
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Libertify was exploited on multiple chains, resulting in a loss of $452,000.
On July 11, 2023, Libertify was exploited on the Ethereum and Polygon chains, resulting in a total loss of approximately $452,000.
Libertify is a personalized AI risk management solution that protects investors from market swings to deliver higher risk-adjusted returns.
The root cause of the exploit is a lack of reentrancy protection on the deposit function of the LibertiVault contract, allowing the attacker to reenter the vulnerable function to take away more shares.
Step 1:
We attempt to analyze the attack transaction executed by this exploiter on both the Ethereum Mainnet and the Polygon chain.
Step 2:
The deposit function on the exploited contract lacked a reentrancy check, which allowed the hacker to mint more shares by re-entering this vulnerable routine.
function _deposit(uint256 assets, address receiver, bytes calldata data, uint256 nav)
private
returns (uint256 shares)
{
if (0 == assets) {
revert ZeroDepositError();
}
if (SANCTIONS_LIST.isSanctioned(_msgSender())) {
revert SanctionedError();
}
if (assets < minDeposit) {
revert MinDepositError();
}
if (assets > maxDeposit) {
revert MaxDepositError();
}
uint256 returnAmount = 0;
uint256 swapAmount = 0;
if (BASIS_POINT_MAX > invariant) {
swapAmount = assetsToToken1(assets);
returnAmount = userSwap(data, address(this), swapAmount, address(asset), address(other));
}
uint256 supply = totalSupply();
if (0 < supply) {
uint256 valueToken0 = getValueInNumeraire(asset, assets - swapAmount, MathUpgradeable.Rounding.Down);
uint256 valueToken1 = getValueInNumeraire(other, returnAmount, MathUpgradeable.Rounding.Down);
shares = supply.mulDiv(
valueToken0 + valueToken1, // Rounded down
nav, // Rounded up
MathUpgradeable.Rounding.Down
);
} else {
shares = INITIAL_SHARE;
}
uint256 feeAmount = shares.mulDiv(entryFee, BASIS_POINT_MAX, MathUpgradeable.Rounding.Down);
_mint(receiver, shares - feeAmount);
_mint(owner(), feeAmount); // mint(feeTo)
}Step 3:
The attacker reentered this function during an external call to mint their share before the totalSupply update; thus, this manipulation led them to take away more shares of rewards.
Step 4:
For the attack on the Polygon chain, the exploiter took a flash loan of 10 million USDT and called the LibertiVault contract's deposit function, which used a portion of the deposited tokens for swapping. The ratio of the tokens deposited in this transaction to the contract's balance before the deposit determines the number of newly minted tokens to be issued.
Step 5:
The attack contract is called during the swap procedure, during which the exploiter invokes a call to the deposit function for the first time, then reenters the function again to deposit a proportion of the USDT into the contract.
Step 6:
After the second reentrancy call, the contract mints tokens for the hacker based on the ratio of the earlier deposited USDT to the previous USDT balance of the contract.
Step 7:
The contract balance in the earlier step calculation should have been the previous balance plus the initial USDT balance deposited. However, due to reentrancy, the contract balance was obtained at the beginning, so the parameter did not change, and the original balance was used for calculation, thereby allowing for the exploit to occur.
Step 8:
The loss on Ethereum is approximately $162,000 and $288,000 on Polygon. A part of the stolen funds from the Polygon chain, worth approximately 123.8 ETH, has been bridged to Ethereum via CelerBridge, and a total of 210 ETH, worth $394,099 at the time of this writing, is held at this address on Ethereum.
