
Taking a Closer Look at the YIEDL Exploit
Learn how Yiedl was exploited, resulting in a loss of assets worth approximately $160,000.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Bearn DAO was exploited, resulting in a loss of assets worth $769,000.
On December 6, 2023, Bearn DAO was exploited due to a smart contract vulnerability, which resulted in a loss of assets worth approximately $769,000.
Bearn is a decentralized reserve currency protocol on the BNB chain.
The root cause of the exploit was a vulnerability that allowed the attacker to manipulate token swap ratios and execute a profitable sandwich attack.
Step 1:
We attempt to analyze the attack transaction executed by the exploiter.
Step 2:
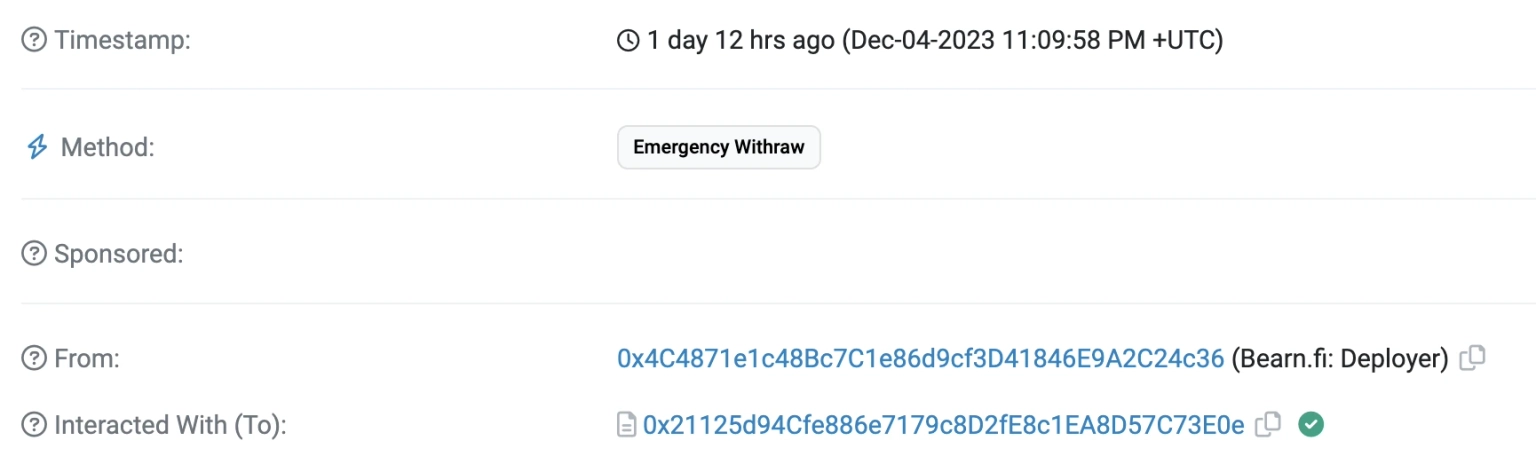
Before the attack took place, on-chain details revealed that the deployer of the contract had invoked a call to the emergency withdrawal function.
Step 3:
The deployer, however, didn't or failed to withdraw the funds from the exploited contract.
Step 4:
As viewed in the logic of the convertDustToEarned function, the vulnerable BvaultsStrategy contract relied on the current balance of the `wantToken` token. But the strategy contract is not supposed to hold a huge amount of dust tokens.
function convertDustToEarned() public whenNotPaused {
require(isAutoComp, "!isAutoComp");
// Converts dust tokens into earned tokens, which will be reinvested on the next earn().
// Converts token0 dust (if any) to earned tokens
uint256 wantAmt = IERC20(wantAddress).balanceOf(address(this));
if (wantAddress != earnedAddress && wantAmt > 0) {
IERC20(wantAddress).safeIncreaseAllowance(uniRouterAddress, wantAmt);
// Swap all dust tokens to earned tokens
IPancakeRouter02(uniRouterAddress).swapExactTokensForTokensSupportingFeeOnTransferTokens(wantAmt, 0, paths[wantAddress][earnedAddress], address(this), now + 60);
emit ConvertDustToEarned(wantAddress, earnedAddress, wantAmt);
}
}
Step 5:
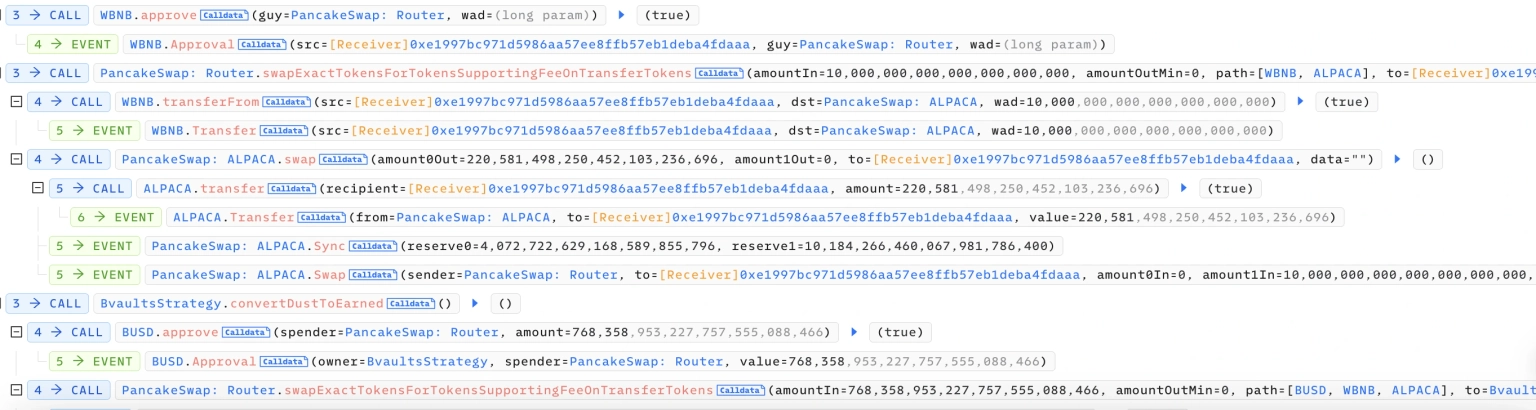
The attacker first manipulated the ALPACA/WBNB pool through large-valued swaps and invoked a call to the convertDustToEarned function, thereby artificially inflating the swap ratio of the tokens.
