
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Hackers were able to drain funds from Mango via price manipulation resulting approx $116M loss.
On October 12, 2022, hackers were able to drain funds from Mango via price manipulation, resulting in approximately a $116 million loss of assets.
Mango is a decentralized autonomous organization.
Mango Markets provides a platform for lending, borrowing, swapping, and leveraged trading of crypto assets. Built on the Solana blockchain, it uses Serum DEX for spot margin trading and Mango Markets' own order book for perpetual futures trading.
The vulnerability appears to be caused by the hackers' ability to manipulate collateral, in which they temporarily spiked the value of their collateral and then take out massive loans from the Mango treasury.
Step 1:
At the time of this writing, the protocol is drained for more than $115 million.
Step 2:
It is known that the team were notified of the full details of the potential occurrence of the exact vulnerability 7 months ago, but they likely took little to no mitigation measures.
Step 3:
The attacker funded an account with $5 million in USDC collateral from FTX.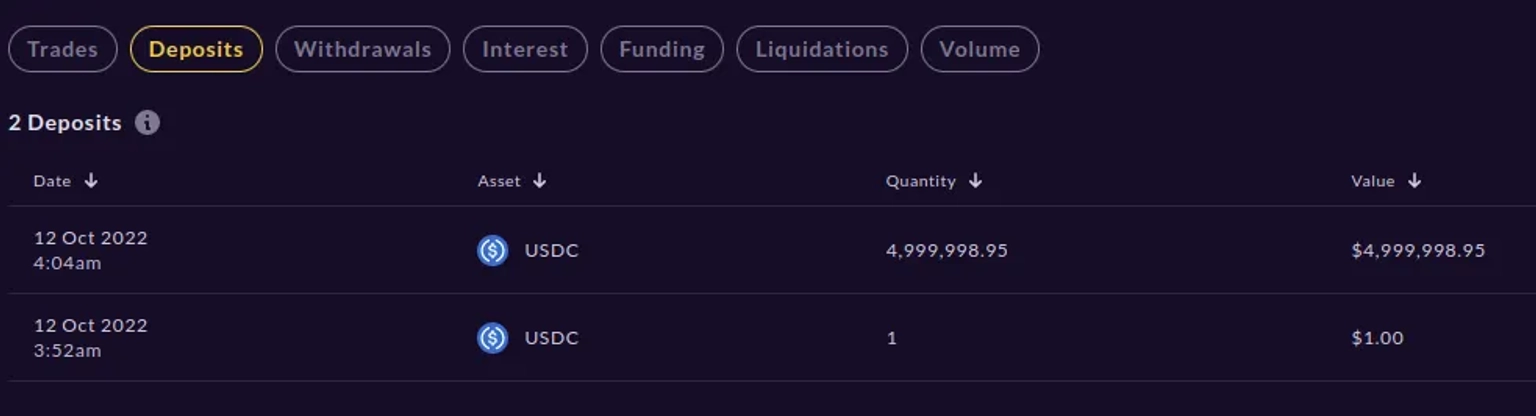
Step 4:
The perpetrator accounts took a large position of stake in MNGO-PERP.
Step 5:
The attacker funded another address with 5 millions USDC collateral to buy those 483 millions units of MNGO perps.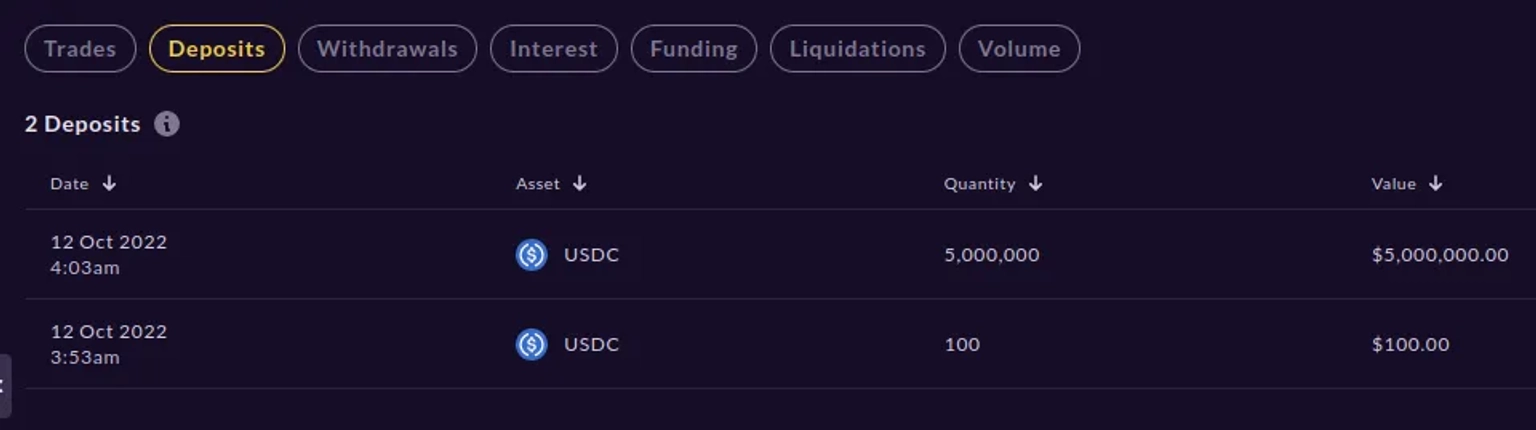
Step 6:
The underlying MNGO/USD prices on various exchanges, including FTX and Ascendex, increased 5-10x in a matter of minutes.
