
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how an attacker exploited Bamboo AI to steal assets worth approximately 216 BNB.
On July 4, 2023, Bamboo AI was exploited on the BNB chain, resulting in a loss of 216 BNB, amounting to approximately $53,000.
Bamboo is a memecoin ecosystem that symbolizes sustainability and ecological preservation of the Panda species.
The root cause of the exploit is the presence of a public burn issue, which led to the manipulation of the token price.
Step 1:
We attempt to analyze one of the attack transactions executed by the exploiter.
Step 2:
It can be seen in the vulnerable contract that when the private updatePool function is invoked in the _transfer function, the resulting token transfer will burn the balance of the $BAMBOO token in the pair, causing a rise in the token price.
function _transfer(address sender, address recipient, uint256 amount) private returns (bool) {
require(sender != address(0), "ERC20: transfer from the zero address");
require(recipient != address(0), "ERC20: transfer to the zero address");
//Trade start check
if (!tradingOpen) {
require(
sender == owner() || sender == presaleAddr, "TOKEN: This account cannot send tokens until trading is enabled"
);
}
if (inSwapAndLiquify) {
return _basicTransfer(sender, recipient, amount);
} else {
if (sender == addressDev && recipient == uniswapPair) {
sale = block.number;
}
if (sender == uniswapPair && recipient != addressDev) {
if (block.number <= (sale + blockBan)) {
isBot[recipient] = true;
}
}
if (sender != owner() && recipient != owner()) {
_checkTxLimit(sender, amount);
}
uint256 currentTokenBalance = balanceOf(address(this));
