
How Was NGFS Token Exploited?
Learn how NGFS Token was exploited, resulting in a loss of assets worth approximately $191,000.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Balancer was exploited, resulting in a loss of assets worth over $238,000.
On September 20, 2023, Balancer was the target of a BGP hijacking attack, which resulted in a loss of funds worth over $238,000.
Balancer is an automated market-making protocol.
The root of the exploit seemed to stem from a BGP hijacking incident, which redirected legitimate network traffic through malicious pathways. This resulted in unauthorized access and subsequent loss of funds.
Step 1:
We analyzed the A-records (IPv4) and the AAAA-records (IPv6) of the domain `balancer.fi`. Below are the generated results.
| A | Prefix | ASN |
| 172.67.203.244 | 172.67.192.0/20 | AS13335 - Cloudflare, Inc. |
| 104.21.37.47 | 104.21.32.0/20 | AS13335 - Cloudflare, Inc. |
Step 2:
Both of these IPs, `104.21.37.47` and '172.67.203.244', belong to the BGP AS number AS13335, which is associated with CloudFlare.
Step 3:
According to the BGP Origin Hijack-17957 data by Cloudflare, the Autonomous System Numbers (ASN) in the list of victims include AS13335, to which balancer.fi belongs.
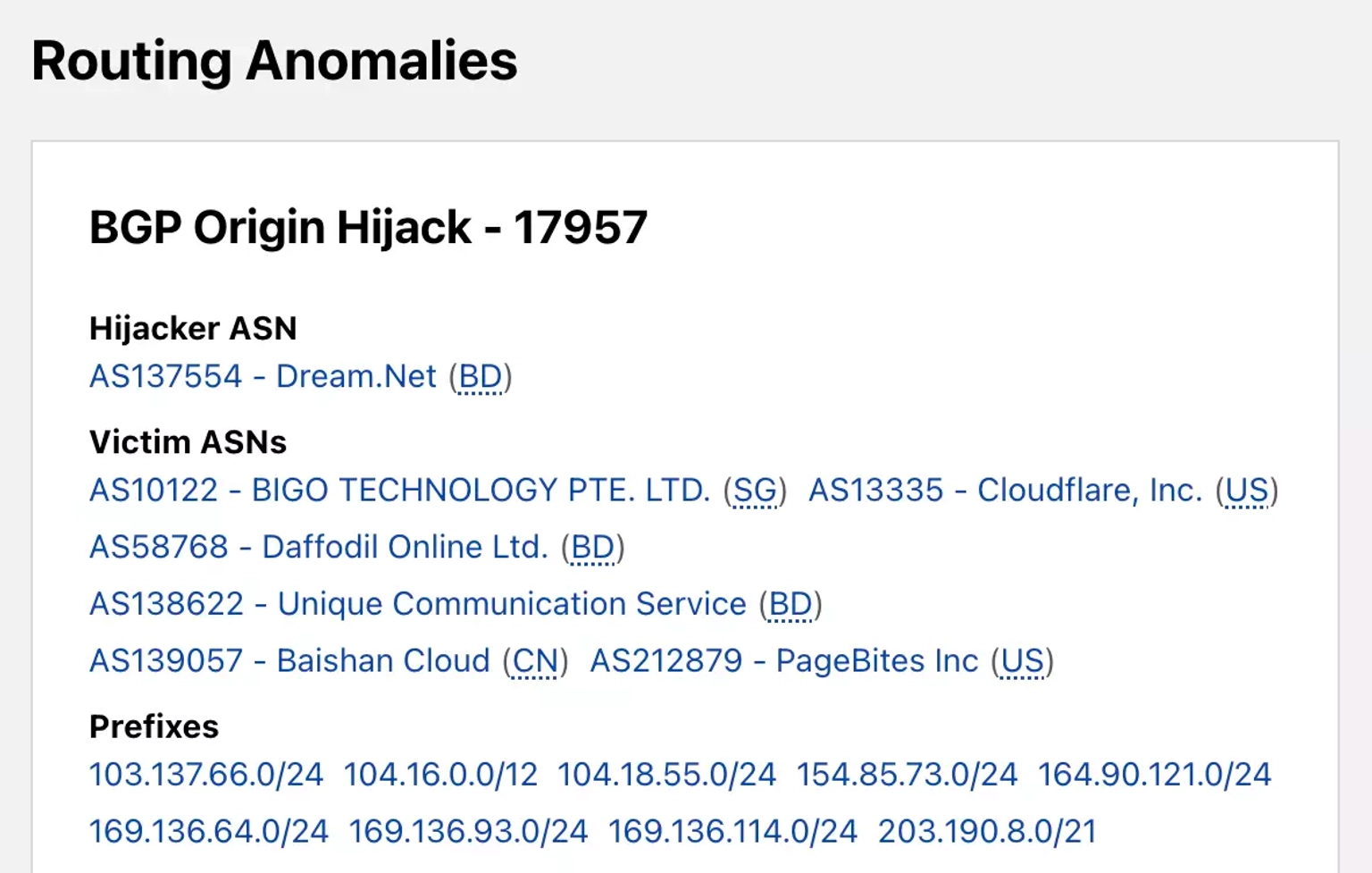
Step 4:
The SSL certificate of the domain associated with `balancer.fi` shows that it was modified on September 19, 2023, at 21:58 GMT. This certificate is likely to be controlled by the attacker.
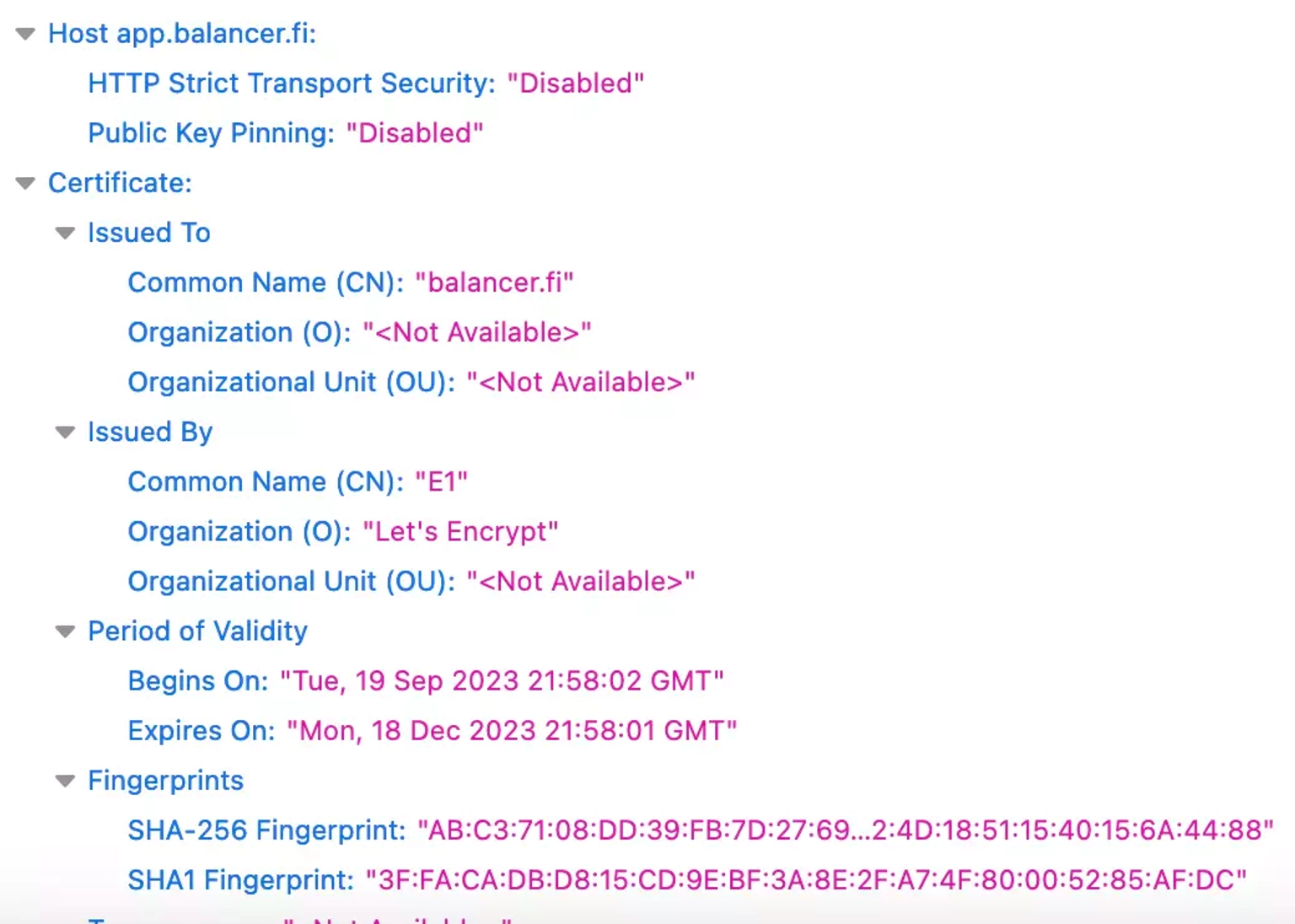
Step 5:
Following the community alert, Cloudflare has listed the site `https://app.balancer.fi` as phishing. Metamask has also updated their list of phishing sites to include all the affected sites relating to this incident.
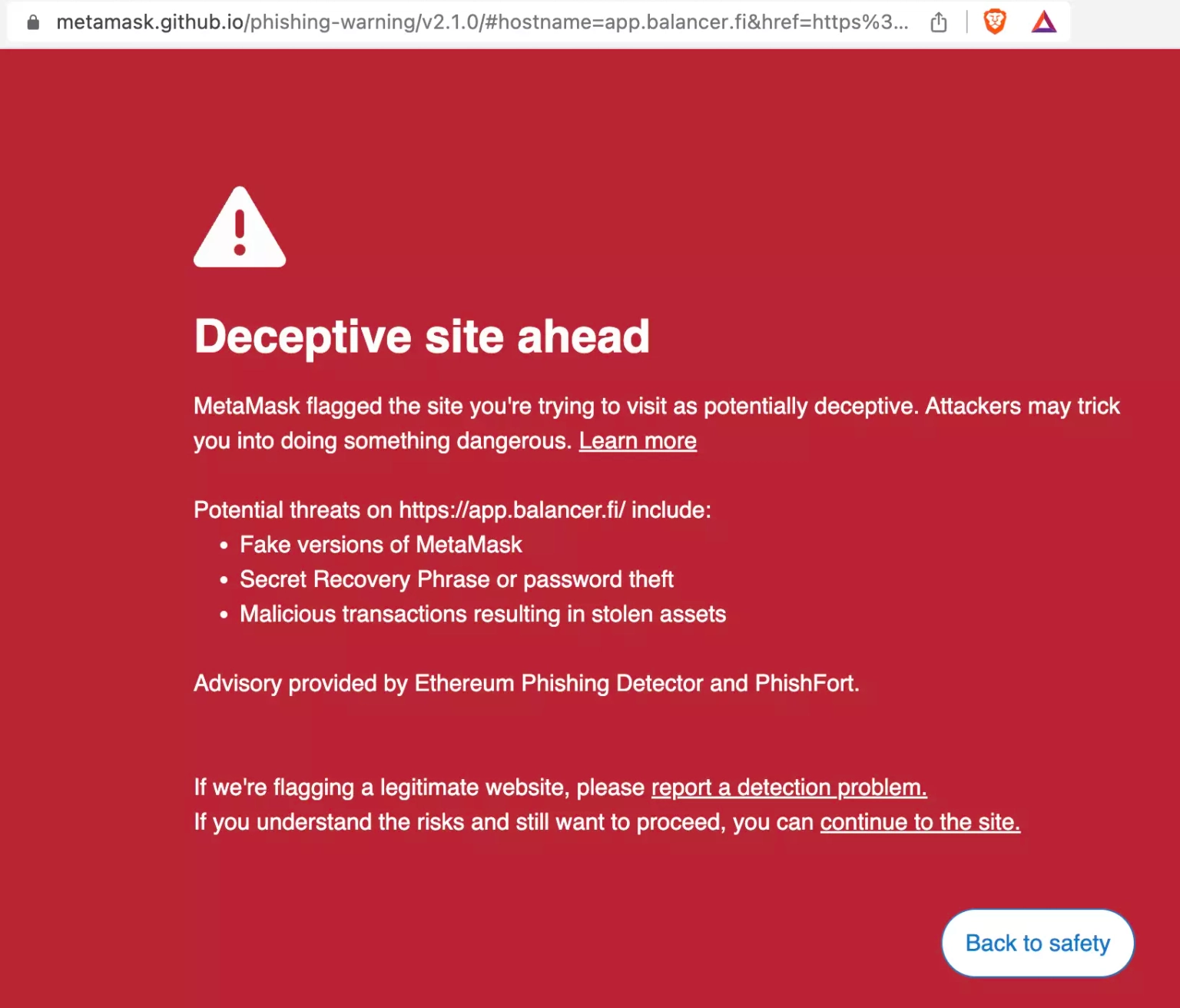
Step 6:
There exists a malicious JavaScript payload on the frontend of `http://app.balancer.fi`.
