
Taking a Closer Look at the YIEDL Exploit
Learn how Yiedl was exploited, resulting in a loss of assets worth approximately $160,000.
Youtube Video
Playing the video that you've selected below in an iframe

Learn about how the multiple 51% attacks were carried out on Ethereum Classic on 2019.
In the first week of January 2019, a hacker exploited ETC via a 51% attack, in which they caused a loss of funds worth 219,500 ETC, roughly amounting to $1.1 million. ETC was also a target of multiple 51% attack during 2020.
Ethereum Classic is a decentralized network made up of an ecosystem of on-chain smart contracts and services, a native cryptocurrency called ETC, and a blockchain ledger.
Ethereum Classic is a version of the Ethereum network that has not been changed. The original Ethereum network was released in 2015. But in 2016, due to a Reentrancy Attack on The DAO, the Ethereum Foundation created a hard fork of the network to try and minimize the loss caused by it. This new hard fork erased the hack from its history and continued with the Ethereum brand name. After the Ethereum hard fork, the original chain was thenceforth referred to as Ethereum Classic with a new token ticker “ETC”.
A 51% attack is an attack on a blockchain that happens when an individual or group is able to gain control of more than 50% of the network's hash power. Hash power is the computational power used to run and solve complex mathematical problems to create a new block. Transactions on Ethereum Classic are verified using the Proof of Work (PoW) consensus algorithm. A PoW-based blockchain can be attacked if the attackers have control over more than 50 percent (51%) of the network's hash rate.
A successful 51% attack enables , an attacker to use their hash power to exert control over the blockchain, preventing new transactions from being confirmed, or reversing or modifying past transactions.
Let's see how that can be done -
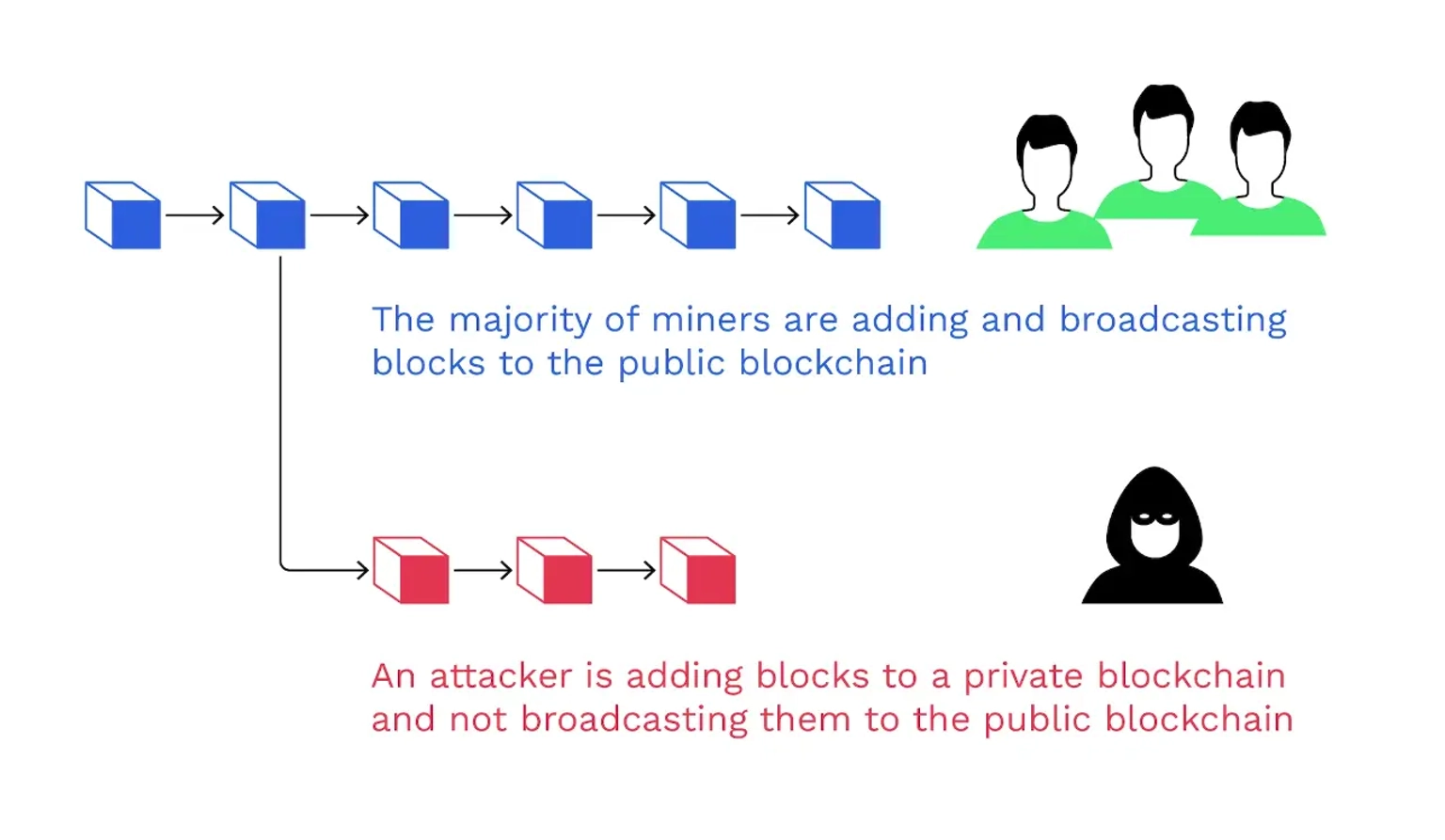
51% Attack Explained. Image Courtesy of Bitpanda
ETC was a target of multiple 51% attacks. The root cause of the vulnerability was due to rented hash power for the attack.
In the initial week of January 2019, the first attack took place in which Coinbase identified a deep chain reorganization where out of a total of 15 attacks, 12 attacks included double spend of 219,500 ETC.
The attacker extracted a huge number of ETC from the Binance wallet, and then transferred those tokens to the other wallet addresses they controlled. All of the transactions would normally have been confirmed on the ETC blockchain, however they were no longer validated due to the rollback of the blockchain.
