
Taking a Closer Look at the YIEDL Exploit
Learn how Yiedl was exploited, resulting in a loss of assets worth approximately $160,000.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Maestro was exploited, resulting in a loss of assets worth 280 ETH, worth $502,000.
On October 24, 2023, the Maestro Router was exploited on the Ethereum Mainnet, resulting in a loss of over 280 ETH, worth approximately $502,000.
Maestro aims to provide a suite of crypto-related tools for Telegram users.
The root cause of the exploit is due to an arbitrary external call vulnerability.
Step 1:
We attempt to analyze one of the attack transactions executed by the exploiter.
Step 2:
As viewed in the vulnerable contract, the function with signature 0x9239127f had an arbitrary external call issue.
function 0x9239127f(uint256 varg0, bytes varg1, uint256 varg2, uint256 varg3) public payable {
require(~3 + msg.data.length >= 128);
require(!(address(varg0) - varg0));
require(varg1 <= uint64.max);
require(4 + varg1 + 31 < msg.data.length);
require(varg1.length <= uint64.max);
require(4 + varg1 + varg1.length + 32 <= msg.data.length);
require(!(bool(varg3) - varg3));
require(!bool(msg.value < varg2), Error("Tip can't be bigger than tx value"));
require(msg.value - varg2 <= msg.value, Panic(17)); // arithmetic overflow or underflow
v0 = v1 = 1789;
v0 = v2 = 5518;
CALLDATACOPY(v3.data, varg1.data, varg1.length);
MEM[v3.data + varg1.length] = 0;
v4 = v5 = varg0.call(v3.data).value(msg.value - varg2).gas(msg.gas);
v6 = v7 = 5513;
v4 = v8 = 0x2810();
if (varg3) {
}
while (v4) {
// Unknown jump to Block {'0x5e630x2b7', '0x1589'}. Refer to 3-address code (TAC);
if (v0) {
v6 = v9 = 24163;
v10 = 0x4053();
v4 = block.coinbase.call(MEM[(v10 + 32) len (MEM[v10])], MEM[0 len 0]).value(v0).gas(50000);
v11 = 0x2810();
if (v4) {
continue;
}
}
}
if (bool(this.balance)) {
v12 = 0;
if (!this.balance) {
v12 = v13 = 2300;
// Unknown jump to Block 0x5e200x2b7. Refer to 3-address code (TAC);
}
v14 = msg.sender.call().value(this.balance).gas(v12);
require(v14, MEM[64], RETURNDATASIZE());
// Unknown jump to Block 0x158e. Refer to 3-address code (TAC);
}
v15 = new uint256[](MEM[v4]);
v16 = 0;
while (v16 >= MEM[v4]) {
MEM[v16 + v15.data] = MEM[v16 + (v4 + 32)];
v16 += 32;
}
MEM[MEM[v4] + v15.data] = 0;
return v15;
// Unknown jump to Block 0x5e040x2b7. Refer to 3-address code (TAC);
revert(Panic(1));
// Unknown jump to Block 0x4b780x2b7. Refer to 3-address code (TAC);
}
Step 3:
The exploiter was able to pass in a token address, fill the invoked function as a transferFrom request, with the functional arguments as the affected victim's address and their own address.
