
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Find out about the MyEtherWallet DNS Spoofing attack that resulted in a hack of over $150,000.
On April 24, 2018, the DNS registration servers of MEW (MyEtherWallet) were compromised by third-party actors, in which hackers got away with over $152,000 worth of Ether.
MyEtherWallet, also known as MEW is an easy-to-use, open-source, client-side interface that enables users to interact with the Ethereum blockchain, and manage their funds without the need of a centralized platform.
The root cause of the vulnerability was the hacker's ability to spoof DNS entries after executing a BGP route hijack that diverted huge swaths of Internet traffic intended for Amazon servers to the systems they controlled.
Step 1:
The attackers took advantage of flaws in two fundamental internet protocols that route traffic around the world: the Border Gateway Protocol (BGP) and the Domain Name System (DNS) (DNS).
Step 2:
MyEtherWallet.com made use of Amazon's Route 53 DNS service, however neither AWS nor Amazon Route 53 were hacked or compromised.
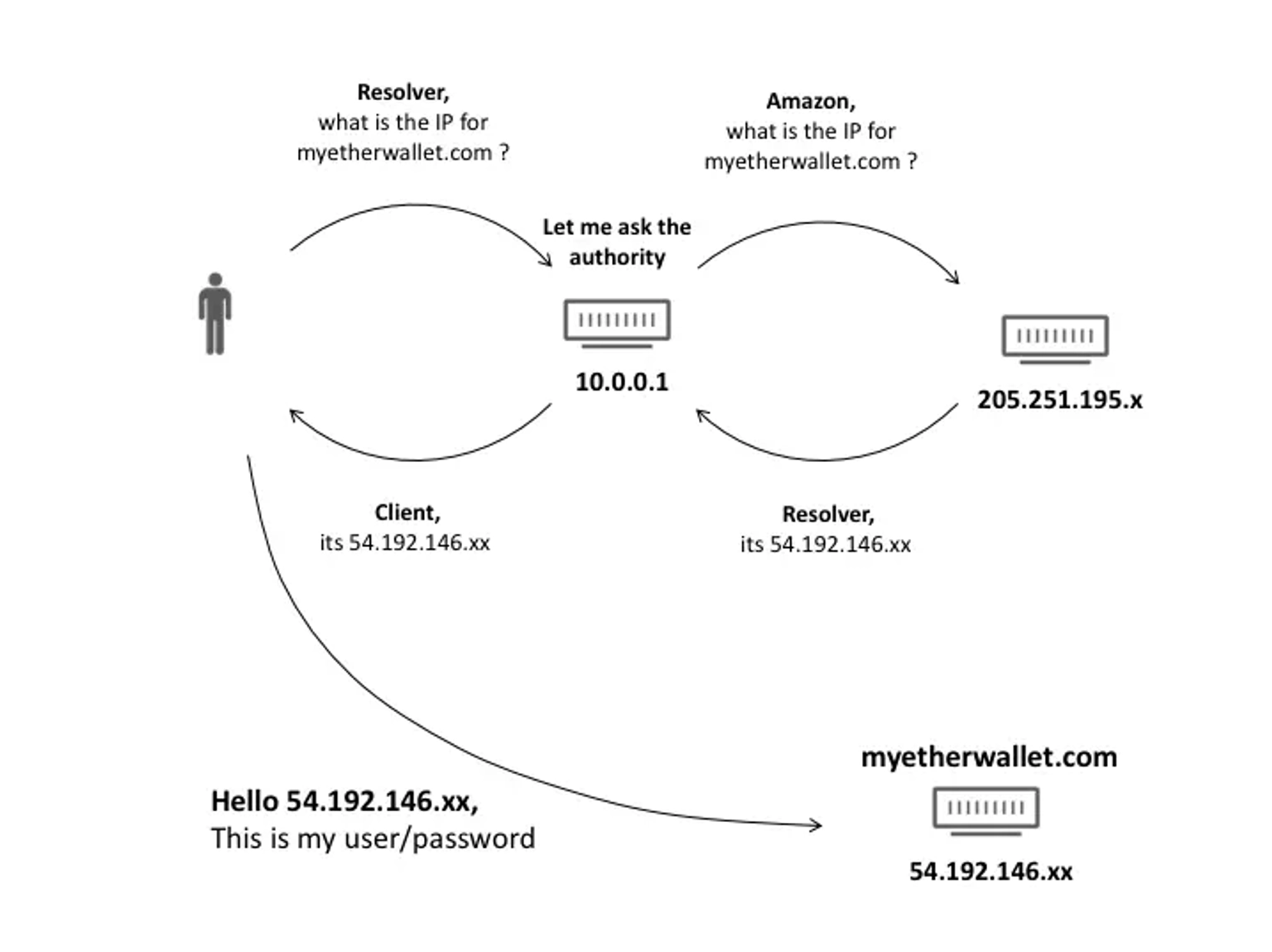
MyEtherWallet regular internet routing. Courtesy of cloudflare.com
Step 3:
IP addresses are the communication protocol used by web browsers. In order for browsers to load Internet resources, DNS servers translate domain names to IP addresses. Each Internet-connected device has a distinct IP address that may be used by other devices to locate it.
