Understanding the XBridge Exploit
Learn how XBridge was exploited, resulting in a loss of assets worth approximately $1.44 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Earning Farm was exploited, resulting in a loss of assets worth $528,000.
On August 9, 2023, Earning Farm was exploited on the Ethereum Mainnet, which resulted in a loss of funds worth approximately $528,000.
Earning Farm aims to provide user-friendly investment tools for the mass population to enjoy the innovation of DeFi.
The root cause of the exploit is a logic error that allowed the operations to reenter the vulnerable contracts.
Step 1:
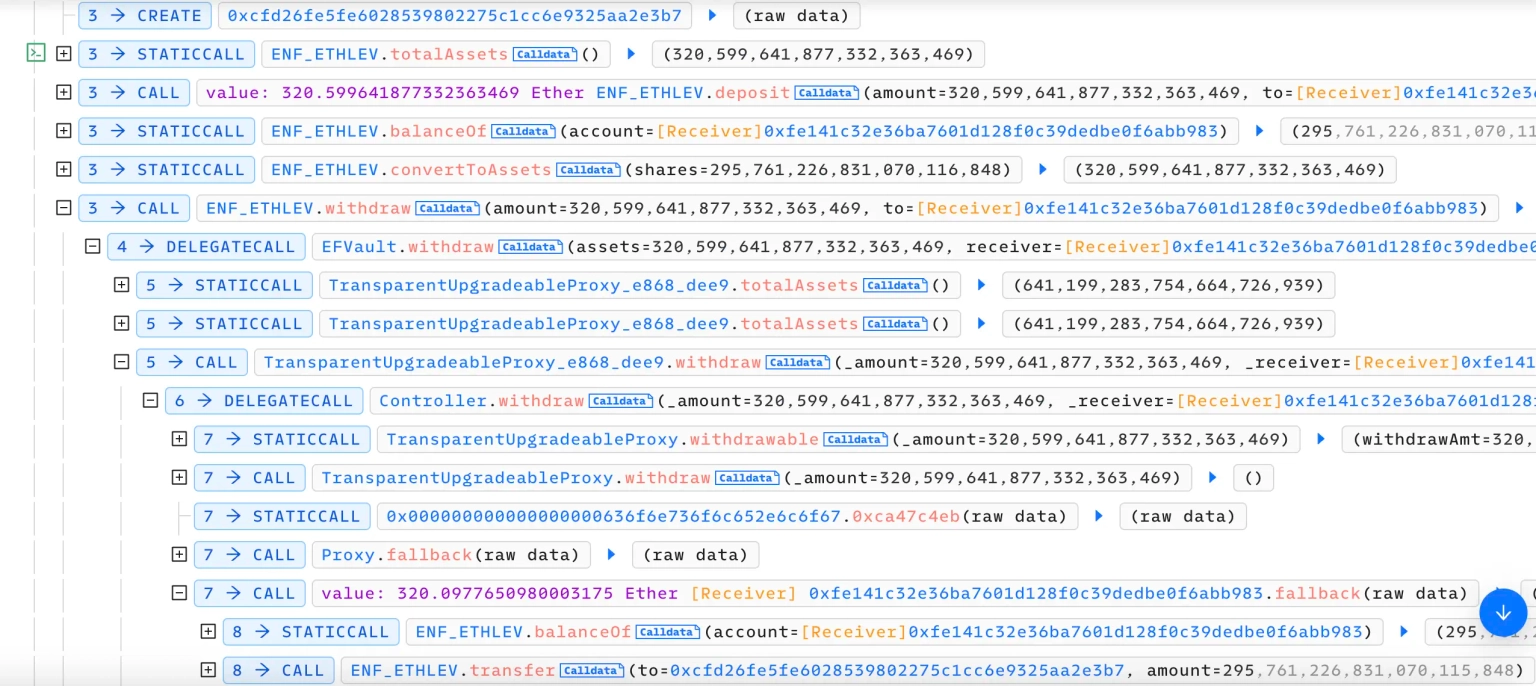
We attempt to analyze one of the attack transactions executed by the exploiter.
