
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how an attacker utilized a flash loan attack to manipulate the price of Upswing Finance.
On January 17, 2023, a flash loan attack on Upswing Finance resulted in the loss of approximately 22.58 ETH, worth $35,800.
The domain for Upswing Finance cannot resolve to an IP address, and their Twitter account provides no project-specific details.
The vulnerability stems as a result of a flash loan attack, owing to the design flaw of UPStkn token, which allowed the hacker to manipulate its price in the liquidity pool.
Step 1:
We took a closer look at the attack transaction executed by the exploiter, and the attack contract deployed by them.
Step 2:
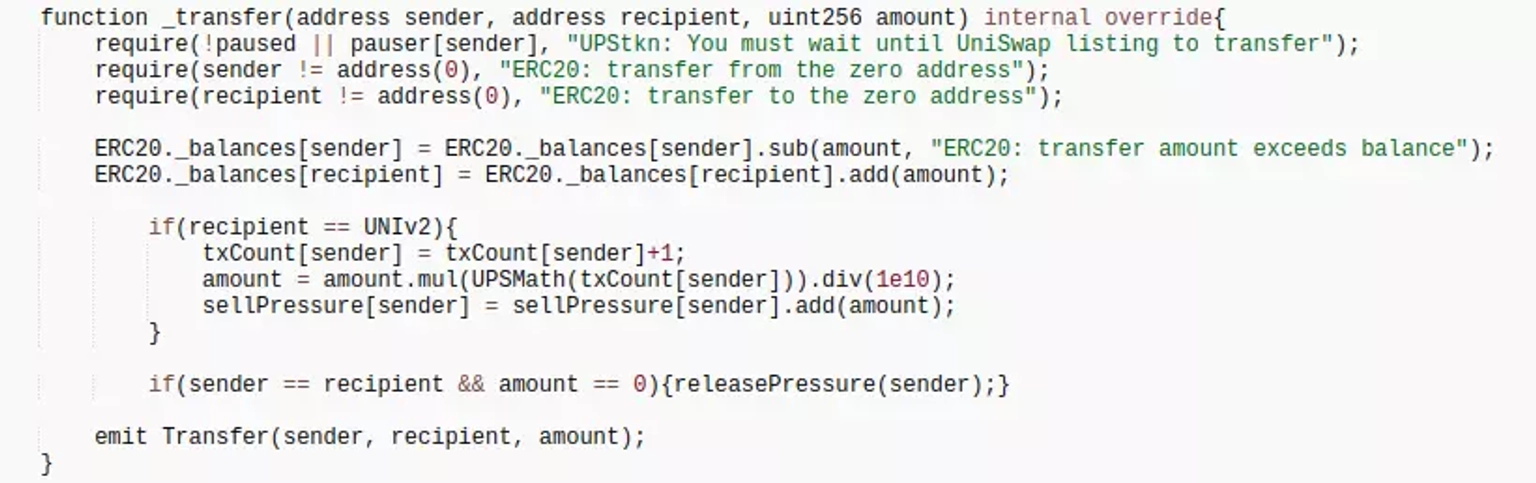
According to the logic in the _transfer function of the contract, $UPStkn token would be accumulated when transferring, specifically if the receiving address is a pair address.
Step 3:
If the receiver is a UNI pool, the amount of $UPStkn token in the pool will be burned, which will alter the pool pricing and provide the hacker an opportunity to make profit from it.
Step 4:
The attacker utilized about 18 swaps to lift $UPStkn token selling pressure, exchanging 1.31 ETH for 136,299.97 UPStkn tokens.