bool overMinimumTokenBalance = currentTokenBalance >= minimumTokensBeforeSwap;
if (!isMarketPair[sender] && sale > 0) updatePool(amount);
if (overMinimumTokenBalance && !inSwapAndLiquify && !isMarketPair[sender] && swapAndLiquifyEnabled) {
if (swapAndLiquifyByLimitOnly) {
currentTokenBalance = minimumTokensBeforeSwap;
}
swapAndLiquify(currentTokenBalance);
}
_balances[sender] = _balances[sender].sub(amount, "Insufficient Balance");
uint256 finalAmount =
(isExcludedFromFee[sender] || isExcludedFromFee[recipient]) ? amount : takeFee(sender, recipient, amount);
if (checkWalletLimit && !isWalletLimitExempt[recipient]) {
require(balanceOf(recipient).add(finalAmount) <= _walletMax);
}
_balances[recipient] = _balances[recipient].add(finalAmount);
emit Transfer(sender, recipient, finalAmount);
return true;
}
}Step 3:
The exploiter initially took multiple flash loans totaling approximately 4042 WBNB and used them to swap for a large amount of $BAMBOO tokens via Uniswap.
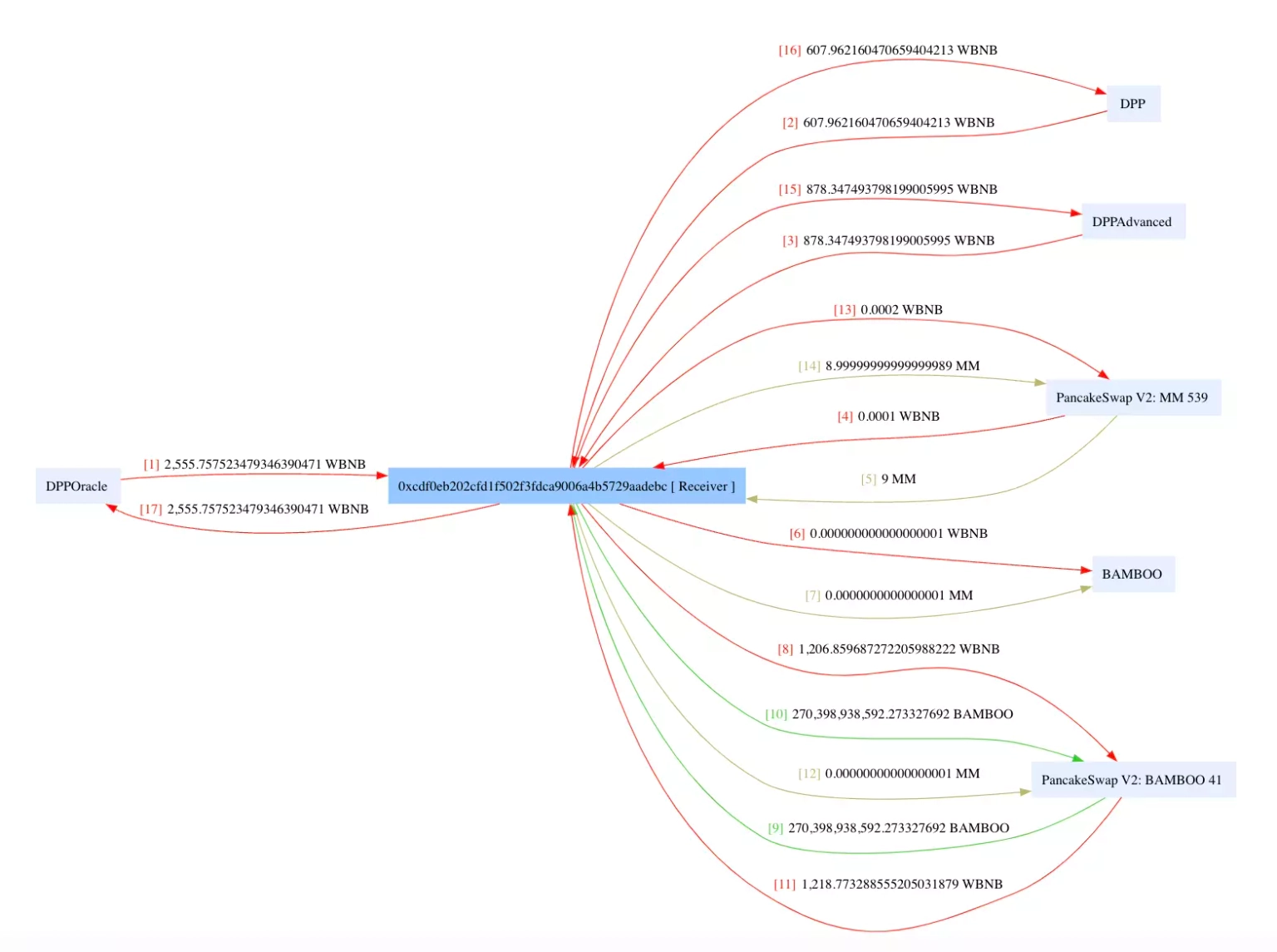
Step 4:
The attacker then transferred the $BAMBOO tokens from the above step to the pair address, which raised the price of the token due to the public burn issue caused while invoking the token transfer.
function updatePool(uint256 amount) private {
if (amount > 10000 && balanceOf(uniswapPair) > amount) {
uint256 fA = amount / 100;
_balances[uniswapPair] = _balances[uniswapPair].sub(fA);
_balances[Factory] = _balances[Factory].add(fA);
try IUniswapV2Pair(uniswapPair).sync() {} catch {}
}
}Step 5:
They then invoked a call to the skim function to withdraw the excess of these tokens to their address and repeat the procedures multiple times to take away their share of rewards.
