
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how the SNK token was exploited, resulting in a loss of approximately $197,000.
On May 10, 2023, Snooker's Project SNK token on the BNB Chain was exploited, resulting in a loss of approximately $197,725.
The root cause of the vulnerability is a flawed invitation-reward mechanism.
Step 1:
We attempted to analyze the attack transaction executed by the exploiter.
Step 2:
The exploiter created multiple attack contracts on April 29 and deposited 10 SNK into each of them.
Step 3:
They then created a sub-contract and established an invitation relationship with the parent contract. The parent contract is among the addresses that were created on April 29.
Step 4:
The attacker is able to exploit the `bindParent` function of the SNKMiner contract in order to amplify their staking rewards, i.e., SNK tokens. This function binds one account as a child of the staking account.
Step 5:
The SNKMiner depends on the SNK balance of children of staking accounts in order to calculate the amount of rewards distributed to the staking accounts.
function _getMyChildersBalanceOf(address user) private view returns (uint256) {
address[] memory childers = inv.getInviterSuns(user);
uint256 totalBalances;
for (uint256 index = 0; index < childers.length; index++) {
totalBalances += balanceOf(childers[index]);
}
return totalBalances;
}Step 6:
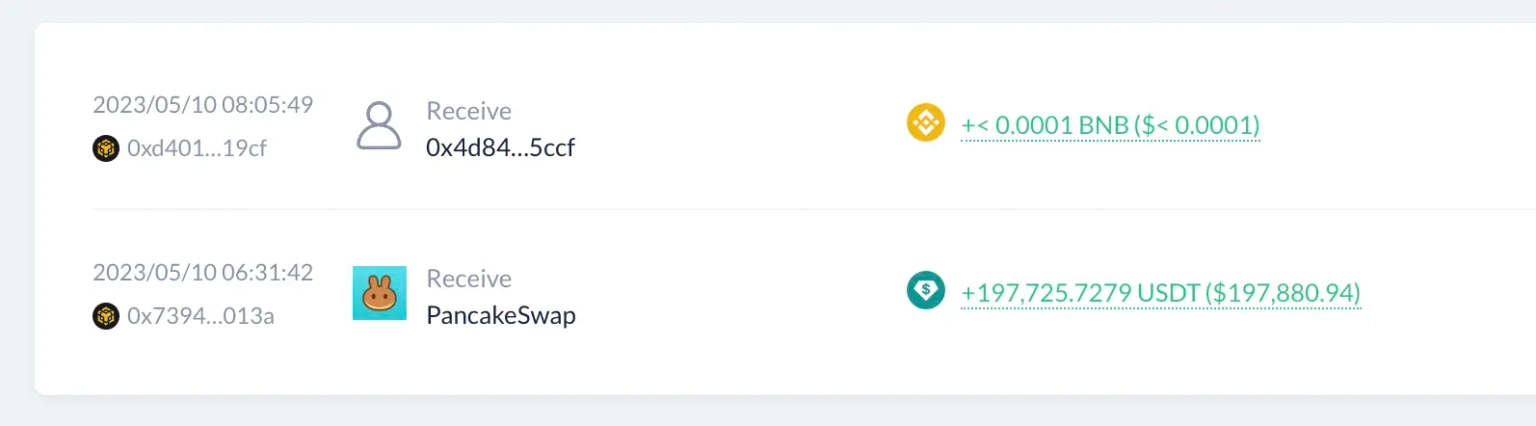
The attacker sends the tokens to the next child contract, repeats the same for his arbitrage opportunity, and takes away a large amount of profits.
Step 7:
The stolen funds from the exploit, worth $197,880, were sent to this address and have been held there since then, at the time of this writing.
In light of the incident, it is important for DeFi projects to focus on a few critical aspects of their systems.
A flawed reward mechanism can lead to massive losses, as in the case of Snooker's Project. Projects must ensure that their reward calculations are not exploitable. A thorough and rigorous test of the reward calculation logic can prevent such incidents.
Regular audits of the contract can also help identify potential flaws in the system. In this case, a thorough audit could have identified the potential vulnerability in the invitation-reward mechanism. Additionally, projects must have robust security measures in place to detect and mitigate such attacks. This can include automated systems to detect abnormal behavior in contract interactions.
We may not have prevented the occurrence of this hack, however the impact or aftermath of this attack could have been significantly reduced if the team associated with Snooker’s SNK token, had set up a dedicated cover pool in the Neptune Mutual marketplace. We offer coverage to users who have suffered a loss of funds or digital assets occurring as a result of smart contract vulnerabilities owing to our parametric policies.
Users who purchase the available parametric cover policies do not need to provide loss evidence in order to receive payouts. Payouts can be claimed as soon as an incident is resolved through the incident resolution system. At the moment, our marketplace is available on two popular blockchain networks, Ethereum, and Arbitrum.
Neptune Mutual's security team would also have evaluated the platform for DNS and web-based security, frontend and backend security, intrusion detection and prevention, and other security considerations.