
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how an attacker exploited Orion Protocol as a result of insufficient reentrancy protection.
On February 02, 2023, Orion Protocol was compromised as a result of a Reentrancy attack, leading to a loss of approximately $3 million in assets.
Orion Protocol is an open-source decentralized blockchain platform that serves as a liquidity aggregator for both centralized and decentralized exchanges.
The vulnerability was caused by insufficient reentrancy protection in their smart contract function, which allowed token transfers to be hijacked into reentering other contract functions in order to increase user balance without actually costing funds.
Step 1:
The exploiter used a self-destructive smart contract in order to deploy a fake token called ATK, which was then used to manipulate the Orion pools.
Step 2:
The protocol was attacked on both the Ethereum, and BNB Chain deployment pools.
Step 3:
We took a closer look at one of the attack transactions executed by the exploiter.
Step 4:
The Reentrancy issue existed in its core contract, specifically in the _doSwapTokens function, which led to the miscalculation of USDT balance.
Step 5:
To be specific, the miscalculated userAmountOut value in the _doSwapTokens function would turn to another argument amountIn, which would then be passed into LibExchange.creditUserAssets function, where assets were mistakenly updated.
Step 6:
The exploiter first deposited 0.5 USDC, received around $2.84 million USDT from Uniswap V2 Pair using flash swap, and swapped 0.0001 USDC through Origin Pool to receive USDT.
Step 7:
Approximately $2.8 million USDT were sent to the Router, which then manipulated the swaps on Orion pools to double the amount of USDT, then $5.6 million USDT were withdrawn from which ~ $2.8 million were sent back to the pool.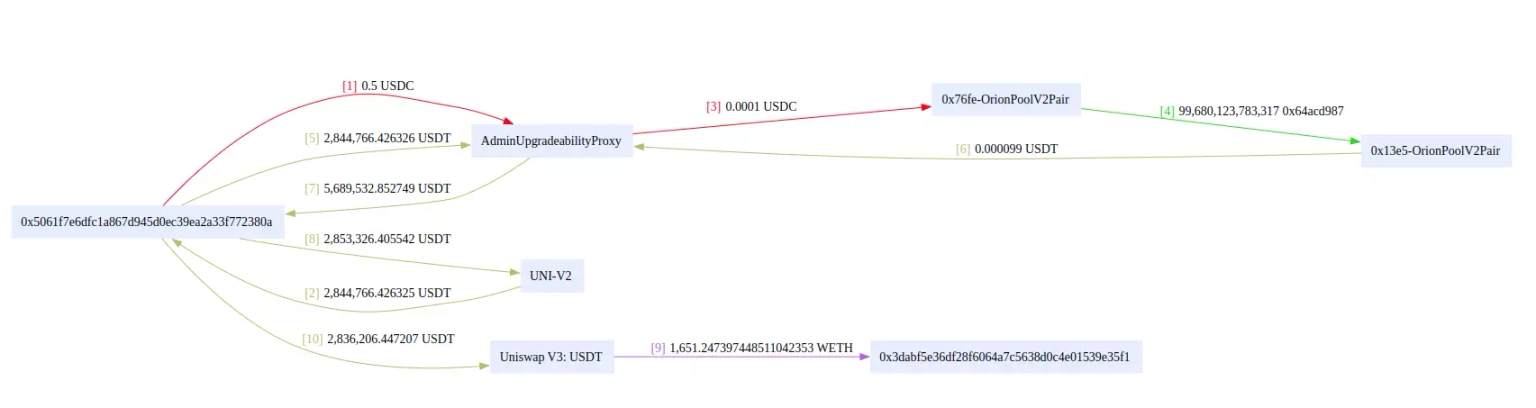
Step 8:
The proceeds generated approximately $2.8 million USDT, which was exchanged for 1651 ETH and sent to the attacker's wallet.
