
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how an attacker exploited the Multichain's AnyswapV4Router contract to take away 87 ETH.
On February 15, 2023, the AnyswapV4Router contract of Multichain encountered a front-running attack, during which the attacker made a profit of about 87 ETH, worth approximately $130,000.
Multichain is an infrastructure designed to support arbitrary cross-chain interactions.
The vulnerability occurred because the attacker used a MEV contract to front-run and invoke a function of the AnySwapV4Router contract to sign and approve the transfer.
Step 1:
We attempted to analyze the attack transaction executed by the exploiter.
Step 2:
The attacker used the MEV contract to front-run and call the anySwapOutUnderlyingWithPermit function of the AnyswapV4Router contract in order to sign and approve the transfer.
Step 3:
Despite the fact that the function makes use of the token's permit signature verification, the stolen WETH lacked a related signature verification function and only triggers a fallback in the deposit function.
Step 4:
Thus, due to the lack of signature verification, the attacker is able to transfer the $WETH approved to the victim contract, through the from address parameter directly to the attack contract using the safeTransferFrom function.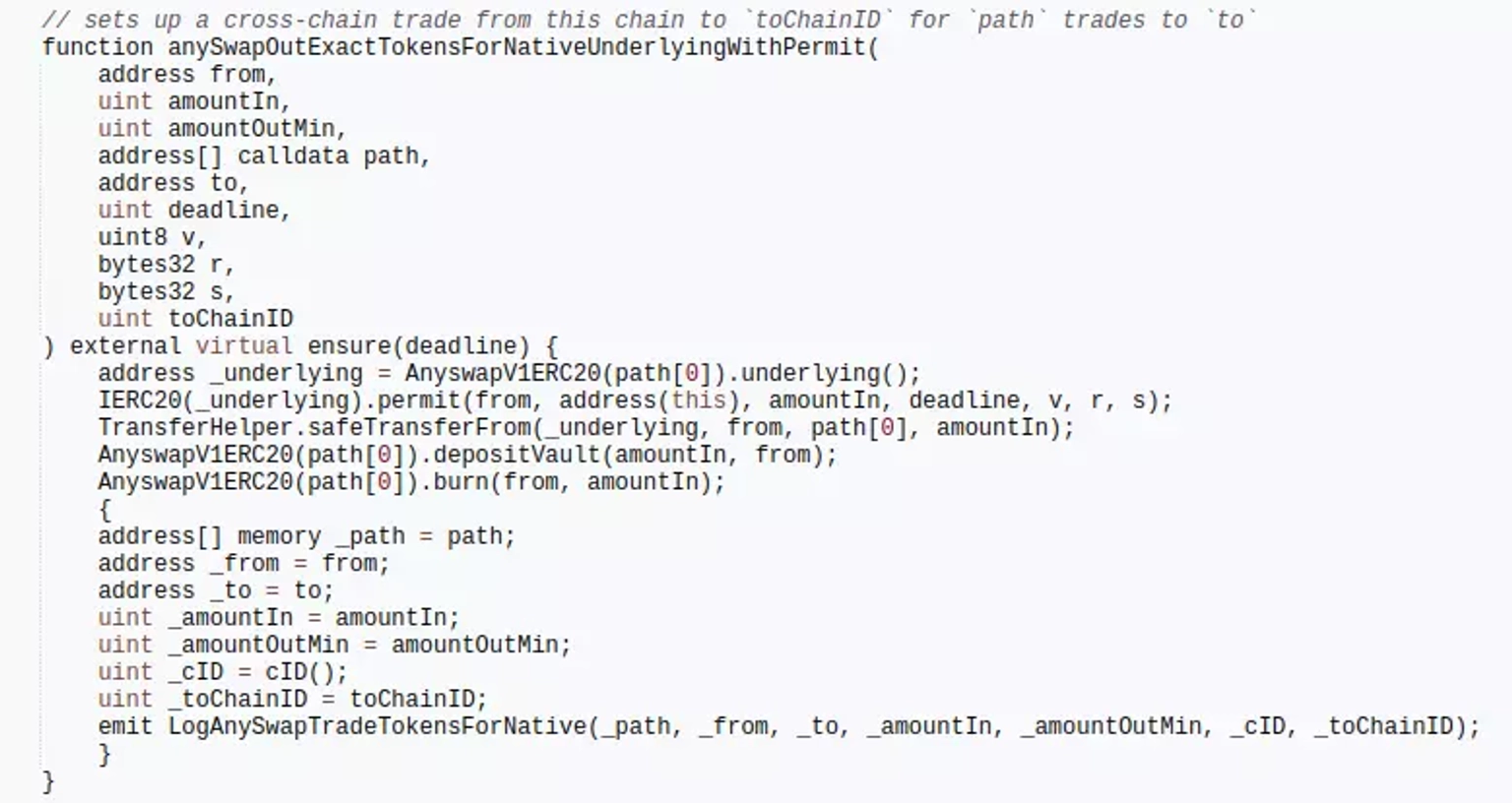
The team stated that this was an old vulnerability that was reported in January 2022.
In their previous postmortem report, they explicitly stated that the risk originating from this exploit still remained for users who had not yet revoked approvals for the affected router contracts.
They further mentioned that the users themselves would have to revoke the approvals.
Between January 10, 2022 and February 19, 2022, the team reported that more than 61% of all affected users had revoked access to the contract containing the underlying vulnerability.
The liquidity pool's vulnerability was quickly fixed after it was reported, as the team upgraded the affected tokens' liquidity to new contracts. The risk remained, however, for users who had not yet revoked approvals for the affected router contracts.
We may not have prevented the occurrence of this hack, however the impact or aftermath of this attack could have been significantly reduced if the team associated with Multichain Protocol had set up a dedicated cover pool in the Neptune Mutual marketplace. We offer coverage to users who have suffered a loss of funds or digital assets occurring as a result of smart contract vulnerabilities owing to our parametric policies.
Users who purchase the available parametric cover policies do not need to provide loss evidence in order to receive payouts. Payouts can be claimed as soon as an incident is resolved through the incident resolution system. At the moment, our marketplace is available on two popular blockchain networks, Ethereum, and Arbitrum.
Neptune Mutual's security team would also have evaluated the platform for DNS and web-based security, frontend and backend security, intrusion detection and prevention, and other security considerations.
Reference Source BlockSec