Step 2:
The vulnerable `withdraw` function of the EFVault contract allowed anyone to burn their `ENF_ETHLEV` balance if it was less than the expected amount of shares.
function withdraw(uint256 assets, address receiver) public virtual nonReentrant unPaused returns (uint256 shares) {
require(assets != 0, "ZERO_ASSETS");
require(assets <= maxWithdraw, "EXCEED_ONE_TIME_MAX_WITHDRAW");
// Total Assets amount until now
uint256 totalDeposit = convertToAssets(balanceOf(msg.sender));
require(assets <= totalDeposit, "EXCEED_TOTAL_DEPOSIT");
// Calculate share amount to be burnt
shares = (totalSupply() * assets) / totalAssets();
// Calls Withdraw function on controller
(uint256 withdrawn, uint256 fee) = IController(controller).withdraw(assets, receiver);
require(withdrawn > 0, "INVALID_WITHDRAWN_SHARES");
// Shares could exceed balance of caller
if (balanceOf(msg.sender) < shares) shares = balanceOf(msg.sender);
_burn(msg.sender, shares);
emit Withdraw(address(asset), msg.sender, receiver, assets, shares, fee);
}Step 3:
The inherited ERC20 methods in the EFVault are not reimplemented and lack non-reentrant modifiers, allowing an attacker to re-enter these routines.
Step 4:
The exploiter initially took a flash loan of 80,000 ETH and deposited approximately 320 ETH into the ENF_ETHLEV contract, thereby receiving the ENF_ETHLEV tokens.
Step 5:
The ENF_ETHLEV tokens were withdrawn to convert them back to ETH. Upon receiving the ETH and before updating the ENF_ETHLEV token balance, due to a faulty judgment, they were sent to yet another contract, overriding the share balance.
Step 6:
The attack contract was used again to collect the ETH by burning a small amount of LP tokens. These processes were repeated across nine different transactions.
Step 7:
The exploited funds, worth 291.64 ETH, were held at this address and then transferred to this address at the time of this writing.
The team hasn’t communicated about this incident on their social media channels at Twitter, but they have sent an on-chain message to the exploiter who is in charge of the stolen funds at the moment.
According to them, they are ready to offer 10% of the hacked assets as a bounty in hopes of recovering the remaining funds. Once the funds have been received, they will also cease all further investigation and tracking with the security agencies.
In light of this exploit, we at Neptune Mutual believe that our offering could have played a crucial role in mitigating the damaging impact of this attack. This situation underscores the urgency and necessity of robust security measures and meticulous testing in the DeFi protocols to effectively prevent such risks.
A tailored solution to prevent future reentrancy attacks would be to implement a non-reentrant mutex in the vulnerable function. This would make the function non-reentrant, preventing the kind of attack that Earning Farm suffered. Also, the design pattern "checks-effects-interactions" can be used to ensure that all state changes take place before calling external smart contracts, minimizing the potential for reentrancy vulnerabilities. It is imperative that using such modifiers doesn’t simply ensure that the functionalities are immune to reentrancy attacks.
However, even with these precautions, it is important to understand that vulnerabilities might still go undetected. Neptune Mutual understands this reality and provides a solution to reduce the impact of such unfortunate incidents. If the team associated with Earning Farm had established a dedicated cover pool with us prior to the exploit, the aftermath of the incident could have been notably alleviated.
Neptune Mutual offers coverage to users who have sustained losses due to vulnerabilities in smart contracts, underpinning our solution with pioneering parametric policies. With our coverage policies, users don't need to go through the cumbersome process of proving their losses. Following the confirmation and resolution of an incident through our comprehensive incident resolution framework, users can claim their payouts promptly.
Our marketplace operates on numerous popular blockchain networks, including Ethereum, Arbitrum, and the BNB chain. This extensive reach allows us to serve a broad spectrum of DeFi users, offering protection from potential vulnerabilities and enhancing their faith in the ecosystem.
Reference Source Beosin