Step 4:
The attackers used the BGP protocol to reroute traffic to Amazon's Route 53 service during the hack.
Step 5:
Using a server at Chicago's Equinix, they used a man in the middle attack to reroute DNS traffic. For more than two hours, this provided them with the necessary traffic, enabling them to intercept Internet traffic headed for Amazon Route 53 customers around the world.
Step 6:
This allowed them to redirect traffic intended for MyEtherWallet.com to the fake phishing website, which was housed on a Russian server.
Step 7:
Therefore, MyEtherWallet.com returned IPs belonging to that Russian provider (AS48693 and AS41995), instead of IPs that were allocated to their domain name.
Step 8:
MyEtherWallet customers reportedly noticed something odd when they visited the wallet's website and saw a warning that the site was utilizing an incorrect security certificate.
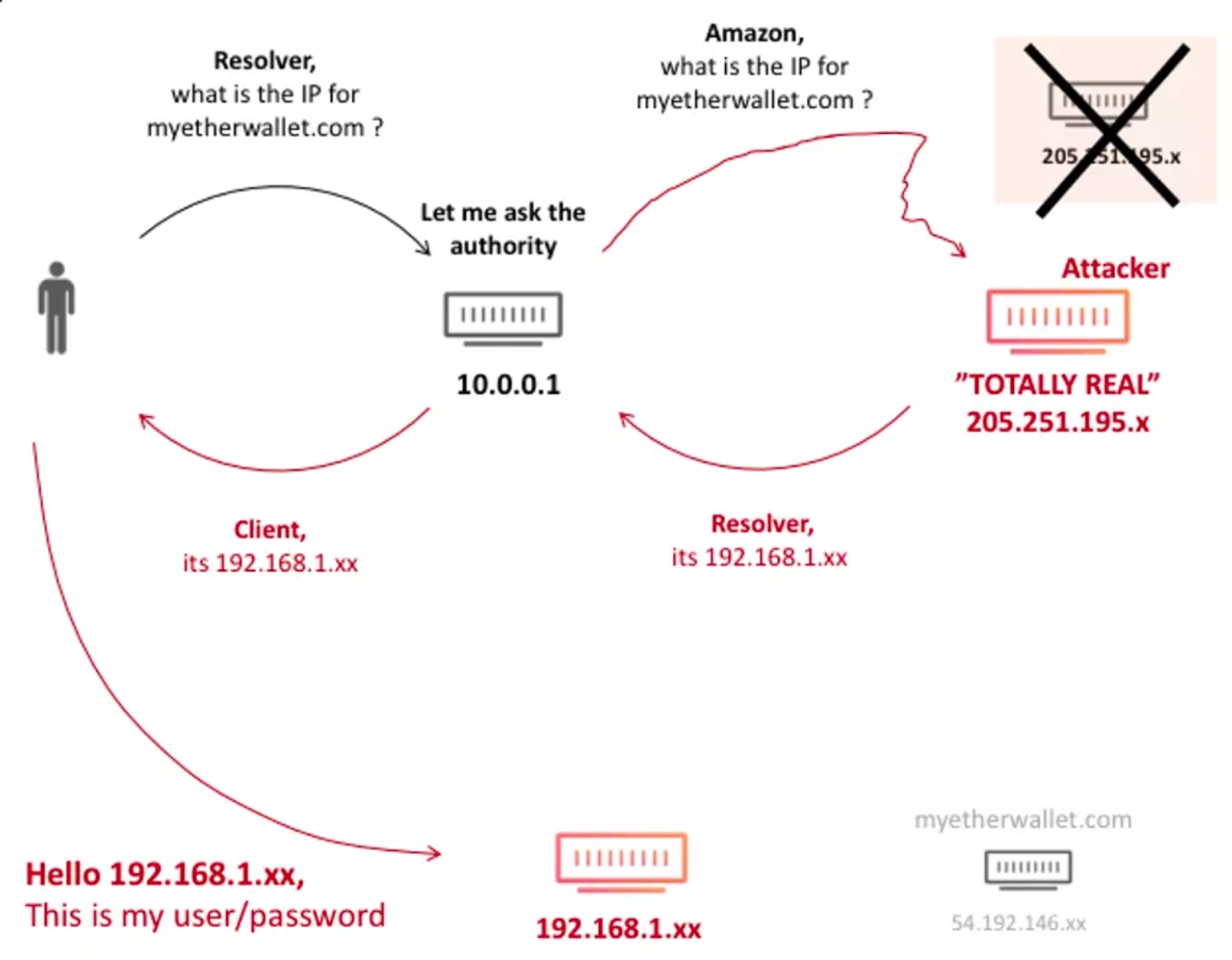
MyEtherWallet routing during the attack. Courtesy of cloudflare.com
Step 9:
Despite the warning, they continued to log in because the website address and everything else about the service appeared to be fine to them.
Step 10:
After logging in, a 10-second timer appeared, counting down until the funds in the wallet were transferred to the attacker.
Step 11:
The attack was especially difficult to detect because it compromised fundamental internet systems that users rarely check. This enabled an attacker to post distorted announcements that redirected traffic without being detected.
MyEtherWallet administrators discovered the DNS hijacking incident and made an effort to alert users via a Twitter announcement. The hacker collected their Ether at this address.
About two hours after the attack, MyEtherWallet was able to regain access over its DNS entries, but the hacker had already moved the 215 ETH worth of stolen funds to another account.
Domain Name System (DNS) spoofing, also known as DNS cache poisoning, is a kind of cyberattack in which a victim's DNS server is tricked into associating a hostile server with a valid domain name. If successful, this strategy exposes customers who put the genuine domain name into their browser to risks such as phishing, malware, and other types of fraud.
