
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Nimbus Platform was exploited using flash loan attack losing upto 278 BNB, approx $76,000.
On December 14, 2022, NimbusPlatform on BSC chain was exploited using flash loan attack, with the attacker profiting 278 BNB, worth approximately $76,000.
Nimbus is a DAO-governed platform that provides users with multiple earning strategies backed up by numerous levels of risk control.
The root cause of this vulnerability is due to the flaw in rewards computation, which only depend on the number of tokens in the pool, leading to being manipulated by flash loans, to obtain more rewards than expected.
Step 1:
We attempted to decode the attack transaction executed by the preparator.
Step 2:
To compute the staking reward, the price feeds of $NIMB and $GNIMB, the reward token, are required. The price of $NIMB, on the other hand, is computed using the manipulated $NIMB minus $NBU_WBNB pair.
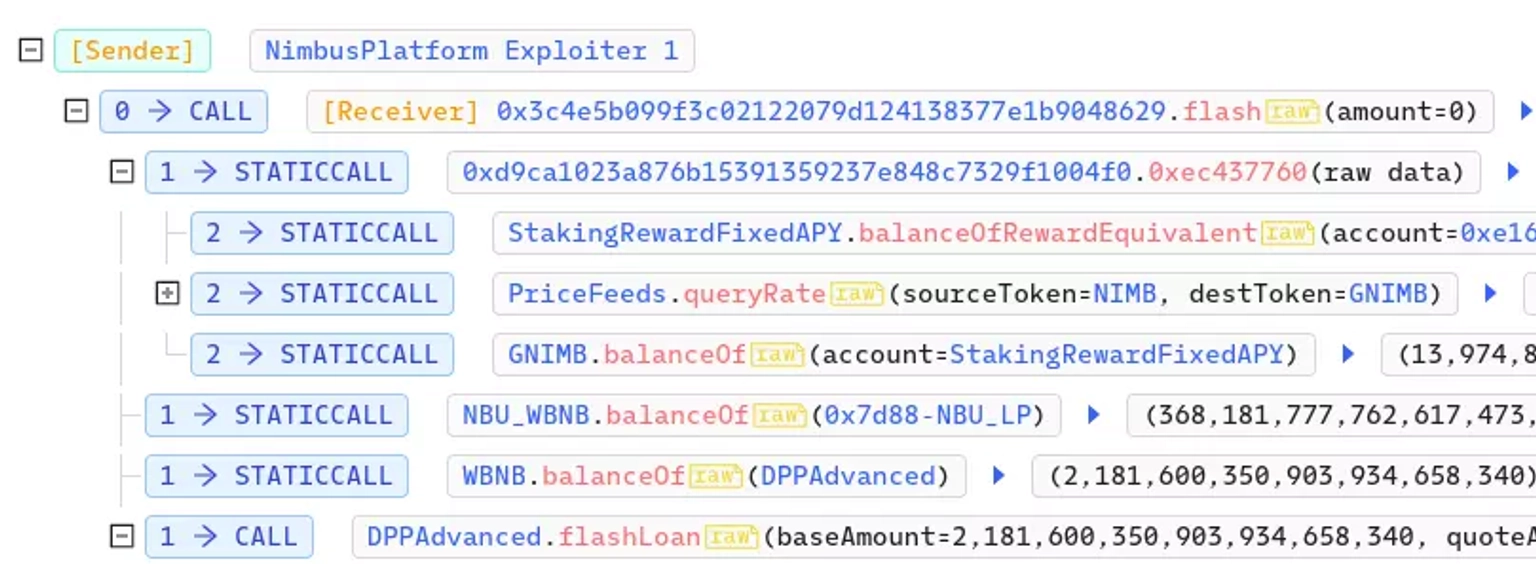
Nimbus Exploiter Transaction Call Stack. Courtesy of BscScan.
Step 3:
As a result, the oracle can be manipulated, allowing the hacker to claim more collateral rewards.
Step 4:
The exploitor borrowed 75,477 $BNB and swapped it for $NBU_WBNB to withdraw the majority of the $NIMB from the pool.
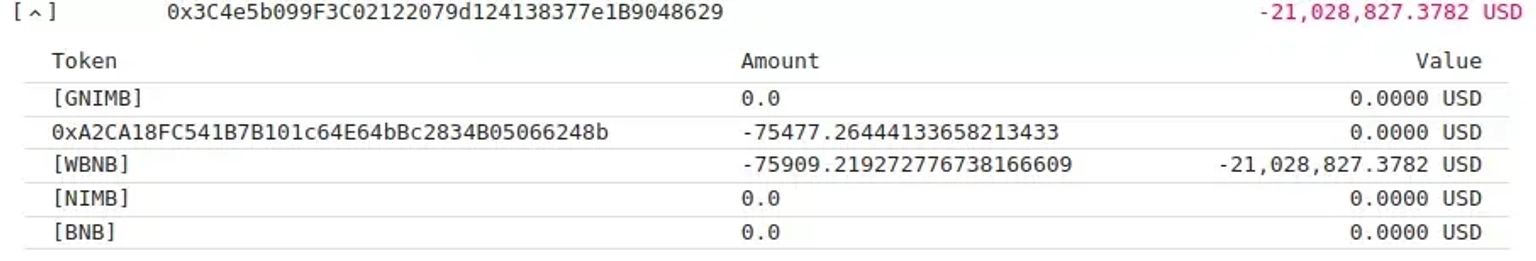
Step 5:
Since the computation of the token reward was proportional to the ratio of $NIMB and $GNIMB in the pool, the call to the getReward function in the Staking contract enabled the hacker to obtain a far higher reward than anticipated.
Step 6:
Prior to the attack, the ratio of Nimbus Utility tokens to Nimbus Governance tokens was 0.069:1, but owing to flashloan and swap, the ratio climbed to 2919.7:1, resulting in a significantly greater payout.
Step 7:
The exploiter then swapped $GNIMB for $BNB in order to repay the flash loan.
Step 8:
The profit from these transactions are now being held at this address.
The team hasn’t provided any coverage to the incident.
In an unfortunate event, Nimbus Platform on the BNB chain fell prey to a flash loan attack, resulting in the attacker walking away with a profit of 278 BNB, equivalent to approximately $76,000. To prevent such vulnerabilities in the future, it is imperative to meticulously design token reward mechanisms that strike a balance between liquidity and security. Implementing data providers like ChainLink could aid in regulating such attacks involving Oracle price manipulation.
In this context, the importance of platforms like Neptune Mutual becomes evident. Although our standard terms and conditions might restrict coverage for exploits arising from flash loans, exceptions can be made in certain cases. Neptune Mutual's parametric cover policies offer an avenue for users to claim payouts without the need for extensive loss evidence, expediting the recovery process once an incident is resolved through the governance system.
Additionally, beyond smart contract audits, the multifaceted security evaluation conducted by Neptune Mutual's security team encompasses aspects such as DNS and web-based security, smart contract evaluations, and both frontend and backend security. By offering dedicated cover pools within its marketplace, Neptune Mutual could have extended a robust safety net to projects like Nimbus Platform, significantly reducing the potential impact of such attacks and fostering a more secure DeFi ecosystem.