosting malicious payloads.
Traditional methods of taking down malicious websites or servers become ineffective when the malicious code resides in a BSC smart contract. These contracts operate autonomously, making the detection and mitigation of such attacks a daunting task for security professionals.
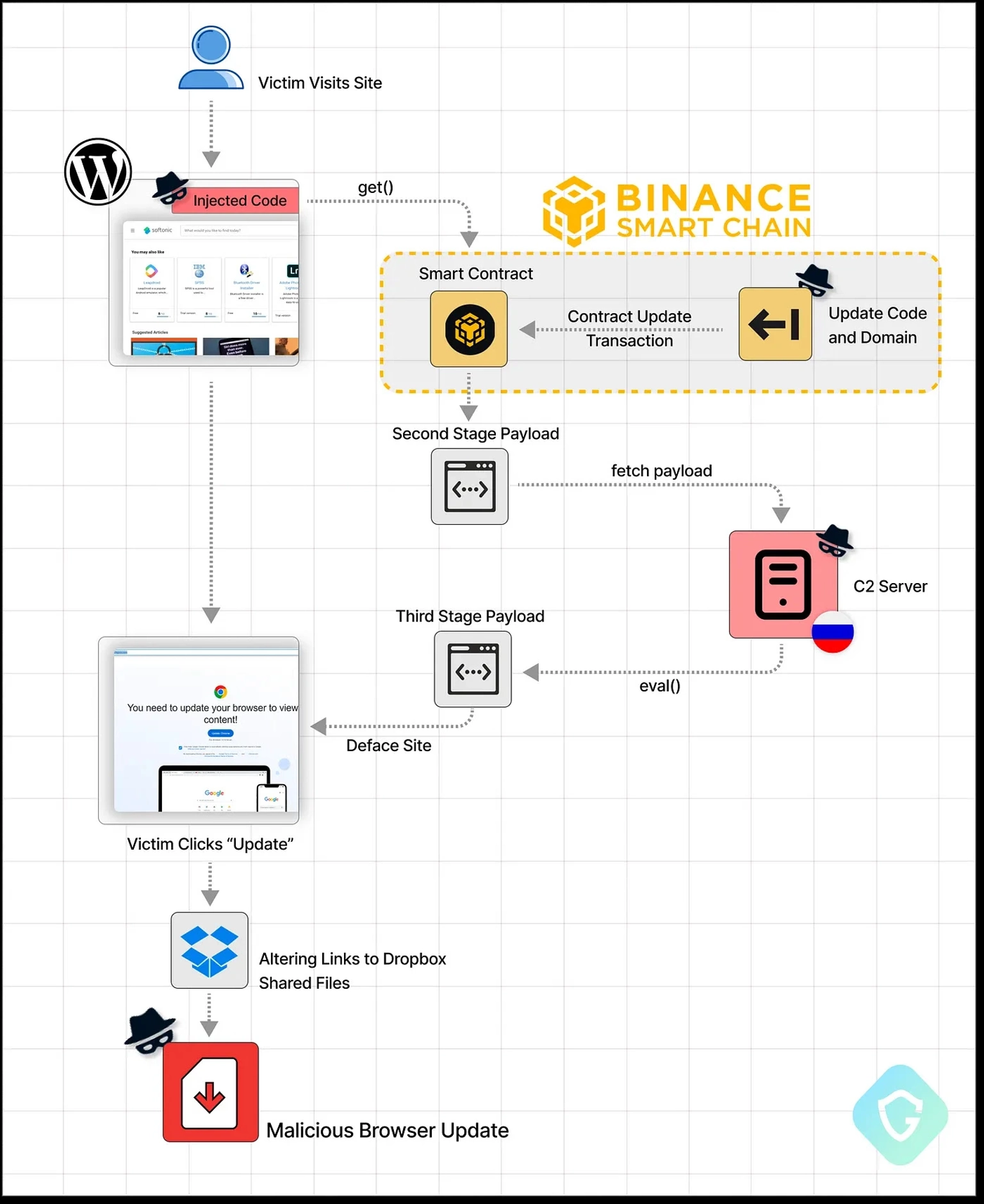
Working of EtherHiding Explained [Image Source: Guardio Labs]
A notable manifestation of the EtherHiding threat is the "ClearFake'' campaign. Attackers inject concealed JavaScript code into these compromised sites, effectively turning them into launchpads for further malicious activities. The initial code retrieves a second-stage payload from a server controlled by the attackers. This payload is responsible for the rest of the site’s sabotage, displaying a highly convincing overlay that demands a browser update. However, this "update" is a fake designed to infiltrate the victim's system with information-stealing malware.
In the progression of the ClearFake campaign, attackers demonstrated adaptability and resilience. Initially, the second-stage code would be hosted on Cloudflare worker hosts, leveraging the robust infrastructure of Cloudflare to serve malicious content. However, when Cloudflare took action and blocked these accounts, the attackers quickly pivoted. Because the blockchain is decentralized and anonymous, the hosted malicious code becomes harder to detect and take down.
After the deployment of the infected smart contracts, they function independently. The only recourse for BSC in such scenarios is to depend on the vigilance of its developer community to identify and report any malicious code found within these contracts.
The choice of Binance's infrastructure for EtherHiding is strategic. The Chain is known for its high performance, low transaction fees, and robust ecosystem supporting a wide array of applications.
These features make BSC attractive not just to legitimate developers and users but also to attackers seeking a reliable and cost-effective platform to host their malicious endeavors. The very attributes that contribute to BSC's success in the blockchain world also make it an appealing vector for cyber threats.
The decentralized nature of blockchain makes it difficult to take down or alter malicious content once it's embedded in a smart contract. This ambivalence of decentralized technology presents a complex challenge, requiring a balanced approach that preserves the benefits of decentralization while protecting against its potential for abuse.
In the shadow of sophisticated cyber threats like EtherHiding, the importance of robust digital security and protection mechanisms becomes increasingly important. Neptune Mutual is a project that focuses on the same principle: protection against online threats. We are committed to safeguarding users and their funds against the kinds of vulnerabilities exposed by attacks in the Web3 space.
Neptune Mutual is a solution in the DeFi insurance landscape, aiming to fortify the security framework of the DeFi sector and ensure the safeguarding of digital assets. Operating on an innovative parametric model, it ensures that payouts are determined based on predefined parameters.
It streamlines the process by eliminating the need for lengthy and complex claim verification processes. In the event of a security breach, such as a hack or exploit, policyholders are assured of receiving timely payouts, thereby minimizing their financial risk without the burden of providing proof of loss.
We offer a marketplace available on the Ethereum, Arbitrum, and BNB Smart Chain networks. Projects can create cover pools on the marketplace, letting their users purchase cover policies.
We invite you to reach out to us through our contact page. Our dedicated team is ready to assist you in setting up cover pools and defining parameters that align with your project's unique requirements.