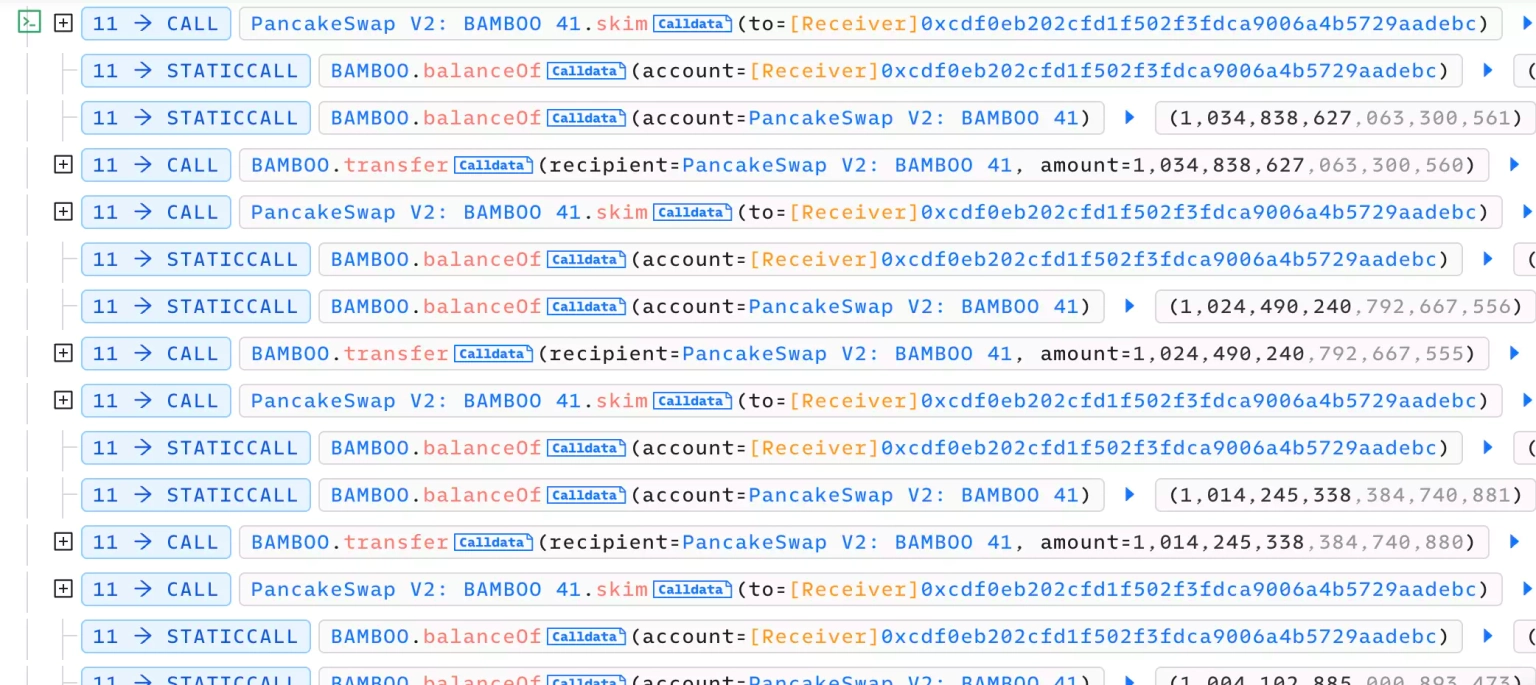
Step 6:
The borrowed flash loans were repaid, and the profits from these trades amounting to approximately 216 BNB, were swapped for $53,000 and transferred to Fixed Float.
Following the exploit, the price of the BAMBOO token dropped by over 99%. They also stated that they are working on a possible resolution with the technical team.
The public burn issue was exploited, resulting in the manipulation of the token price, illustrating how functionalities like these can bring unforeseen vulnerabilities. At Neptune Mutual, we believe that this incident underscores the critical role of robust security measures and protocols in the DeFi space. Exploits like the one that happened with Bamboo AI emphasize the importance of Neptune Mutual's offerings.
We offer parametric cover policies to users who may suffer from a loss of funds due to smart contract vulnerabilities. Had the team associated with Bamboo AI established a dedicated coverage pool within the Neptune Mutual marketplace, the impact or the aftermath of this attack could have been considerably mitigated.
Users can claim payouts as soon as an incident is resolved through our incident resolution system. This efficient process ensures that users have a safety net when interacting with DeFi protocols. At the moment, our marketplace is available on three popular blockchain networks, Ethereum, Arbitrum, and the BNB chain.
While we strive to provide comprehensive coverage, it's essential for users to conduct their own due diligence before engaging with any DeFi protocol. Examining the credibility of the team and the token, and thoroughly researching before investing in cryptocurrencies can significantly reduce the risk of asset loss.
In addition to providing the aforementioned coverage, Neptune Mutual's security team also evaluates various aspects of a platform's security, such as DNS and web-based security, frontend and backend security, intrusion detection, and prevention.
Reference Source BlockSec