Utilizing secure DNS servers that encrypt DNS traffic is one potential defense against DNS hijacking attacks. This can aid in preventing traffic from being intercepted and forwarded to malicious servers by attackers. Although securing BGP could be challenging, employing security practices like DNSSEC and HSTS would have reduced the impact of this kind of attack. When DNSSEC is enabled, fraudulent DNS entries are rejected by DNS resolvers. With HSTS enabled, browsers shield users from self-signed certificates.
Utilizing a DNS firewall is another option for preventing DNS attacks because it blocks malicious traffic and only permits legitimate traffic to get to its destination. Utilizing a reliable and trustworthy DNS service provider is advisable since they will have additional safety procedures in place to guard against DNS hijacking and other attacks of a similar nature.
Users can protect themselves by keeping an eye out for suspicious activity on the platform they use. It is always important to be aware of the risks and take appropriate precautions to protect ourselves when clicking on links from unknown or untrustworthy sources.
Neptune Mutual was not available as a marketplace at the time of the event, thus users who fell for this phishing scheme probably had no way of recovering their funds. We may not have been able to prevent this hack from occurring, but we could have reduced or mitigated the aftermath of the attack to a greater extent. Users who would have purchased the available parametric cover policy for MyEtherWallet need not have to provide loss evidence in order to receive their payout. Payouts would have been made as soon as this type of incident was resolved through our governance system.
Neptune Mutual's security team would also have evaluated the platform for DNS and web-based security, frontend and backend security, intrusion detection and prevention, and other security considerations.
Reference Source MyEtherWallet