
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how the NeverFall project was exploited, which resulted in a loss of $74,250.
On May 2, 2023, the NeverFall project on the BNB chain was exploited due to price manipulation, resulting in a loss of approximately $74,250.
The root cause of the vulnerability is due to the flawed calculation that relies on the balance of the corresponding PancakeSwap pair.
Step 1:
We attempted to analyze the attack transaction executed by the exploiter.
Step 2:
In the `sell` function of their contract, the liquidity to be removed gets calculated based on the token balance of the pair.
function sell(uint256 amount) public returns (uint256) {
super._transfer(msg.sender, address(this), amount);
//撤池子 退给用户U
uint256 balanceNF = this.balanceOf(uniswapV2Pair);
uint256 pairTotalSupply = IERC20(uniswapV2Pair).totalSupply();
uint256 needLiquidity = amount * pairTotalSupply / balanceNF;
uint256 beforeU = IERC20(usdtAddress).balanceOf(address(this));
removeLiquidity(needLiquidity, amount * 90 / 100, 0);
uint256 afterU = IERC20(usdtAddress).balanceOf(address(this));
uint256 outU = afterU - beforeU;
IERC20(usdtAddress).safeTransfer(msg.sender, outU * sellFee / 100);
//营销
IERC20(usdtAddress).safeTransfer(marketingAddress, outU * sellMarketingFee / 100);
emit SellNF(msg.sender, amount, outU);
return outU * sellFee / 100;
}Step 3:
The exploiter was able to trick the contract into burning a huge amount of liquidity using a flash loan and performing a large swap on the pair.
Step 4:
The attacker took a flash loan of 1.6 million $BUSD and used 200,000 $BUSD to buy approximately 75.47 million $NeverFall tokens via buy function in the Never Fall contract.
Step 5:
The buy function added liquidity to the contract with 90% $BUSD deposited by the user and $NeverFall tokens. The remaining 1.4 million $BUSD is then swapped for $NeverFall in the BUSD-Never Fall pool, and the held $NeverFall tokens are sold using the `sell` function.
Step 6:
The attacker repaid the flash loan, after which the profit of approximately 74,250 $BUSD was swapped for BNB and then laundered to Tornado Cash.
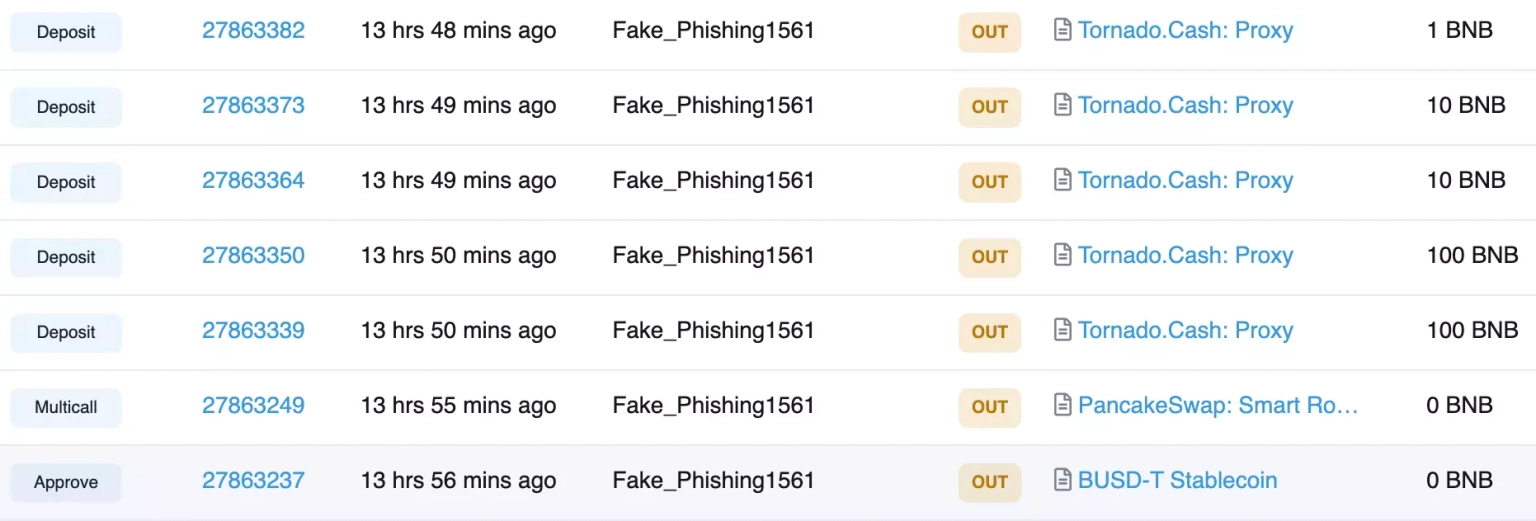
The unfortunate exploitation of the NeverFall project was largely due to a flawed calculation that relied heavily on the balance of the corresponding PancakeSwap pair. The attack succeeded because the attacker was able to manipulate the price of the token by exploiting a flawed calculation scheme. This exploit could have been prevented to a greater extent if the token price didn't rely on the balance of the corresponding PancakeSwap pair.
While it is impossible to completely eliminate the risk of such exploits, adequate user coverage can significantly reduce the impact of such attacks. This is where Neptune Mutual comes into play.
Neptune Mutual provides coverage to users who have suffered a loss of funds or digital assets due to such smart contract vulnerabilities. If the NeverFall project had established a dedicated cover pool in the Neptune Mutual marketplace prior to the attack, users could have been compensated for their losses promptly without needing to provide explicit loss evidence.
This is thanks to Neptune Mutual's parametric policies, which are designed to provide instant payouts as soon as an incident is resolved through our incident resolution system. This could have been an invaluable asset to the users affected by the NeverFall exploit. At the moment, our marketplace is available on two popular blockchain networks, Ethereum, and Arbitrum.
Moreover, Neptune Mutual's security team continually evaluates platforms for potential vulnerabilities, considering aspects like DNS and web-based security, frontend and backend security, and intrusion detection and prevention. If NeverFall had engaged with Neptune Mutual for these services, this vulnerability might have been detected and rectified before it was exploited.