
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Uwerx Network was exploited, resulting in a loss of 174.78 ETH, worth $324,000.
On August 2, 2023, Uwerx Network was exploited on the Ethereum Mainnet, which resulted in a loss of 174.78 ETH, worth approximately $324,000.
Uwerx aims to revolutionize and reconceptualize the freelance industry by launching a blockchain-powered freelance platform.
The root cause of the exploit is price manipulation caused by a vulnerable function that burns off 1% of the initial transfer amount.
Step 1:
We attempt to analyze the attack transaction executed by the exploiter.
Step 2:
On the vulnerable Uwerx contract, there is a vulnerable `_transfer` function that burns an extra 1% of the UWERX token if the `_to` address is the `uniswapPoolAddress` variable.
function _transfer(address from, address to, uint256 amount) internal virtual {
require(from != address(0), "ERC20: transfer from the zero address");
require(to != address(0), "ERC20: transfer to the zero address");
_beforeTokenTransfer(from, to, amount);
uint256 fromBalance = _balances[from];
require(fromBalance >= amount, "ERC20: transfer amount exceeds balance");
unchecked {
_balances[from] = fromBalance - amount;
// Overflow not possible: the sum of all balances is capped by totalSupply, and the sum is preserved by
// decrementing then incrementing.
_balances[to] += amount;
}
if (to == uniswapPoolAddress) {
uint256 userTransferAmount = (amount * 97) / 100;
uint256 marketingAmount = (amount * 2) / 100;
uint256 burnAmount = amount - userTransferAmount - marketingAmount;
emit Transfer(from, to, userTransferAmount);
emit Transfer(from, marketingWalletAddress, marketingAmount);
_burn(from, burnAmount);
} else {
emit Transfer(from, to, amount);
}
_afterTokenTransfer(from, to, amount);
}Step 3:
The UWERX contract has a private address variable, `uniswapPoolAddress`, set as:
address private uniswapPoolAddress = 0x0000000000000000000000000000000000000001;As per the condition in the `_transfer` routine, when the receiving address is set to this `uniswapPoolAddress` address, the protocol first modifies the balance of the sender and then again invokes a call to the `_burn` function, thereby burning off 1% of the initial amount.
function _burn(address account, uint256 amount) internal virtual {
require(account != address(0), "ERC20: burn from the zero address");
_beforeTokenTransfer(account, address(0), amount);
uint256 accountBalance = _balances[account];
require(accountBalance >= amount, "ERC20: burn amount exceeds balance");
unchecked {
_balances[account] = accountBalance - amount;
// Overflow not possible: amount <= accountBalance <= totalSupply.
_totalSupply -= amount;
}
emit Transfer(account, address(0), amount);
_afterTokenTransfer(account, address(0), amount);
}Step 4:
The exploiter initially took a flash loan of 20,000 ETH, swapped them for roughly 5,053,637 WERX, and then transferred 4,429,817 WERX back to the pool, creating an imbalance.
Step 5:
The attacker then called the skim function of the UniswapV2 pool after consuming a large number of WERX tokens, and then called the sync function to maliciously inflate the price of the token.
Step 6:
After this price manipulation, the tokens were swapped back to obtain ETH. The borrowed flash loan was repaid, and the profit from these trades was roughly 174 ETH, which is still held at this address.
