
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

The TopGear vault of Brahma (brahTOPG) project was attacked resulting in a loss of $89,343.
On November 9, 2022, the TopGear vault of Brahma (brahTOPG) project was attacked, in which the hacker was able to steal 89,343 $USDC.
Brahma is a non-custodial protocol that activates and manages liquidity across chains and decentralized applications and enables effective capital utilization in the DeFi ecosystem.
The vulnerability is caused because the Zapper contract rigorously checked for incoming user data, which resulted in an arbitrary external call.
Step 1:
The exploit transaction can be seen here.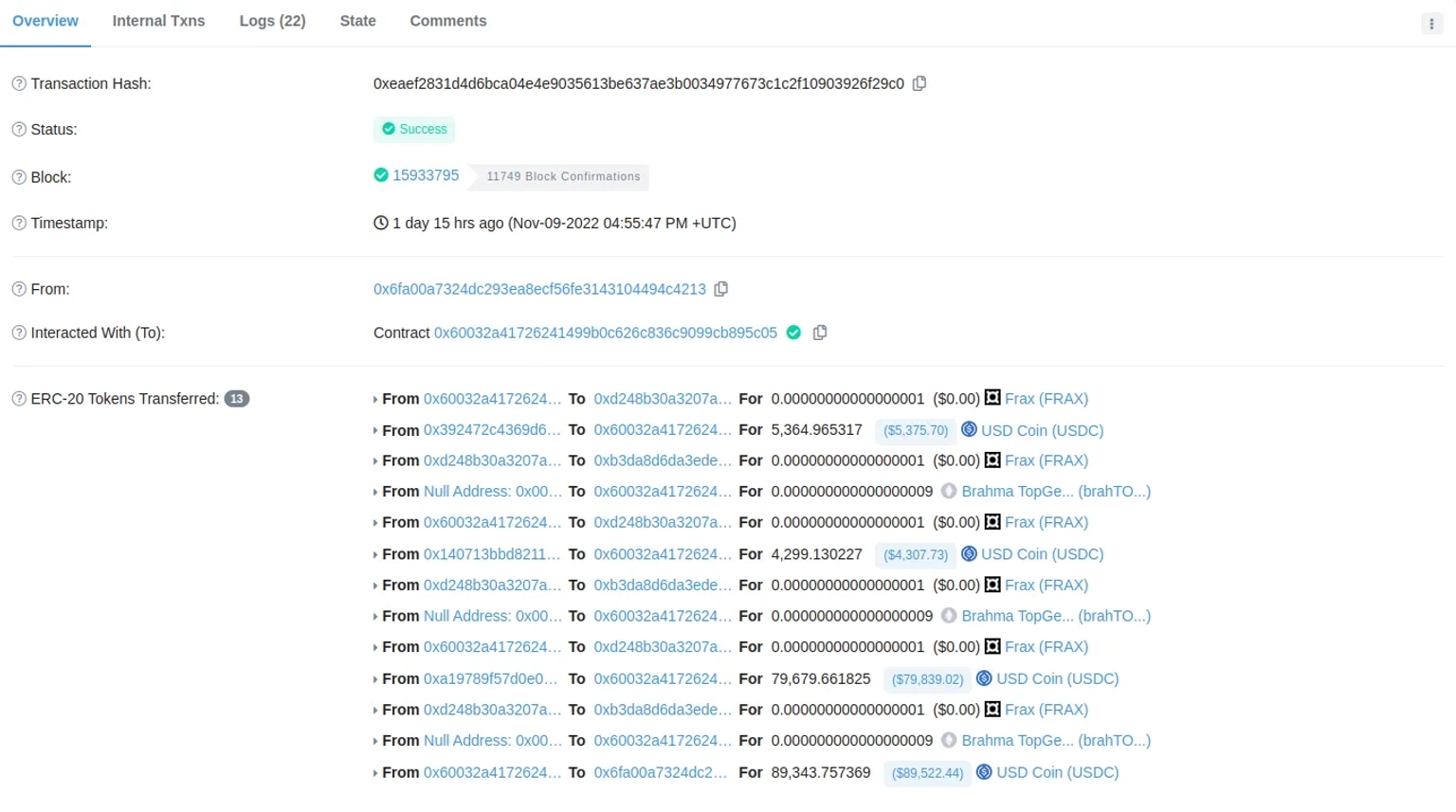
Step 2:
The attacker first queried the balance of one of the users, and then called the zapIn function of the Zapper contract.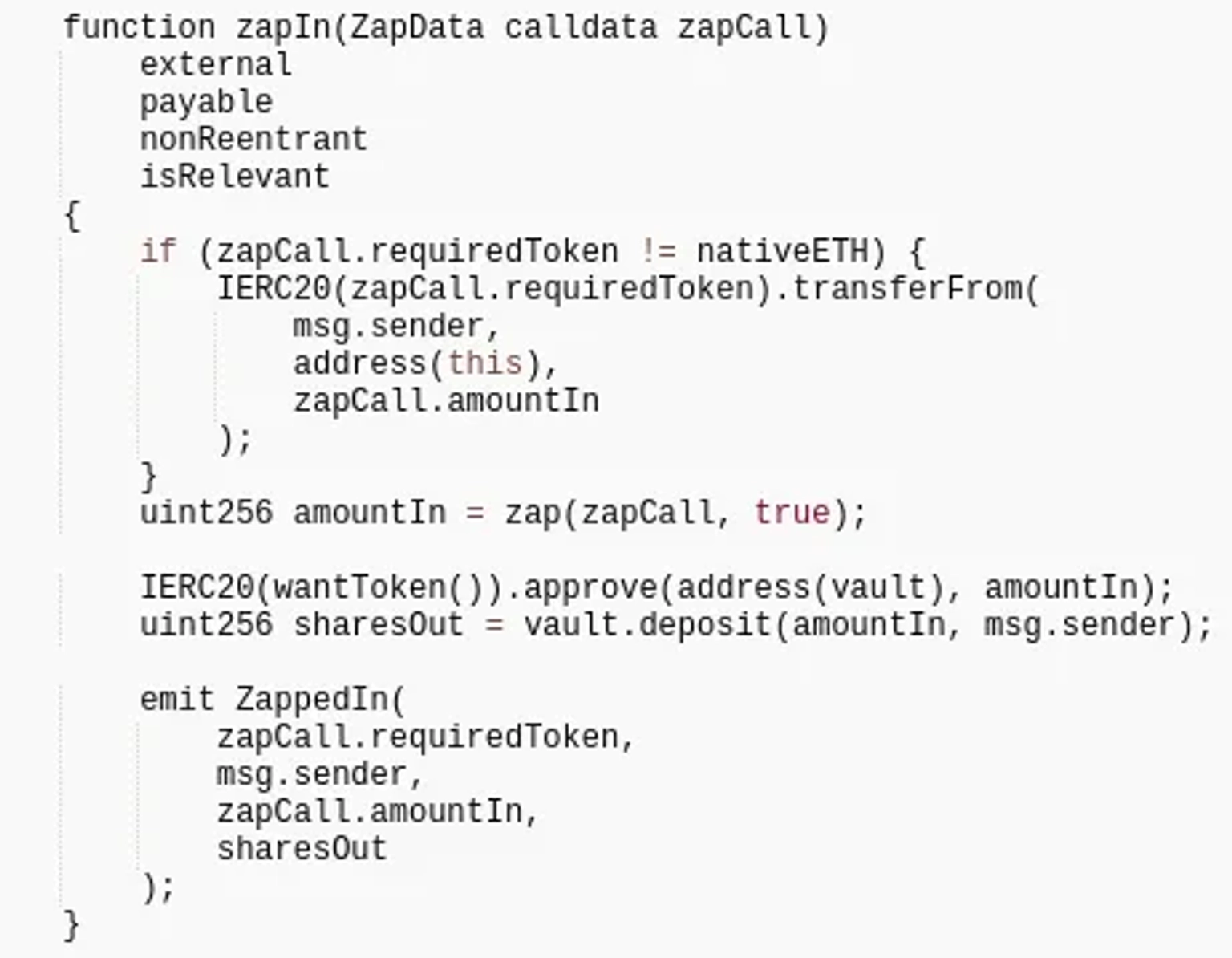
Step 3:
This function will transfer the token supplied by the requiredToken parameter to the contract.
Step 4:
The parameter passed in by the function can be modified externally, allowing the attacker to create a fake token for the requiredToken and then transfer it to Zapper contracts.
Step 5:
A call is made to the internal function zap, which checks whether the balance of the fake token in the contract is greater than or equal to the value supplied in.
Step 6:
The attacker is able to proceed to the next line of code because the balance value was already queried before.
Step 7:
The attacker created this function to transfer frax tokens to the Zapper contract, which will then be deposited into the vault.
