
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how an attacker exploited Euler Finance to steal funds worth approximately $200 million.
On March 13, 2023, Euler Finance was exploited in a series of transactions, resulting in a total loss of approximately $200 million.
Euler Finance is a UK-based startup that uses the power of mathematics in order to create high-performance, non custodial products on Ethereum and other blockchains.
The vulnerability occurred because Euler Finance permitted donations without having an account health check. The exploit lies in the change made to the EToken implementation, specifically in the donateToReserves function.
This issue was introduced through Euler Improvement Proposal 14 that made multiple changes in its ecosystem. The changes were also the subject of a number of security audits, but the security audit firms were not able to find the vulnerabilities. According to the team, this vulnerability remained on-chain for 8 months, until it was exploited.
The Liquidation module will try to pay off the full debt of the violator. However, the protocol will default to whatever collateral the user has if their collateral doesn't meet the expected repayment yield. This was possible when a borrower had multiple collaterals, and taking them all away won't make the violator solvent again.
Step 1:
We attempted to analyze one of the attack transactions executed by the exploiter.
Step 2:
The hacker first took a flash loan of 30 million $DAI from AAVE and deposited 20 million $DAI on the Euler Protocol to receive 20 million $eDAI.
Step 3:
They then invoked a call to the mint function in order to borrow approximately $200 million in eDAI (collateral assets) and $200 million in dDAI (debt assets), thereby scaling their DAI balance up by 10 folds.
Step 4:
The attacker deposited 10 million $DAI via the repay function, repeated the above procedures again, and then invoked the donate to reserve call to burn $100 million worth of eDAI. Because of this, the amount of dDAI were greater than the held amount of eDAI, which effectively skipped their liquidation checks and made them liquidatable.
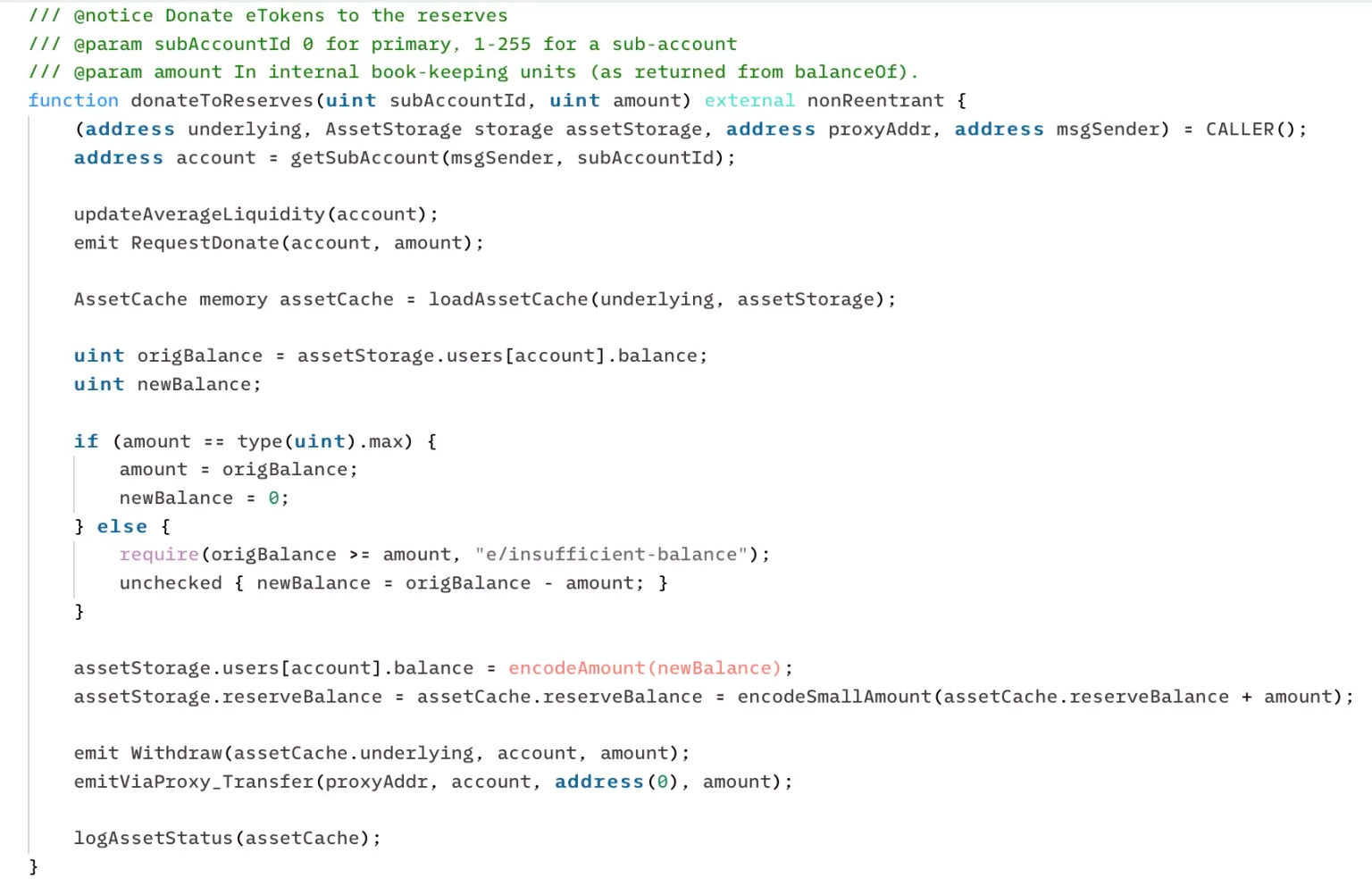
Step 5:
Therefore, as the ratio of the collateral assets in eDAI to the debt assets in dDAI was less than 1, this allowed the liquidator to liquidate the attacker's debt without transferring funds to the protocol.
Step 6:
The attacker withdrew approximately 38 million $DAI from the contract and repaid the borrowed flash loan back to AAVE, making a profit of roughly 8.9 million $DAI.
Step 7:
The exploiter also repeated the attacks on other pools, for which the attack transactions reference are listed alongside: Transaction 2, Transaction 3, Transaction 4, Transaction 5, Transaction 6
Step 8:
At the time of this writing, the hacker has held 8080 $ETH worth approximately $13.5 million in this address, and 88,651 $ETH worth $148,449,041 plus 43,063,733 $DAI totaling approximately $191.49 million in this address.
Step 9:
The exploiter has also transferred 100 $ETH worth approximately $158,000 to Tornado Cash.
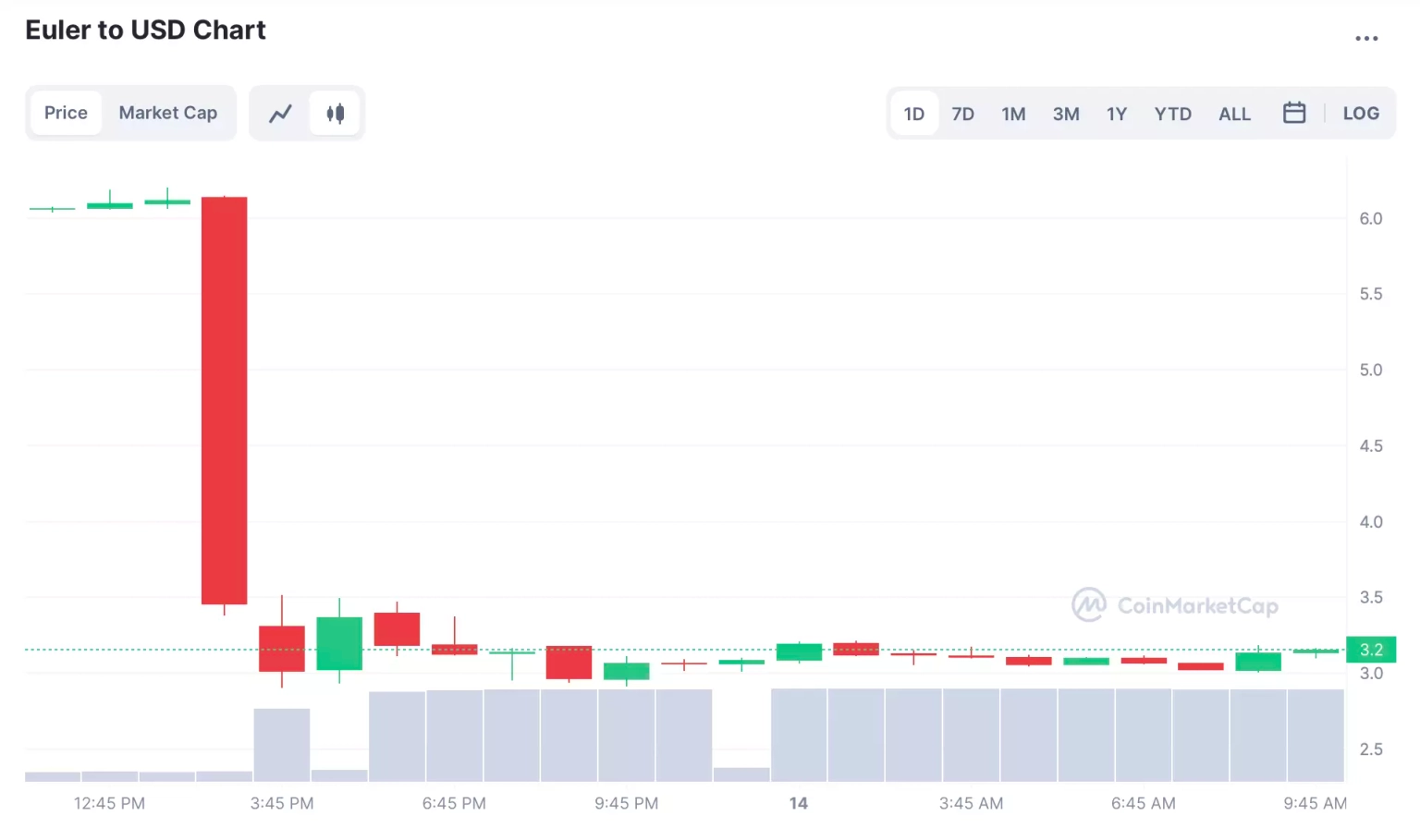
Following the attack, the price of Euler native $EUL token fell by 50%.
The team stopped the attack as soon as possible by disabling the EToken module, which blocked deposits, and the vulnerable donation function. The team stated that they would continue to work with their security partners, law enforcement agencies, and the security community as a whole in order to resolve this unprecedented incident. Additionally, they have also contacted the individuals behind the exploit in order to learn about their available options.