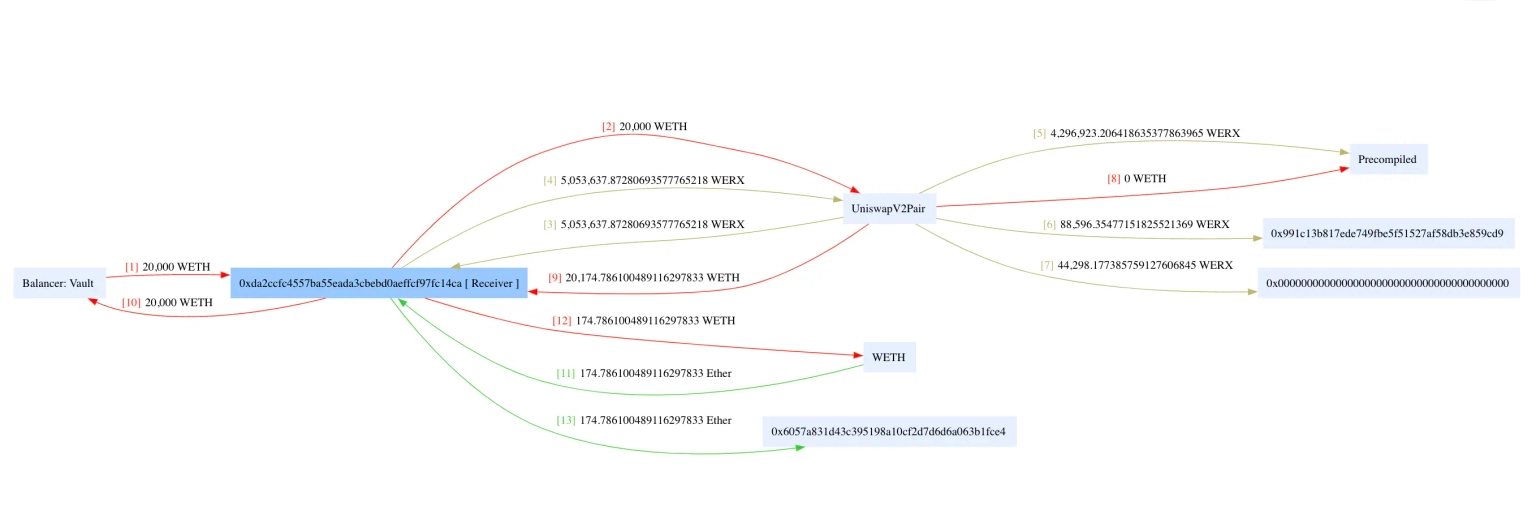 Image: Funds flow for Uwerx Exploit. Courtesy of Phalcon by BlockSec
Image: Funds flow for Uwerx Exploit. Courtesy of Phalcon by BlockSec
The team completed their token presale on August 1, 2023. After the occurrence of the exploit, they stated that the team is looking into the incident with urgency and will be making an official announcement. Apparently, the team will be relaunching WERX using the liquidity funds reserved for buy-backs.
They also sent a message to the exploiter to return 80% of the exploited funds while keeping the other 20% as a white-hat bounty reward. They have also shared a detailed report of this incident and their plans moving forward. The price of the underlying token dropped by 100% following the exploit.
The exploit described is fundamentally rooted in the Uwerx Network's vulnerable `_transfer` function and the implications of its logic when transacting with the designated `uniswapPoolAddress`. While the tokenomics design appears to have been set with the intent to benefit the project by burning and redirecting funds for marketing, the vulnerability was exploited to create imbalances and manipulate prices.
To begin with, the protocol’s design of burning tokens when transferred to a specific address is inherently problematic. Manipulating token prices on decentralized exchanges, especially when the address is known, is not particularly challenging for skilled individuals, especially when combined with flash loans.
An equitable system shouldn't apply arbitrary transfer rules based on the recipient's address, especially one that's hardcoded. Any form of redistribution or burning can be better controlled with a separate function that the team invokes manually or via automated strategies with clear, robust logic.
As we journey through the decentralized landscape, it's paramount to remember that while the world of blockchain and cryptocurrency offers exciting possibilities, it is also rife with complexities and challenges. To navigate these waters, due diligence is non-negotiable. Knowing the credibility of the team behind a project is pivotal. Investors need to research the team’s past ventures, their reputation in the community, and their transparency in communication. A genuine project will typically be forthright about its goals, progress, and setbacks.
Understanding the project's use case is equally crucial. In a market saturated with tokens and projects, the ones with real-world applications, clear utility, and a vision for the future are the ones most likely to succeed. It's essential to distinguish between genuine innovation and mere market hype.
While these preventative measures are essential, they may not entirely preclude the possibility of an attack. It's here that solutions like ours at Neptune Mutual play an integral role. If the team associated with Uwerx had established a dedicated cover pool with us prior to the exploit, the aftermath of the incident could have been notably alleviated.
Neptune Mutual offers coverage to users who have sustained losses due to vulnerabilities in smart contracts, underpinning our solution with pioneering parametric policies. With our coverage policies, users don't need to go through the cumbersome process of proving their losses. Following the confirmation and resolution of an incident through our comprehensive incident resolution framework, users can claim their payouts promptly.
Our marketplace operates on numerous popular blockchain networks, including Ethereum, Arbitrum, and the BNB chain. This extensive reach allows us to serve a broad spectrum of DeFi users, offering protection from potential vulnerabilities and enhancing their faith in the ecosystem.
Reference Source BlockSec