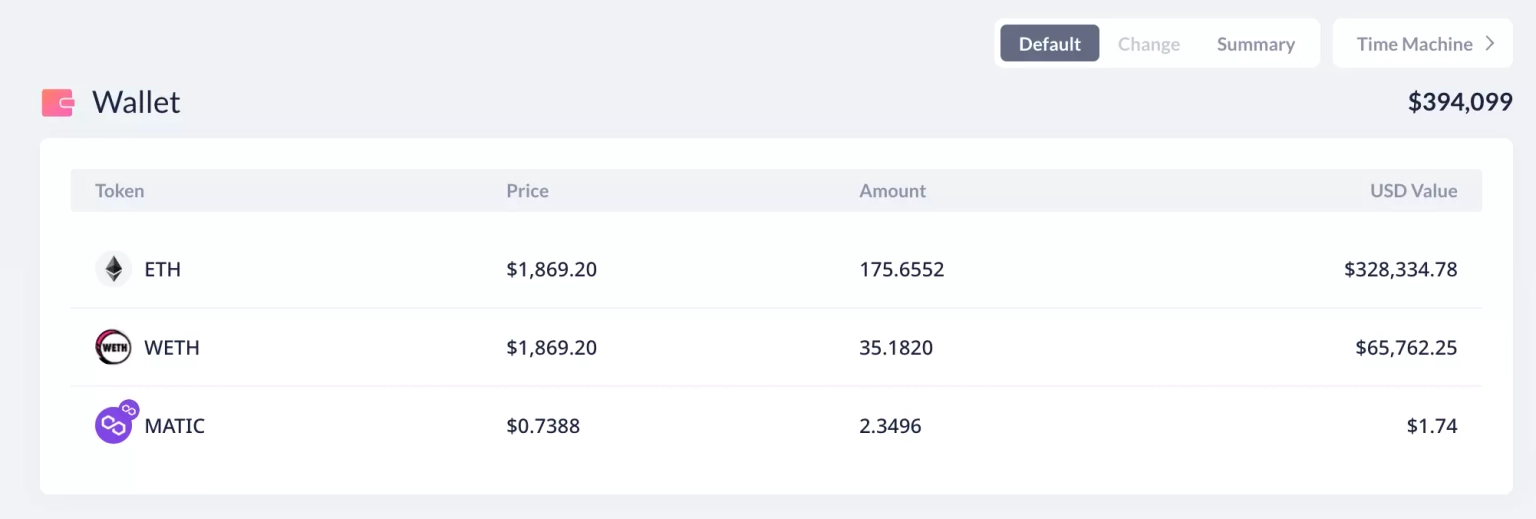
Following the incident, the team acknowledged the occurrence of the exploit and stated that the hack was performed on the test vault with funds from employees for 99%. The exploited funds include only $230 worth of user funds. According to them, the law enforcement process will begin at 6:00 p.m. UTC on July 11, in the absence of any funds being returned.
In light of the recent exploitation of Libertify, we at Neptune Mutual believe that our offering could have played a crucial role in mitigating the damaging impact of this attack. This situation underscores the urgency and necessity of robust security measures and meticulous testing in the DeFi protocols to effectively prevent such risks.
We offer coverage for users who have suffered losses due to smart contract vulnerabilities such as the one exploited in the LibertiVault contract. This exploit was caused by a lack of reentrancy protection, enabling the attacker to re-enter the deposit function to withdraw more shares than they should have been allowed.
A tailored solution to prevent future reentrancy attacks would be to implement a non-reentrant mutex in the deposit function. This would make the function non-reentrant, preventing the kind of attack that Libertify suffered. Also, the design pattern "checks-effects-interactions" can be used to ensure that all state changes take place before calling external smart contracts, minimizing the potential for reentrancy vulnerabilities.
However, even with these precautions, it is important to understand that vulnerabilities might still go undetected. Neptune Mutual understands this reality and provides a solution to reduce the impact of such unfortunate incidents.
By establishing a dedicated cover pool with Neptune Mutual, Libertify could have offered its users an immediate recovery path from the exploit. Our innovative parametric policies allow users to claim their losses without the need to provide detailed proof of loss. Once the incident is confirmed and resolved through our incident resolution system, payouts can be claimed immediately.
Our marketplace operates on several popular blockchain networks, including Ethereum, Arbitrum, and the BNB chain, allowing us to provide coverage to a diverse array of DeFi users.
In addition, Neptune Mutual's security team would have assessed the Libertify platform for a range of potential vulnerabilities, including DNS and web-based security, frontend and backend security, and intrusion detection and prevention. These comprehensive evaluations can provide valuable insights into how a platform can further enhance its security.
Reference Source PeckShield