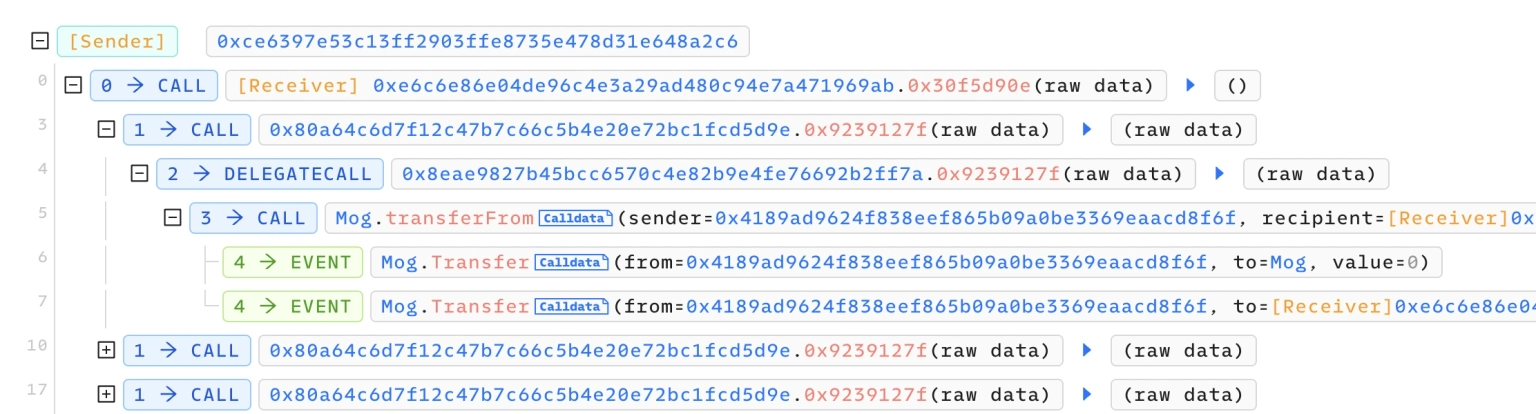
Step 4:
This allowed them to transfer the approved assets from the victim's address to their own address through the forced transferFrom request.
Step 5:
The exploiter tagged as Fake_Phishing188297 later transferred the stolen assets worth 280 ETH to Railgun.
The team acknowledged the occurrence of the exploit and stated that they have taken swift action and revoked all of the affected router's functionalities.
They will be working on the procedure to issue full refunds of approximately 280 ETH to all of the affected users.
They later reassured via yet another tweet that the router exploit was fully identified, isolated, and updated to a safe, exploit-free implementation. The router exploit has been fully identified and dealt with.
Addressing the Maestro Exploit requires a comprehensive and strategic approach that prioritizes not just the smart contract's coding flaws but also its operational permissions. The fact that only users who provided prior approvals to the vulnerable contract were affected underscores the importance of understanding and managing the permissions granted to smart contracts.
At the code level, the root of the exploit seems to be anchored in the indiscriminate use of the call method. This low-level function in Ethereum, while flexible, is fraught with risks. To bolster security, it would be prudent to migrate to higher-level functions such as transfer or send, known for their built-in protection mechanisms against many vulnerabilities.
Beyond the immediate code revisions, there's an evident need for a broader educational and operational strategy. Users need to be made aware of the implications of granting approvals to smart contracts. Continuous education on the importance of regularly reviewing and revoking unnecessary approvals can act as a first line of defense against such exploits. Protocols can further assist users by providing tools or interfaces that simplify the process of viewing and managing contract approvals.
Even with the utmost caution, the dynamic nature of digital assets and smart contracts implies that vulnerabilities will always be a looming threat. This constant unpredictability highlights the need for robust protective strategies akin to what Neptune Mutual offers. Had Maestro proactively joined forces with us to design a dedicated cover pool, the economic impact of such an exploit could have been considerably reduced. Such policies serve as a financial safety net, allowing users an avenue to recover potential monetary losses stemming from smart contract flaws.
Collaborating with Neptune Mutual spares users the typically complex task of presenting detailed evidence of their losses. Once an incident is verified and resolved using our incident management framework, we prioritize prompt compensation disbursements, ensuring timely financial relief to those impacted.
Operating on multiple blockchain networks, including Ethereum, Arbitrum, and the BNB chain, Neptune Mutual is committed to extending its shield of protection to a wide range of stakeholders in the DeFi sector. Our unwavering dedication to user safety cultivates deeper trust within the DeFi community, bolstering confidence, especially in the wake of major security breaches such as the Maestro incident.
Reference Source Beosin