Step 7:
This prompted Switchboard and Pyth oracles to raise their MNGO benchmark price.
Step 8:
The unrealized profit caused a mark-to-market increase in the value of the account that was long MNGO-PERP which allowed the account to borrow and withdraw BTC, USDT, SOL, mSOL, USDC out of the Mango protocol.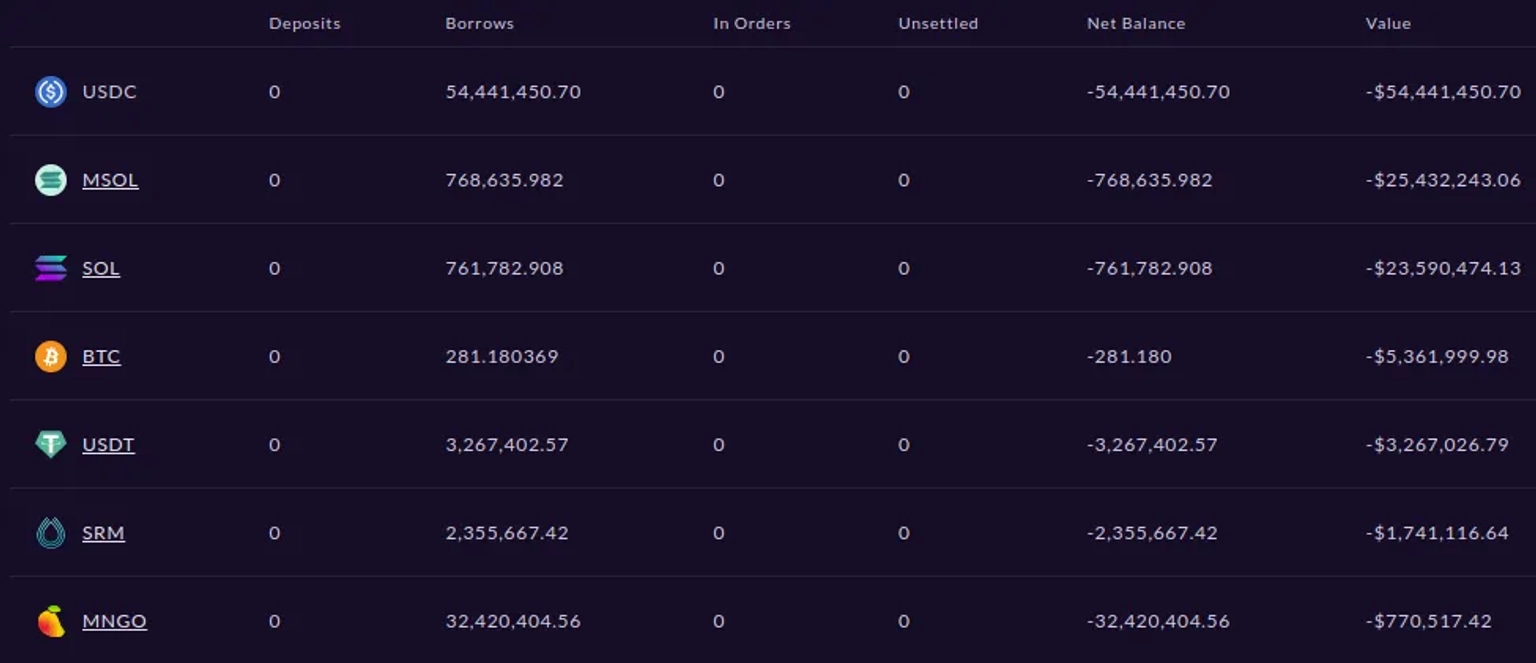
Step 9:
The event let to maxed out the borrows available from the $190 million equivalent deposits on the platform.
Step 10:
The net value extracted by the account during the event was equivalent to around $100 million.
The native token of the protocol has plunged 44% to $0.022. During the attack, MNGO surged to $0.087 before falling after the collateral was drained.
Following the exploit, the Mango program instructions were frozen to prevent any further interaction with the protocol, such as depositing additional funds that may not be recoverable.
This incident effectively drained all available equity, preventing users with deposits on the protocol from withdrawing assets.
After that, the attacker published a governance proposal that suggested the Mango DAO utilize its $70 million treasury to pay off the bad debts. Nearly 33 million people have voted in support of the proposition, the majority of which were probably spoils from the heist from the attacker themselves.
The attack is down to an economic design flaw. The parameters, prerequisites, and activities that must be carried out in the smart contract should be specified in writing for each available function.
Our security team at Neptune Mutual can validate your platform for DNS and web-based security, smart contract reviews, as well as frontend and backend security. We can offer you a solution to scan your platform and safeguard your protocol for known and unknown vulnerabilities that have the potential to have catastrophic long-term effects. Contact us on social media if you are serious about security and have the budget, desire, and feeling of responsibility to do so.