Step 5:
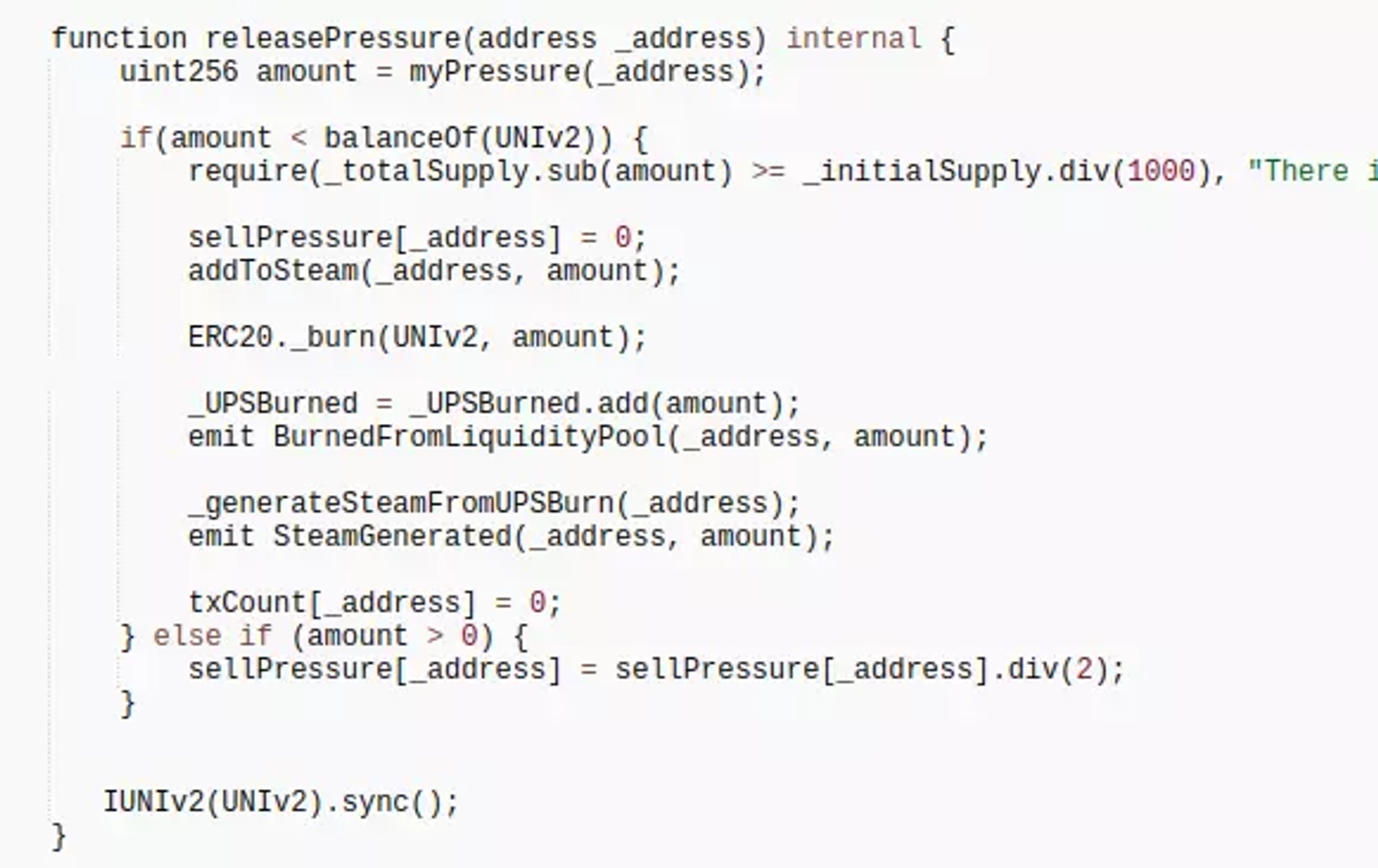
The attacker transferred 0 UPStkn tokens to himself to trigger the internal function releasePressure, which burned the LP's 573,300.39 UPStkn tokens in order to increase the price of UPStkn.
Step 6:
The attacker then sold the earlier obtained 136,299.97 UPStkn for a profit of 22.589 ETH after manipulating the token price.
The project appears to be dormant since October 2020. The circumstance appears sketchy, with few updates on their Twitter account and limited availability of members on Telegram. There has been no acknowledgement of the incident by the team.
The flash loan attack that unfolded against Upswing Finance underscored the vulnerability that persists within the DeFi landscape. This time, an approximate loss of 22.58 ETH, amounting to $35,800, was sustained due to a design flaw in the UPStkn token, allowing an exploiter to manipulate its price within the liquidity pool.
Unfortunately, the project's lack of presence raises further concerns. With their domain failing to resolve to an IP address and minimal project-specific information on their Twitter account, the circumstances surrounding Upswing Finance appear dubious. Despite this, the attack transaction's execution and the deployment of the exploit contract serve as a stark reminder of the vulnerabilities prevalent in this space.
This breach stemmed from an intricate set of steps. The attacker carefully orchestrated the manipulation of the UPStkn token's price, leading to the accumulation of tokens and subsequent burning. Through multiple swaps and well-calculated moves, the attacker managed to distort the token price to their advantage, ultimately profiting at the expense of the protocol.
To curb the potential for such attacks involving Oracle price manipulation, reliance on robust data providers like ChainLink could be a prudent strategy. This reinforces the need for robust data integrity as a line of defense against price manipulation, thereby enhancing the security landscape of the DeFi sector.
In the aftermath, the project's apparent dormancy raises questions about its responsiveness and accountability. With limited updates and engagement on social platforms, the absence of any acknowledgment of the incident from the team raises concerns about the project's legitimacy and user protection.
Neptune Mutual stands as a beacon of security in the DeFi realm. In scenarios where protocols suffer a loss due to smart contract vulnerabilities, our dedicated cover pool within the Neptune Mutual marketplace could have provided a crucial safety net. Our parametric cover policies enable affected parties to claim payouts efficiently without requiring exhaustive loss evidence once an incident is resolved through our governance system.
Our holistic security evaluation ensures that platforms are fortified against potential threats. While a protocol audit is a vital step, relying solely on one audit partner might not offer a comprehensive review of vulnerabilities. Collaborating with multiple partners ensures a thorough security assessment that bolsters user asset safety and a comprehensive understanding of the protocol's security.
Reference Source QuillAudits