
Collaboration between Neptune Mutual and SushiSwap
Explore Neptune Mutual's ongoing collaboration with SushiSwap offering several benefits.
Youtube Video
Playing the video that you've selected below in an iframe

Learn about SIM swap attacks and how users can take preventive measures against them.
The landscape of cryptocurrencies and decentralized finance has opened up exciting possibilities, but it's also a breeding ground for hackers, exploiters, and scammers. Hacks and exploits have become all too mainstream in this realm, where the lure of vast fortunes often meets the vulnerabilities of the digital world.
To put the gravity of the situation into perspective, let's examine these staggering numbers: In 2020, over $4.3 billion was lost to hacks and exploits in the crypto world. This figure rose to $9.79 billion in 2021 and $4.39 billion in 2022. Alarmingly, as of 2023, the trend shows no signs of slowing down, with losses surpassing $1.5 billion in just the first half of the year.
Alongside smart contract vulnerabilities, the Sim Swap attacks have emerged as a particularly devastating threat. This fraudulent scheme entails convincing a mobile service provider to transfer a victim's phone number to a new SIM card under the attacker's control. The process may seem complex, but attackers can execute it from the comfort of their homes with just a SIM card, a phone call to the victim's mobile provider, and personal data. Gathering someone’s personal information is disturbingly simple and can be acquired through various means, including social media, the black market, or phishing sites that deceive users into disclosing their private details.
Armed with this information, cybercriminals contact the victim's mobile carrier, presenting themselves as the legitimate account holder. Once successful, the attacker gains control of the victim's phone number, cutting off the victim's access to calls, texts, and internet services. This sinister tactic can lead to a cascade of catastrophic consequences, including unauthorized access to accounts and sensitive data. Even prominent figures in the security-conscious cryptocurrency world, such as Vitalik Buterin, have fallen victim to the devastating impact of SIM swap attacks.