Attack 2020:
Later, in between July and August 2020, three more attacks were carried out. In the first two, double-spend attacks took place on crypto trading platform OKEx (now OKX).
Over the course of the first attack, 11 malicious transactions originating from a single address were inserted into the Ethereum Classic blockchain, resulting in the reorganization of 3,000 blocks allowing more than 807,000 ETC to be double-spent.
The second attack happened within a week following the earlier attack and had a similar reorganization depth (about more than 4,000 blocks).
The then third attack of the month came as the final attack resulted in a massive reorganization of 7,000 blocks, but there were still no indications of a double-spend attempt.
During the first 51% Attack of 2019, the hacker sent 100k USD worth of ETC to Gate.io after a few days of the attack. However, the major consequences of the attack for ETC was disturbing as it was one of three cryptocurrencies that Thailand's Securities and Exchange Commission banned from usage in initial coin offerings and as a trading pair in February 2019.
In the first two double-spend attacks, hackers stole more than $5 million in ETC. With the shock of the awful month which had three consecutive attacks, ETC urgently used MESS as a network security solution. MESS was deployed on October 11, 2020 at block height 11,380,000 and was intended to lessen the risk of 51% attacks on the ETC network. Now attacking the chain would be 31 times more expensive with MESS than it was before.
It is crucial to ensure that no single miner, group of miners, or a mining pool is controlling more than 50% of the blockchain network's computing power. Thus, hackers wanting to attack a blockchain will likely be unable to outbuild the longest existing and validated chain.
To avoid the possibility of a 51% attack, a blockchain network can adopt Proof of Stake (PoS), a more secure consensus algorithm than Proof of Work (PoW). A 51% attack occurs under PoW when one entity controls more than 50% of the network's hashpower and uses this to alter the blockchain. In PoS, however, a group or individuals must own 51% of the staked cryptocurrency, which is inherently expensive. Mostly, PoS incentives are regulated by the most affluent users who are unlikely to undertake the hack, as they would have to risk losing their entire staked amount by doing so.
Reference Sources Cointelegraph, Forbes, Messari, Investopedia, Coingeek