Step 8:
The attacker was able to transfer USDC tokens from other authorized users since the contract specified by the swapTarget argument is called externally, and the parameters passsed to the call were also externally constructible.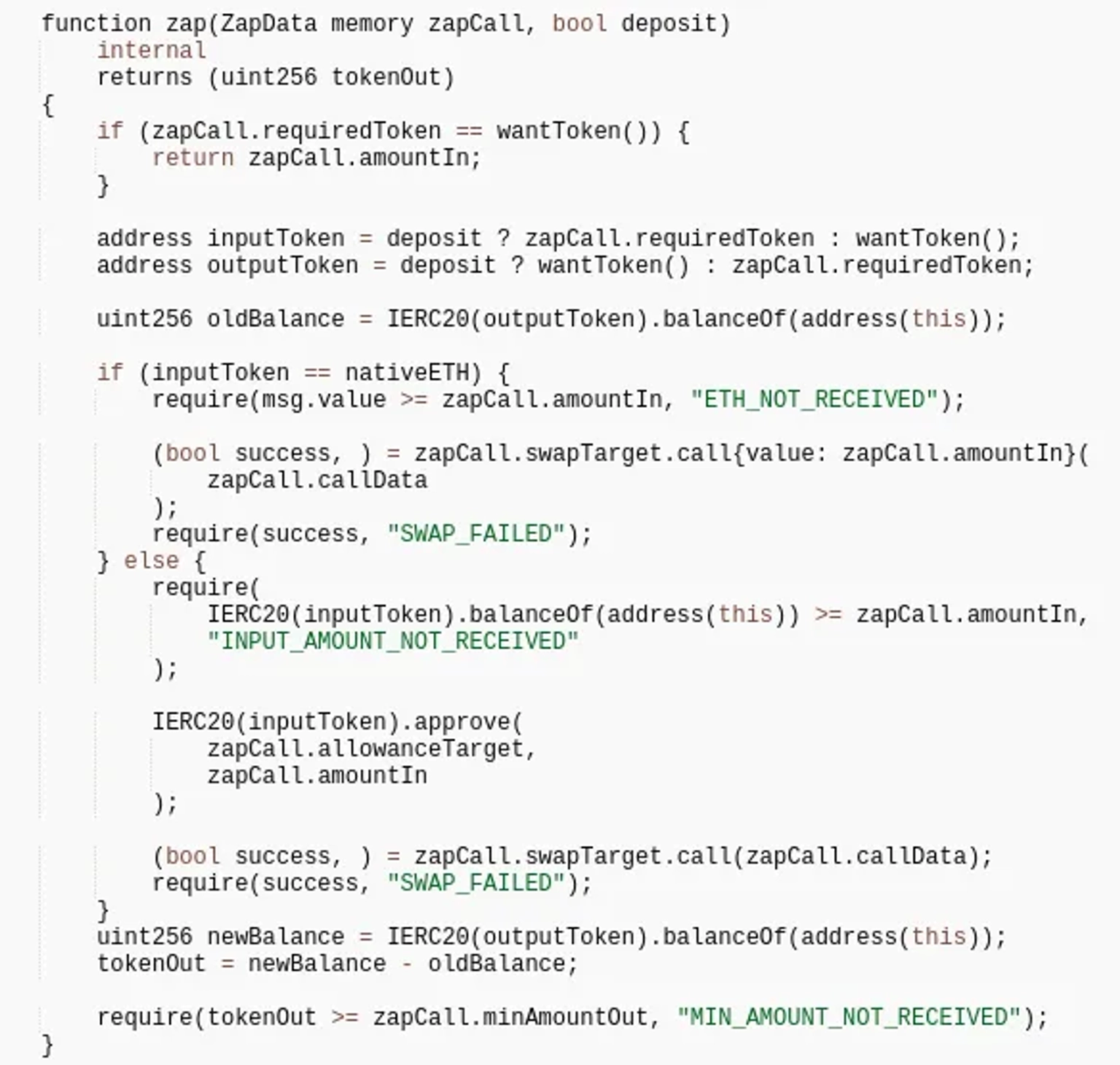
Step 9:
The attacker repeated these actions three times, ultimately stealing the USDC balance from the accounts of three victims.
The team is yet to publish a detailed postmortem report to explain the cause and consequences of this incident.
The TopGear vault of the Brahma (brahTOPG) project fell victim to an attack that resulted in the theft of 89,343 USDC. The vulnerability assessment identified a flaw arising from the Zapper contract's meticulous examination of incoming user data, inadvertently leading to an arbitrary external call.
A potential countermeasure for preventing this exploit would have involved stringent validation techniques to restrict any external calls to the contracts.
Additionally, had the team associated with Brahma established a dedicated cover within Neptune Mutual, the impact or aftermath of the attack could have been significantly reduced. Users who purchase our parametric cover policies do not need to provide evidence of their loss to receive payouts. Once an incident is confirmed and resolved through our incident resolution system, payouts can be claimed immediately.
In conclusion, the attack on Brahma's TopGear vault underscores the indispensable importance of robust security measures within the realm of decentralized finance. Neptune Mutual stands ready as a dedicated partner, augmenting security measures and offering a steadfast framework to mitigate the impact of vulnerabilities, thereby cultivating a more secure and resilient decentralized financial ecosystem.
Reference Source: SlowMist