Step 6:
The reverse swap allowed the attacker to perform a sandwich attack, letting them take away approximately $768,358 worth of assets as profits.
Step 7:
The exploiter has since transferred 40,000 BUSD to this address and approximately 160,000 BUSD to this address. The remaining assets worth $560,645, at the time of this writing, are still held at this address controlled by the attacker.
The team hasn't acknowledged the attack on their social media channels on Twitter.
However, they have sent an on-chain message to the attacker stating that they had withdrawn BUSD from the vault contract to convert them to USDT. According to them, the stolen funds don't belong to the team but rather to the users, and they have thus asked the attacker to refund a portion of the funds back to them, allowing them to reimburse the affected users. The attacker is told to retain a portion of the stolen assets as bounty rewards.
The recent Bearn DAO exploit underscores the critical need for constant vigilance in the dynamic and often unpredictable world of decentralized finance. This incident not only highlights specific vulnerabilities but also serves as a catalyst for a broader reassessment of security practices and communication protocols in the DeFi sector. As we dissect this event, it becomes clear that a multifaceted approach is necessary to steer our course towards a more fortified and resilient DeFi ecosystem.
Central to this exploit was a significant flaw in the convertDustToEarned function of Bearn DAO's smart contract. This vulnerability laid the groundwork for an attacker to manipulate token swap ratios, facilitating a sophisticated sandwich attack. This incident should prompt DeFi protocols to rigorously reevaluate and revamp the logic underpinning their token conversion processes. It’s imperative that these processes are designed to be inherently resistant to external manipulation, thereby safeguarding against similar exploits.
Equally consequential in this exploit was the capacity to manipulate token prices, which played a pivotal role in the attacker's strategy. To mitigate such risks, a more robust oracle mechanism is crucial. Oracles should be engineered to source data from a diverse spectrum of reliable feeds, significantly diminishing the likelihood of a single point of failure. Additionally, the strategic implementation of circuit breakers stands as a necessary safeguard. These mechanisms should be capable of suspending trading activities in the event of extreme and unnatural price fluctuations, serving as a critical line of defense against potential market manipulation.
The exploit also casts a spotlight on the current inadequacies of emergency response protocols within DeFi protocols. The necessity for a more sophisticated and automated system for emergency withdrawals cannot be overstated. Such a system should encompass multi-signature approvals and time-locked transactions, ensuring that any emergency response is executed promptly yet securely. The peculiar nature of the on-chain message sent to the exploiter further amplifies concerns regarding potential insider involvement, an aspect that requires thorough investigation and reinforced internal controls.
Beyond these specific vulnerabilities, it is paramount to reinforce the overall security framework of DeFi platforms. Regular and comprehensive audits should become a standard practice, extending beyond internal reviews to include external experts. Furthermore, leveraging bug bounty programs to engage the broader community is a strategic move. These programs can tap into a vast reservoir of talent and expertise, enabling the early detection and mitigation of potential security threats.
Despite the best efforts of developers and auditors to create a robust codebase and conduct thorough testing, the inherent complexity of smart contracts means that vulnerabilities may occasionally go unnoticed. This reality highlights the importance of a security strategy that is both proactive and reactive.
In this context, Neptune Mutual offers a vital safeguard against the unexpected repercussions of such vulnerabilities. Had the Bearn team partnered with us at Neptune Mutual to establish a dedicated cover pool before the incident, the financial impact of the exploit could have been greatly reduced. We at Neptune Mutual provide coverage for users who suffer losses of funds or digital assets due to smart contract vulnerabilities, leveraging our innovative parametric policies.
For users who choose our parametric cover policies, there is no need to submit proof of loss to receive a payout. As soon as an incident is verified and resolved through our incident resolution system, the affected parties can claim their payouts immediately.
Moreover, our marketplace offers its protective services across various blockchain networks, including Ethereum, Arbitrum, and the BNB chain. This broad accessibility not only provides a safety net to a diverse range of DeFi users but also significantly contributes to bolstering confidence within the DeFi ecosystem.
Reference Source Ancilia