
Taking a Closer Look at the YIEDL Exploit
Learn how Yiedl was exploited, resulting in a loss of assets worth approximately $160,000.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how the CS Token was exploited, resulting in a loss of approximately $715,000.
On May 23, 2023, CS Token was exploited, resulting in a total loss of approximately $715,000.
The attack was successful because in the _transfer function of the contract, the burnAmount parameters are calculated using sellAmount; however, the sellAmount value doesn't get updated in time.
Step 1:
We attempted to analyse the attack transaction executed by the exploiter.
Step 2:
The attacker initially took a flash loan of $80 million from PancakeSwap and swapped it for $CS token.
Step 3:
The swap helped them accumulate a large number of $CS tokens, which were further converted back to $BUSD.
Step 4:
For each of those conversions, the CS contract recorded the sellAmount parameter of the associated transaction, after which the exploiter called the CS contract yet again to perform small fund transfers.
Step 5:
During the transfer process, the held funds were being burned in the transaction pairs, represented by the burnAmount parameter of the contract, which is calculated based on the sellAmount parameter.
Step 6:
As the sellAmount parameter is not updated in real time, the attacker was able to gradually decrease the amount of CS tokens in the BUSD/CS trading pair and eventually profit by exchanging a small amount of $CS tokens for a large amount of $BUSD.
Step 7:
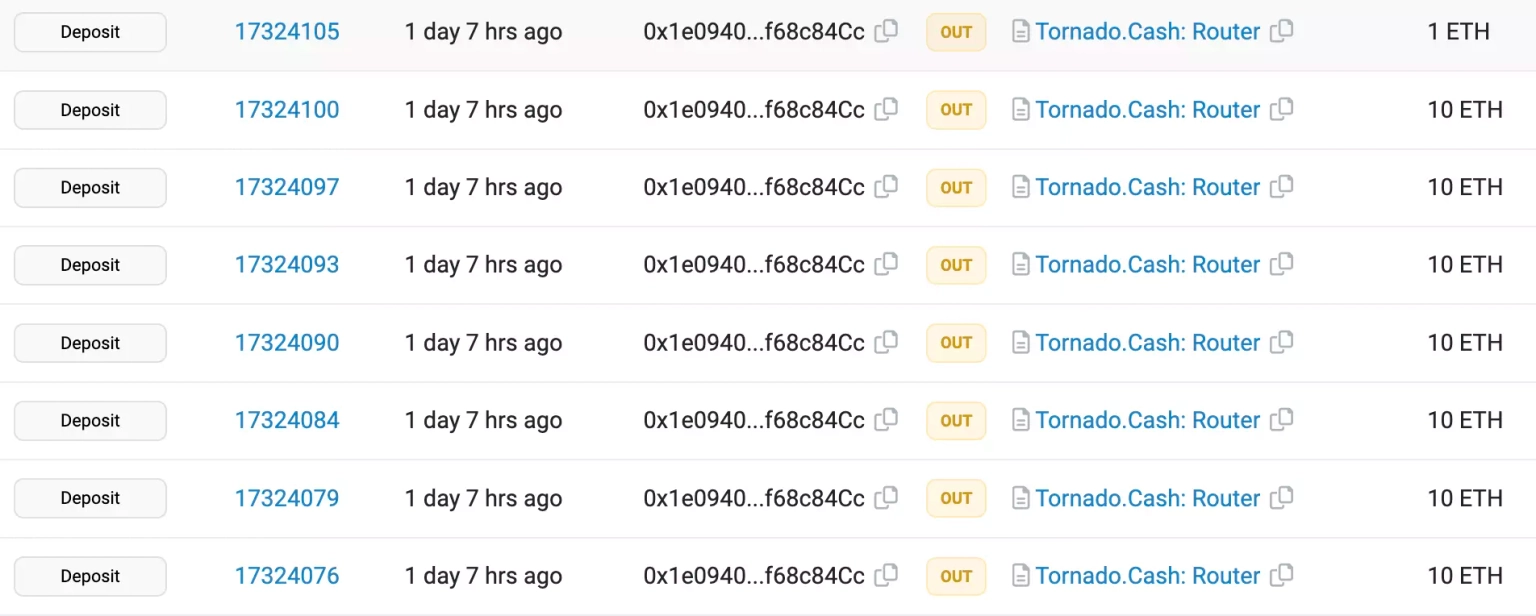
The borrowed flash loan was repaid, and the attacker then converted all of the $BUSD to $ETH and cross-chain transferred them to Ethereum before eventually laundering funds worth approximately 383 ETH to Tornado Cash.
It is critical to understand that no security measure is perfect, but implementing rigorous security standards can greatly reduce the risk of all such attacks on DeFi protocols. These standards can aid in identifying and addressing potential attack vectors before they are exploited by attackers.
Many formal verification tools can also be used to ensure that the smart contract behaves as it is intended to. Independent third-party auditors should conduct regular smart contract audits to identify vulnerabilities and recommend mitigation strategies.
We may not have prevented the occurrence of this hack, however the impact or aftermath of this attack could have been significantly reduced if the team associated with CS Token had set up a dedicated cover pool in the Neptune Mutual marketplace. We offer coverage to users who have suffered a loss of funds or digital assets occurring as a result of smart contract vulnerabilities owing to our parametric policies.
Users who purchase the available parametric cover policies do not need to provide loss evidence in order to receive payouts. Payouts can be claimed as soon as an incident is resolved through the incident resolution system. At the moment, our marketplace is available on two popular blockchain networks, Ethereum, and Arbitrum.
Neptune Mutual's security team would also have evaluated the platform for DNS and web-based security, frontend and backend security, intrusion detection and prevention, and other security considerations.