
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how a vulnerability in MetaPoint's smart contract led to a loss of $920,000.
On April 12, 2023, MetaPoint was exploited due to a smart contract vulnerability, which resulted in the loss of funds worth approximately $920,000.
MetaPoint is an online virtual world where players can participate in virtual reality activities such as games, management, finance, construction, entertainment, etc. in order to obtain economic benefits and pleasant experiences.
The root cause of the vulnerability is due to the existence of a public approval function, which was exploited to transfer all of the user's assets.
Step 1:
We attempted to analyze the attack transaction executed by the exploiter.
Step 2:
One of their contracts contained an open approval function that allowed the attackers to obtain the full amount of the user’s deposit.
Step 3:
The exploiter created attack contracts to invoke a call to the approve function of this contract in bulk and approved the maximum value.
Step 4:
At the time of this writing, this attacker has control over approximately $98,000 worth of assets, while the other attacker has already transferred 2515 $BNB tokens worth approximately $814,000.
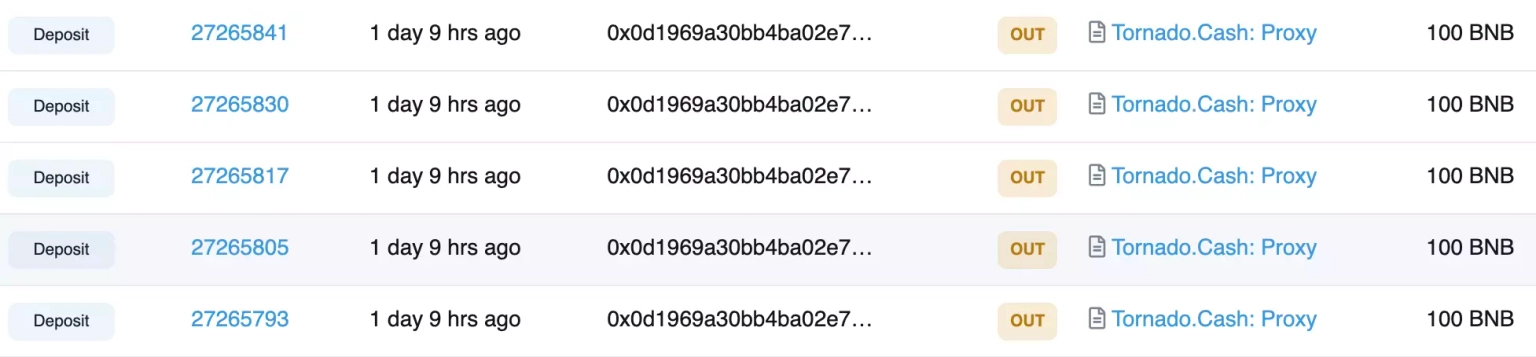
Following the attack, the team acknowledged the incident and asked to stop all interactions with the contract.
They will apparently turn to a third-party auditor in order to perform a security audit of their code base and will also look forward to formulating and announcing their next course of action.
The attack, which exploited a public approval function, could have been detected and rectified with regular smart contract audits conducted by independent third-party auditors. These audits not only identify vulnerabilities but also recommend strategies to mitigate them, thus reducing potential attack vectors.
In addition, permissions within the smart contract should have been properly managed. In MetaPoint's case, a function with significant power over users' funds was left open to public access, enabling the attacker to take control of these funds. Protocols should, therefore, limit user permissions to those strictly necessary for protocol interaction, eliminating the possibility of malicious activity exploiting critical functionalities.
Despite the best security efforts, the potential for hacks and exploits still exists. This is where solutions like Neptune Mutual can play a critical role in risk management and mitigation. Had MetaPoint set up a dedicated cover pool with Neptune Mutual prior to the attack, the financial impact could have been significantly reduced. We offers parametric cover policies that provide coverage for losses due to smart contract vulnerabilities.
Neptune Mutual's policies are designed with user convenience in mind. Users who purchase these policies do not need to provide evidence of loss to receive payouts. Once an incident is resolved through our incident resolution system, payouts can be claimed immediately. Our marketplace operates on two leading blockchain networks, Ethereum and Arbitrum, thus providing widespread coverage.
Moreover, Neptune Mutual's security team conducts thorough evaluations of platform security, encompassing aspects such as DNS and web-based security, frontend and backend security, and intrusion detection and prevention. This all-encompassing approach to security can help identify potential vulnerabilities and provide recommendations to fortify the platform against future attacks.
Reference Source CertiK