Vitalik Buterin, the co-founder of Ethereum, is known for his deep understanding of security in the blockchain world. Yet even someone of his stature can fall victim to these attacks, underscoring the fact that in the ever-evolving digital landscape, no one is immune to the threat. This incident serves as a stark reminder that despite the best efforts, human errors and vulnerabilities can persist.
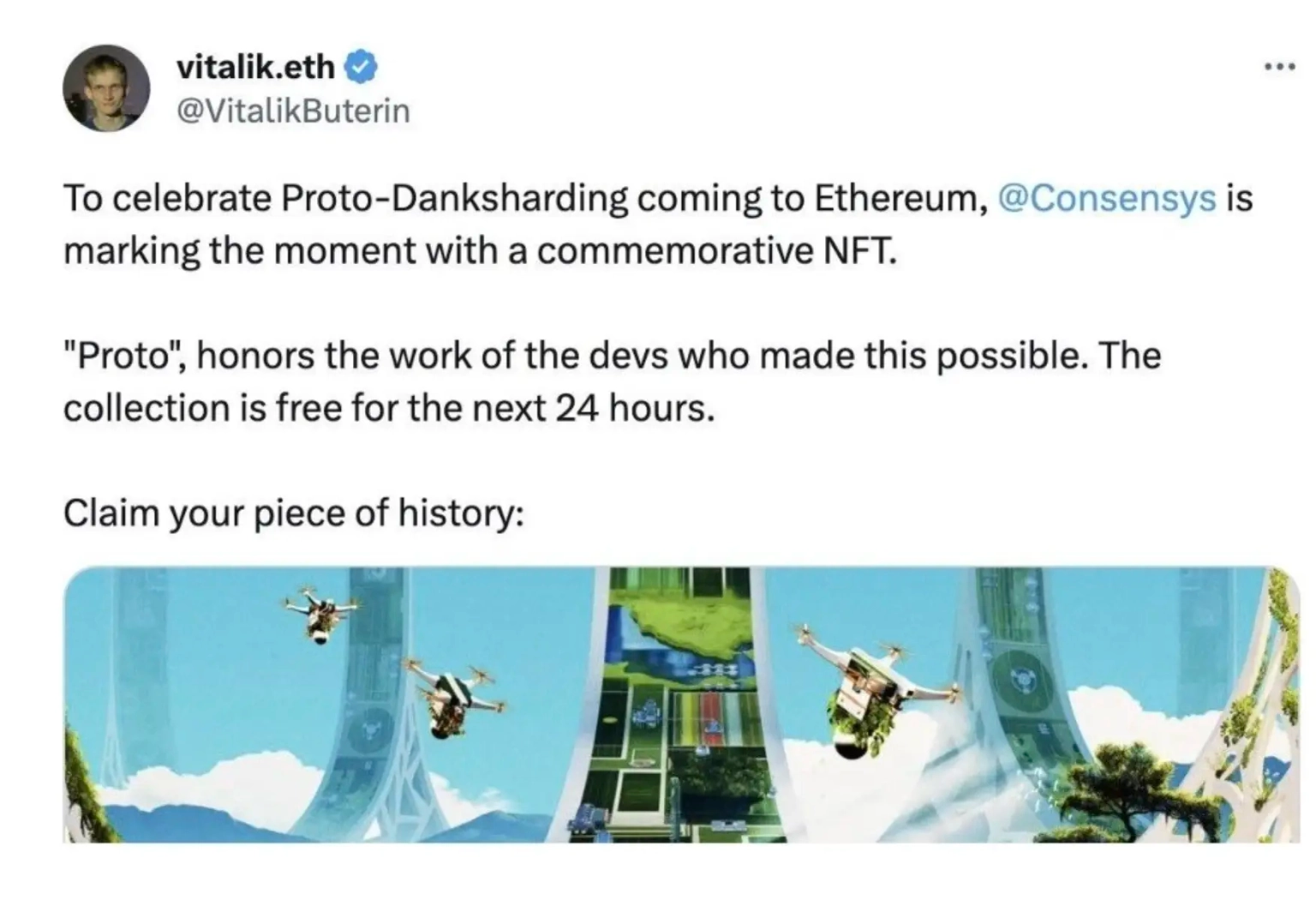
After the Sim Swap attack, the scammer took control over Vitalik Buterin's Twitter account. The con artist then posted a phishing link to a free Proto Danksharding NFT relating to ConsenSys. Multiple sources and on-chain data reveal that the con artist stole over $700,000 in funds. One of the affected individuals lost about 50% of this value as their CryptoPunk NFTs 3983 and 1751 were hijacked.
The consequences following his account takeover would have been far worse than anticipated. This incident sent shockwaves through the crypto community, highlighting the urgent need for enhanced security measures and education on common security practices.
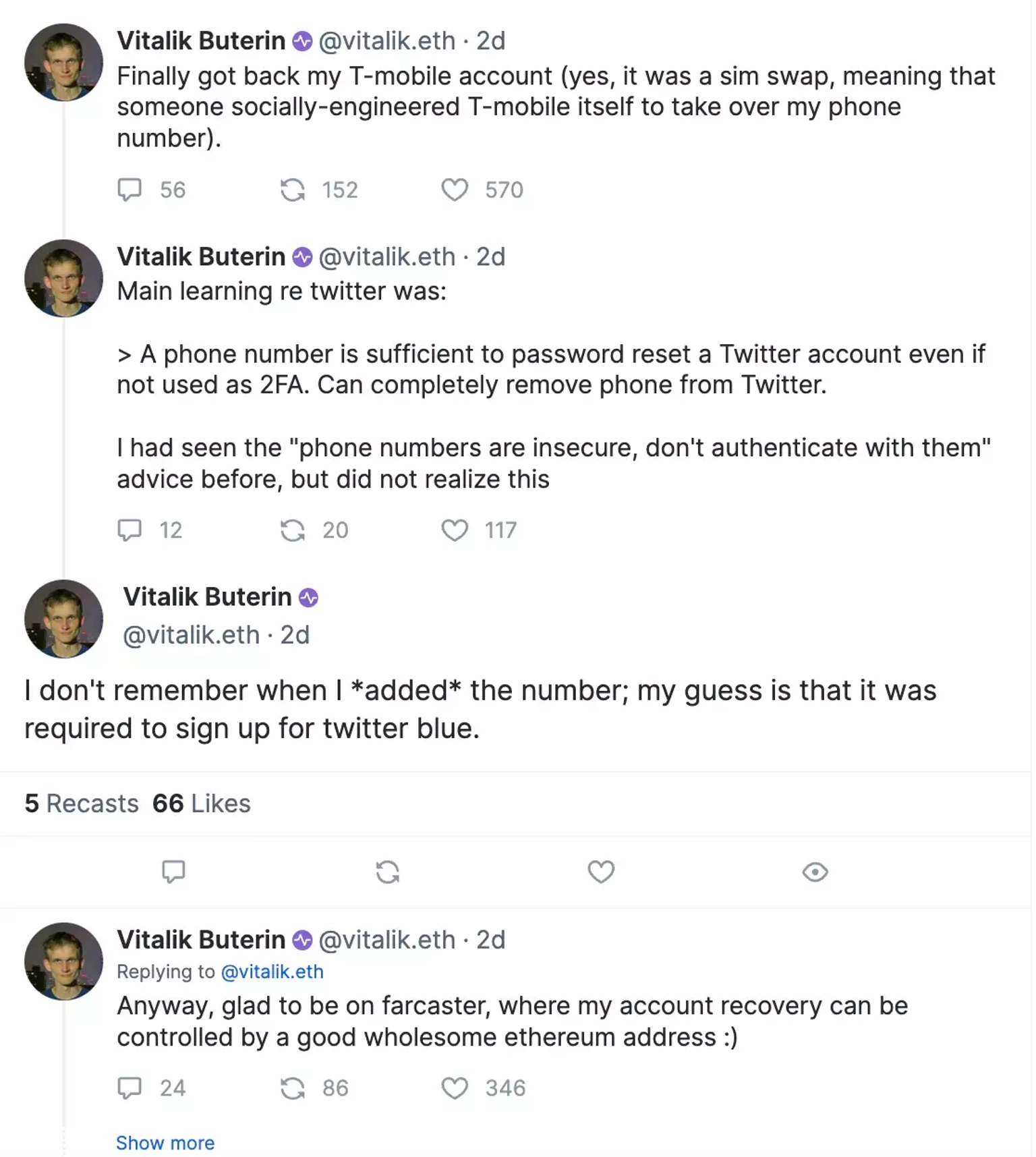
Sim Swap attacks have been on the rise, with 2023 witnessing a surge in incidents. As per the investigation by ZachXBT, over $13.3 million was lost across 60 different cases of Sim Swap between April 2023 and August 2023. The list includes high-profile figures, influencers, and renowned DeFi protocols, further emphasizing the urgency of addressing this threat. According to him, a majority of these affected individuals had taken their SIM cards from providers such as T-Mobile, Verizon, and ATT. Scammers tend to create a sense of urgency by sharing a phishing link promising a free airdrop of tokens or other digital assets, as well as other exciting opportunities to steal the assets from the compromised accounts.