The complex, mathematics-powered world of DeFi, as seen with the Euler Finance exploit, is both its strength and its Achilles' heel. The exploit's scope, with losses amounting to approximately $200 million, demonstrates the severity of potential vulnerabilities even within well-audited systems. Euler Finance, despite its comprehensive approach and previous security audits, fell victim to an unforeseen vulnerability that lingered in its ecosystem for eight months. The intricacies surrounding the misuse of the donateToReserves function and the flaws in the EToken implementation amplify the critical need for multifaceted security solutions.
In light of this incident, Neptune Mutual recognizes the essence of robust, all-encompassing safeguards in the DeFi space. Offering a system of parametric cover policies could have substantially alleviated the financial repercussions of the Euler Finance exploit. While security testing and audits are imperative, they cannot guarantee the detection of every vulnerability, especially as the complexity of DeFi protocols grows. Insurance coverage becomes a much-needed safety net in such unpredictable scenarios.
Had Euler Finance partnered with us and set up a dedicated coverage pool, the affected stakeholders might not have borne the brunt of this exploit so intensely. Users insured under our parametric policies could have laid claim to their covered amounts immediately after the incident's resolution without wading through the usual tedious process of producing evidence of loss. The beauty of our coverage lies in its simplicity, accessibility, and speed, which are paramount in crises. Our marketplace presence on both the Ethereum and Arbitrum networks ensures that a wide spectrum of users can benefit from our services.
Beyond mere financial insurance, Neptune Mutual would also have provided Euler Finance with a comprehensive technical and security review. Our expertise extends beyond just contract vulnerabilities; we dive deep into platform-wide considerations, including DNS and web-based security, front-end and back-end security, and intrusion detection mechanisms.