
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how classic arithmetic overflow issue was used to exploit Poolz Finance on multiple chains.
On March 15, 2023, Poolz Finance was exploited on Ethereum, Polygon, and BNB Chain, resulting in a total loss of approximately $550,000.
Poolz is a decentralized fundraising platform that helps cryptocurrency projects to launch and expand their communities via IDOs, NFT sales, and gaming projects.
The root cause of the exploit is due to the existence of a classic integer overflow vulnerability in its Vesting contract.
We have shared a detailed explanation of this attack vector, its occurrence, and prevention in our earlier blog titled Solidity Integer Overflow & Underflow.
Step 1:
We attempted to analyze one of the attack transactions executed by the exploiter.
Step 2:
The exploiter initially called the vulnerable CreateMassPools, which allows users to create pools in bulk, provide initial liquidity and record pool attributes. It invoked another call to the getArraySum function.
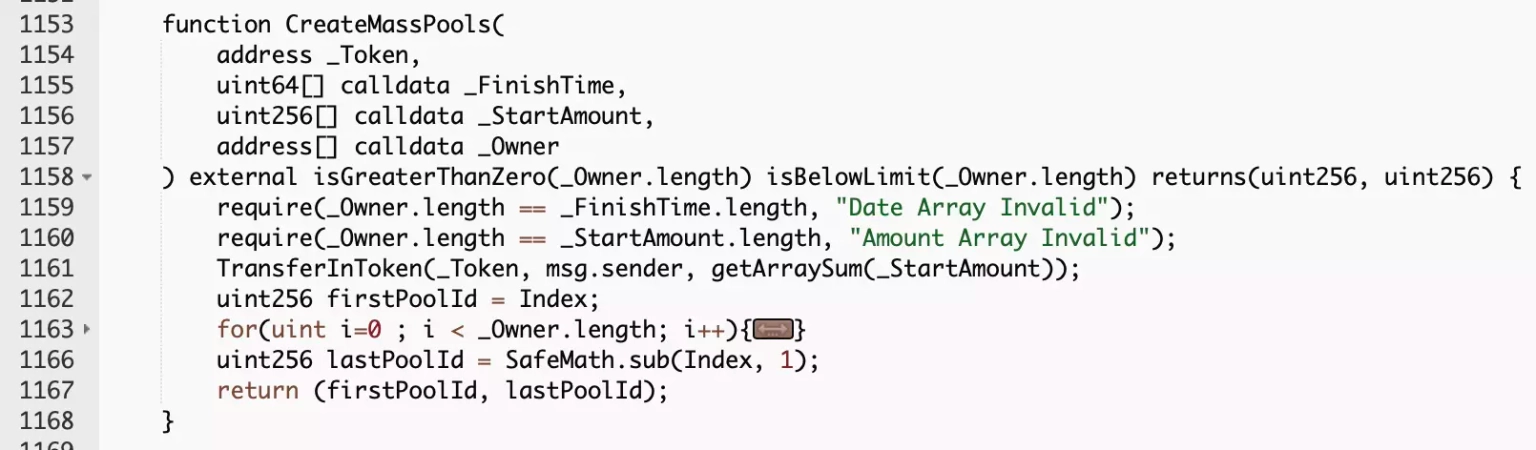
Step 3:
The getArraySum function controls the amount in the TransferInToken, which is used to establish liquidity in the pool. The array sum exceeded uint256 triggering the integer overflow vulnerability.
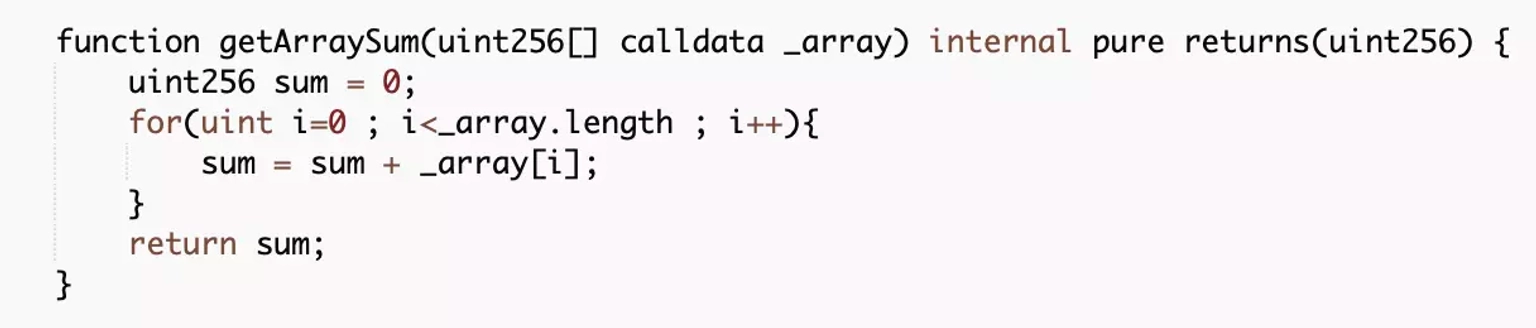
Step 4:
The exploiter then called the withdraw function to take away their share of profit from the attack.
Step 5:
The attacker also repeated the exploit on the Ethereum MainNet, and Polygon chain, stealing $ESNC, $POOLZ, $DON, $ASW and other tokens.
Step 6:
A large number of tokens were stolen and swapped for $BNB, and at the time of this writing, the attacker-controlled wallet address holds approximately 1,291 $BNB worth $397,668, 54.2 $ETH worth $91,216, and other assets in $POOLZ, $KMON, $ESNC, and $MATIC totaling roughly $550,000.
Following the attack, the price of the $POOLZ token dropped by more than 90%. The team reported that they are currently collaborating with law enforcement agencies and cyber security professionals and will soon provide a resolution.
According to them, the hacker address has been flagged on the explorers, and a complete freeze has been imposed on all POOLZ porting on Chainport bridge. They have removed the remaining liquidity from Uniswap and Pancakeswap, and will be deploying a new contract for new POOLZ token and will deploy liquidity based on the token exchange rate prior to the hack.
Additionally, they shared the specifics of the distribution of their new token, $POOLX. The $POOLZ token holders before the hack will receive the new token in a 1:1 ratio. The token holders prior official announcement will also receive the new tokens in a 1:1 ratio, including those who had sent tokens to the Chainport bridge before the hack but had their funds stuck due to these unforseen circumstances.
All cliffed token holders will be eligible to participate to participate in Poolz IDO, and will also receive a bonus 3 to 4% based on the size of their holdings.
A conventional approach to guard against underflow or overflow errors is to use or build mathematical libraries that replace the standard mathematical operators: addition, subtraction, and multiplication.
The SafeMath library by Open Zeppelin provides the fundamental arithmetic operations as well as the ability to throw errors based on the preconditions and postconditions to determine whether an overflow or underflow has occurred.
Solidity compilers above version 0.8.0 can automatically check for overflows and underflows and produce an error if the values go out of bounds. Moreover, it is also important to properly design the smart contract in order to prevent potential Denial of Service attacks that are based on integer overflow and underflow issues.
Reference Source PeckShield