Step 9:
The hacker then funneled approximately 1100 ETH into Tornado Cash.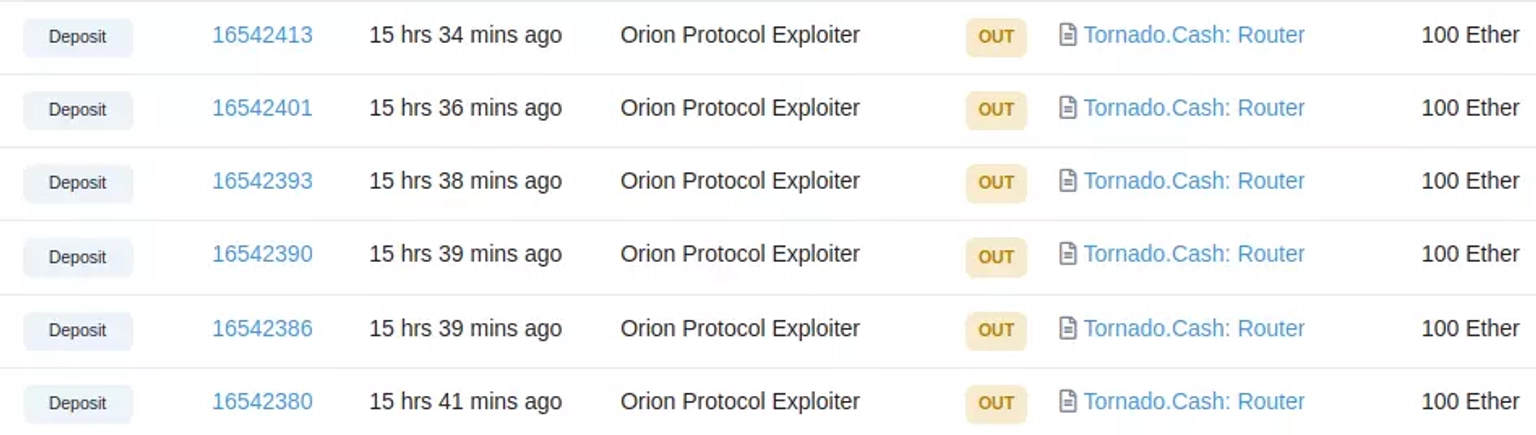
Step 10:
The other attack transaction on BNB Chain netted the exploiter approximately $191,434.
Following the incident, Alexey Koloskov, CEO of Origin Protocol, posted a lengthy thread on Twitter, claiming that they have reason to believe that the problem was not caused by shortcomings in their core protocol code, but rather by a vulnerability in mixing third-party libraries in one of the smart-contracts used by experimental and private brokers.
The exploited contract was used by one of their experimental brokers, with the company's treasury in the broker's account balance, thus all users funds are assured to remain intact.
The compromise of the Orion Protocol due to a reentrancy attack casts a somber shadow on the growing landscape of decentralized platforms. Serving as a liquidity aggregator for both centralized and decentralized exchanges, Orion Protocol’s vulnerability lay in the lack of reentrancy protection in its smart contract functions. This absence enabled attackers to cunningly maneuver token transfers, leading to a staggering loss of about $3 million.
Reentrancy attacks, unfortunately, have a notorious history in the blockchain space, with perhaps the most infamous one being the hack on The DAO that resulted in the theft of a monumental 3.6 million ETH. This attack vector typically hinges on manipulating a contract to call back into itself before the first call is finished. To effectively counteract such vulnerabilities, a series of measures need to be implemented.
A mutex, for instance, can prevent a contract from being reentered, ensuring functions within the smart contract are non-reentrant. Additionally, by adhering to the checks-effects-interactions design pattern, platforms can ensure all internal state changes are finalized before any external smart contract calls are initiated. It's paramount that these technical solutions are combined with rigorous security audits to ascertain and rectify potential vulnerabilities.
In such unpredictable scenarios, having a safety net becomes paramount, and this is where Neptune Mutual emerges as an invaluable ally. Had Orion Protocol had the foresight to establish a dedicated cover pool within our Neptune Mutual marketplace, the aftermath of this security breach could have been substantially mitigated. We, at Neptune Mutual, recognize the dynamic and intricate nature of smart contract vulnerabilities. By offering parametric policies, we endeavor to provide a security blanket to users who have unfortunately encountered losses due to these vulnerabilities. The essence of our policies is their user-centric design: users who opt for our coverage don't wade through tedious processes of providing loss evidence. Once an incident resolves, a payout can be directly claimed.
Our platform, conveniently accessible on leading blockchain networks like Ethereum and Arbitrum, is only a part of our comprehensive offering. Our security team, with their in-depth knowledge and expertise, would have provided a thorough assessment of Orion Protocol's ecosystem, examining every facet from DNS and web-based security to detailed backend fortifications. Our proactive approach to intrusion detection and prevention ensures vulnerabilities, such as the one exploited in the Orion Protocol, are recognized and addressed promptly.
Reference Sources PeckShield, BlockSec