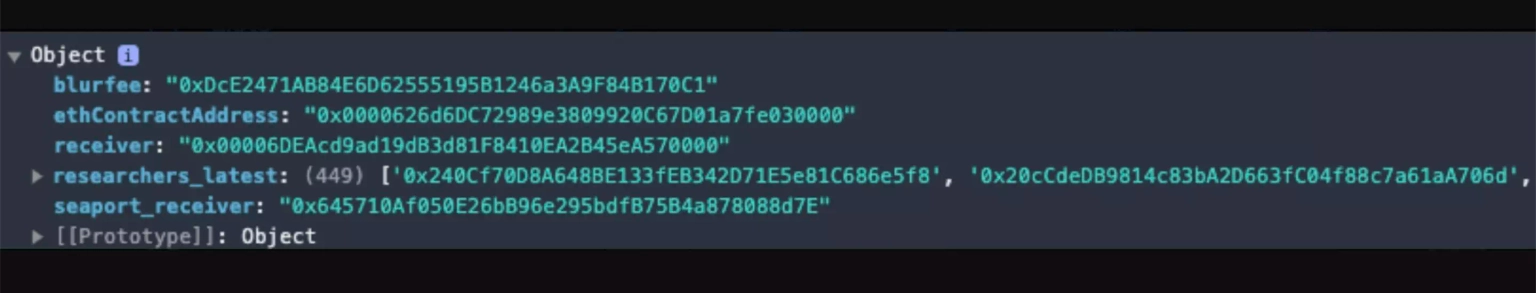
Step 7:
Once users connect their wallet, this compromised site will automatically check their balance and authorize phishing and other actions to drain funds from the associated wallet.
Step 8:
Once the confirmation is established, the malicious payload redirects customer funds to the attacker's addresses below.
0x645710Af050E26bB96e295bdfB75B4a878088d7E
0x00006DEAcd9ad19dB3d81F8410EA2B45eA570000
0x0000626d6dc72989e3809920c67d01a7fe030000
Step 9:
On the Avalanche chain, the exploiter also transferred approximately 61.349 WETH.e to this address.
