
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Pine Protocol was exploited, resulting in a loss of assets worth 40 ETH.
On December 22, 2023, Pine Protocol was exploited across multiple transactions on the Ethereum Mainnet due to a smart contract vulnerability, which resulted in a loss of funds worth approximately 40 ETH.
Pine Protocol is a non-custodial, decentralized asset-backed lending protocol.
The root cause of the exploit is due to the shared pools between two different contracts in their protocol.
Step 1:
We attempt to analyze one of the attack transactions executed by the exploiter.
Step 2:
The exploiter took advantage of the flaw in their protocol's most recent update, in which both the old version and the new release of their contracts were sharing the same address.
Step 3:
This shared pool address between the old and new versions of the contracts resulted in the execution of fund transfers originating from the same address for different pools.
Step 4:
The attacker initially took NFT tokens as collateral to borrow assets from the new version of the pool.
They then took another flash loan from the old version of the pool and used the flash loan to repay their initial borrowed assets.
Step 5:
Due to the shared fund pools between the flash loan and NFT lending contract, the repayment was also recorded as a flag loan repayment.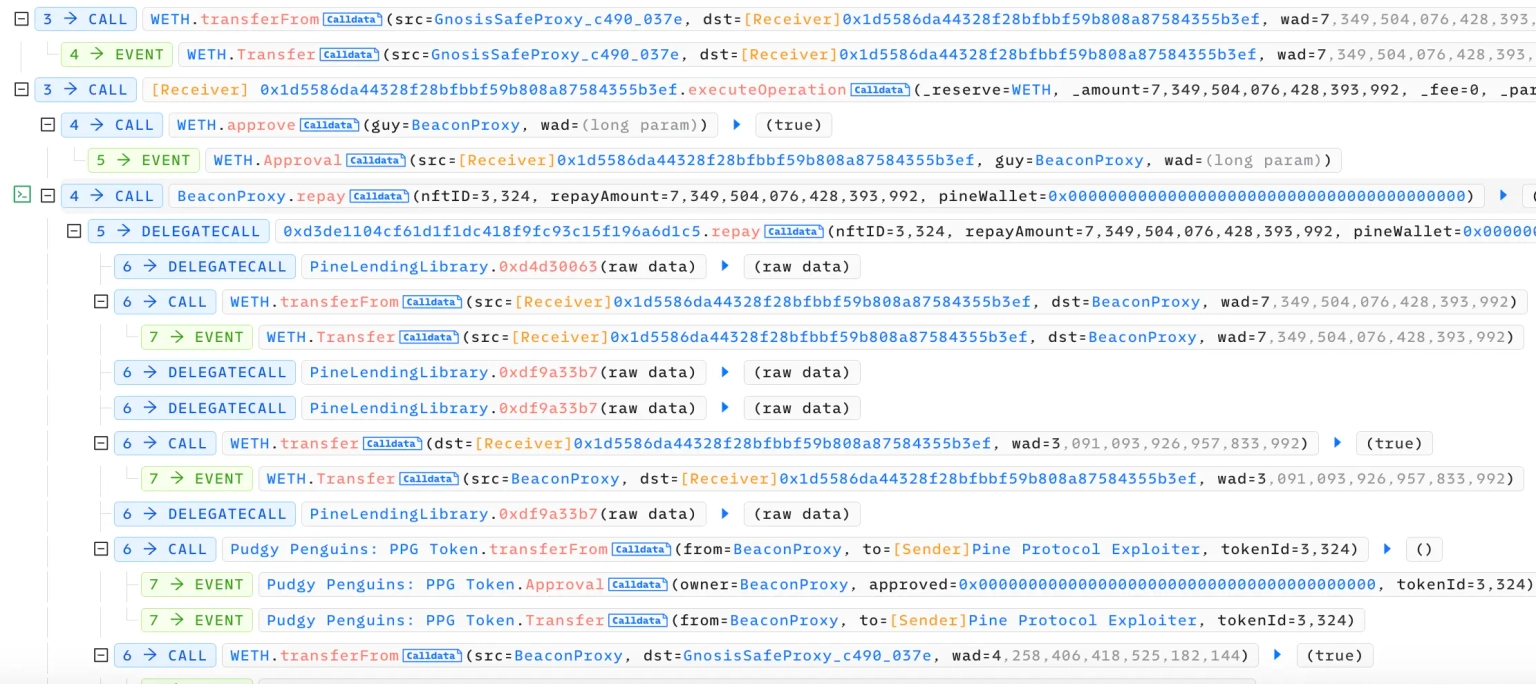
These steps were repeated multiple times to drain the assets from the vault.
Step 6:
The exploiter withdrew ETH from FixedFloat and ChangeNow and then laundered 20 ETH, worth $46,082, to Tornado Cash.
The hacker, after the successful exploitation of the Pine Protocol, sent an on-chain message by stating their intention to keep half of the stolen funds as a bounty. The hacker also advised the team to consolidate all WETH into a single wallet for security reasons, indicating that other wallets might be at risk.
The Pine Protocol team responded with gratitude for the hacker's willingness to communicate and return the funds. They requested the return of the remaining funds to their multi-signature wallet and extended an invitation for further discussion via email, expressing an interest in understanding more about the exploit.
In a subsequent message, the hacker elaborated on the technical aspects of the exploit. They highlighted that the vulnerability lay in the old contracts, which did not enforce `whitelistedIntermediaries` checks for the flash loan function, whereas the new contracts did. This revelation confirmed the team's suspicions about the vulnerability, leading to an acknowledgment of their oversight in not recognizing that a specific address was also part of the old contract system.
In the wake of the Pine Protocol exploit, addressing the immediate aftermath and implementing long-term safeguards are crucial steps.
Addressing the core issues that led to the exploit requires an extensive audit and revamping of the existing contract architecture. Ensuring that all contracts, irrespective of their version, implement robust conditional checks is fundamental to securing the flash loan functionality. Another critical measure is the segregation of pool addresses for different contract versions, thereby eliminating the risks associated with shared resources. Additionally, incorporating advanced security protocols and real-time monitoring systems will bolster the protocol’s ability to detect and respond to threats swiftly.
The long-term security of the Pine Protocol hinges on proactive and preventive measures. Establishing a continuous and rigorous external audit process is key to identifying and mitigating vulnerabilities. A structured framework for updates and migrations will ensure the secure and seamless integration of new contract versions. Engaging the broader DeFi community through bug bounty programs and open-source code reviews can tap into collective expertise to uncover potential security flaws. Additionally, regular training and awareness programs for both the team and the community are imperative to stay abreast of evolving security practices in the DeFi space.
Despite rigorous security measures, completely eliminating the risk of exploitation is an elusive target. This inherent uncertainty underscores the importance of extensive cover policies, similar to those offered by Neptune Mutual. By establishing a dedicated cover pool in our marketplace, the impacts of the exploit suffered by Pine Protocol could have been significantly mitigated. Our services provide users with reassurance, diminishing financial or digital asset losses due to smart contract vulnerabilities, courtesy of our distinctive parametric-based policies.
For those who choose our parametric cover policies, there's no requirement to present proof of loss to receive a payout. Once an incident is verified and resolved through our incident resolution system, the affected users can promptly claim their payouts.
Our marketplace spans several prominent blockchain networks, including Ethereum, Arbitrum, and the BNB chain, to deliver insurance coverage to a diverse array of DeFi users. Our participation in the ecosystem extends beyond protection, enhancing user confidence in the DeFi space.
Reference Source Cyvers