Over the past four months $13.3M+ has been stolen as a result of 54 SIM swaps targeting people in the crypto space.
— ZachXBT (@zachxbt) August 23, 2023
When an account is compromised scammers attempt to create a sense of urgency with a fake claim to drain your assets.
Never use SMS 2FA and instead use an… pic.twitter.com/Fu1C3syQJE
To safeguard against Sim Swap attacks leading to phishing attempts, proactive steps must be taken. Here is a comprehensive list of some of these preventive measures:
However, it's important to note that genuine banks, government agencies, and reputable health offices will never request your personal information online. If you happen to receive such calls or messages, it's advisable to disconnect or delete them, even if they appear authentic. You can always independently contact the respective agency to verify the authenticity of the communication.
In the ever-evolving crypto landscape, security must remain at the forefront. The rise of Sim Swap attacks, as witnessed through the recent victimization of Vitalik Buterin, serves as a stark reminder of the relentless persistence of malicious actors.
While the crypto world offers unprecedented opportunities, it also demands vigilance, awareness, and proactive security measures. This is what we are striving for at Neptune Mutual. The road ahead involves fortifying defenses, staying informed, and collectively striving for a safer and more secure decentralized future. You can find plenty of resources in the Neptunite Ecosystem to stay ahead of the curve on your road to cyber safety. You can acquire protection in the Neptunite Cover Marketplace for your digital assets. Take a look at our hack database, and you can be the first to know about hacks and exploits happening in real time with dedicated analysis drafted by our security experts just for you. Contact us if there’s any way we can support you