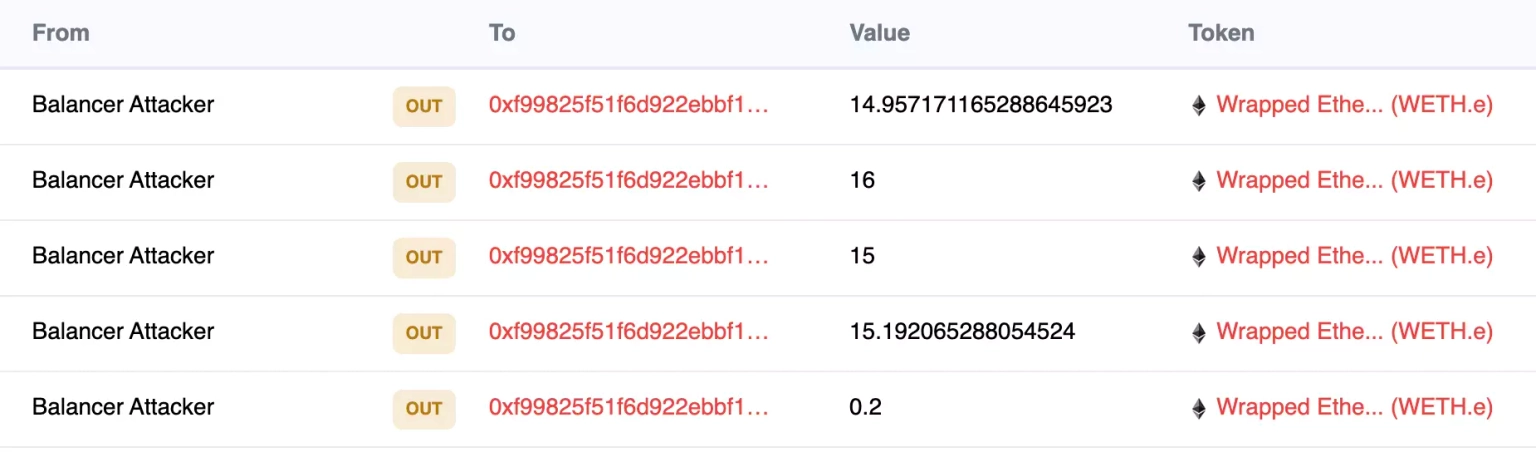
Following the incident, the team issued a community alert stating that their frontend is under attack and urging users to refrain from interacting with their UI until further notice.
They further stated that the Balancer DAO was actively addressing the attack by working with all relevant parties to ensure the full recovery of their platform.
A later tweet by the team revealed that the actual cause of the incident was a social engineering attack on EuroDNS, the domain registrar used for `.fi` TLDs. Following this, they also stated that they are exploring the options to deprecate the `.fi` TLD in order to move to a more secure registrar.
Balancer's unfortunate BGP hijacking incident points to multiple areas of concern that must be addressed to avoid such security compromises in the future. Implementing RPKI (Resource Public Key Infrastructure) can ensure that IP address blocks and ASN registrations can be validated cryptographically. With RPKI, even if someone announces a hijacked BGP route, the invalidity of the route is evident, and it won't be accepted. BGPsec, an extension to BGP, also offers security for the path of BGP ASes. Using BGPsec would ensure that the path of autonomous system numbers (ASN) in a BGP update message is valid.
Given that the SSL certificate of balancer.fi was modified during the attack, an organization can also use automated tools and services to monitor and send alerts for any changes or expirations of the SSL certificates. By monitoring Certificate Transparency (CT) logs, organizations can detect unauthorized certificates issued for their domains.
Utilizing secure DNS servers that encrypt DNS traffic is another potential defense against such hijacking attacks. This can aid in preventing traffic from being intercepted and forwarded to malicious servers by attackers. Although securing BGP could be challenging, employing security practices like DNSSEC and HSTS would have reduced the impact of this kind of attack. When DNSSEC is enabled, fraudulent DNS entries are rejected by DNS resolvers. With HSTS enabled, browsers shield users from self-signed certificates.
Web applications remain the frontline for user interaction, making them prime targets. By defining a strict Content Security Policy (CSP), websites can deter malicious payloads from being executed. It ensures that only scripts from trusted sources run, adding an extra layer of defense. Additionally, Subresource Integrity (SRI) can be a game-changer. which verifies that external resources loaded by web documents against predefined cryptographic hashes to ensure they are unaltered.
Reference Source SlowMist