
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe
Learn how the ASKACR token was exploited due to a logic error, resulting in a loss of 85 BNB.
On March 21, 2023, the ASKACR Token on BNB Chain was exploited, resulting in a total loss of 85 BNB, worth approximately $28,400.
$ASKACR is a token on BNB Chain.
The attack was possible because of a flaw in the way rewards are distributed by the transfer function, which operates without checking the transfer amount.
Step 1:
We attempted to analyze the attack transaction executed by the exploiter.
Step 2:
The _transfer function has a logic, which invokes another call to the _beforeTokenTransfer function of the contract.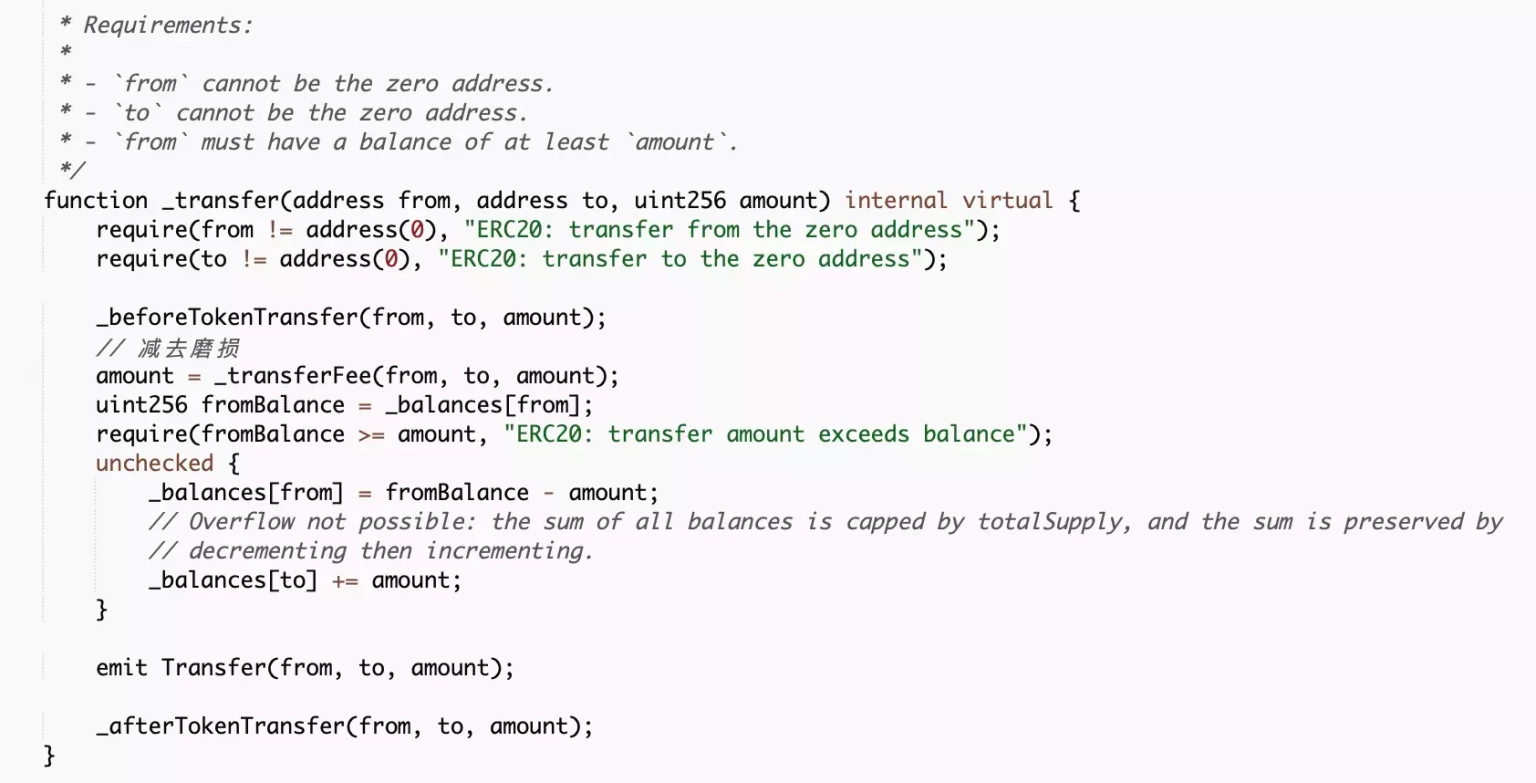
Step 3:
This function further invokes a call to yet another _lpShare function of the contract.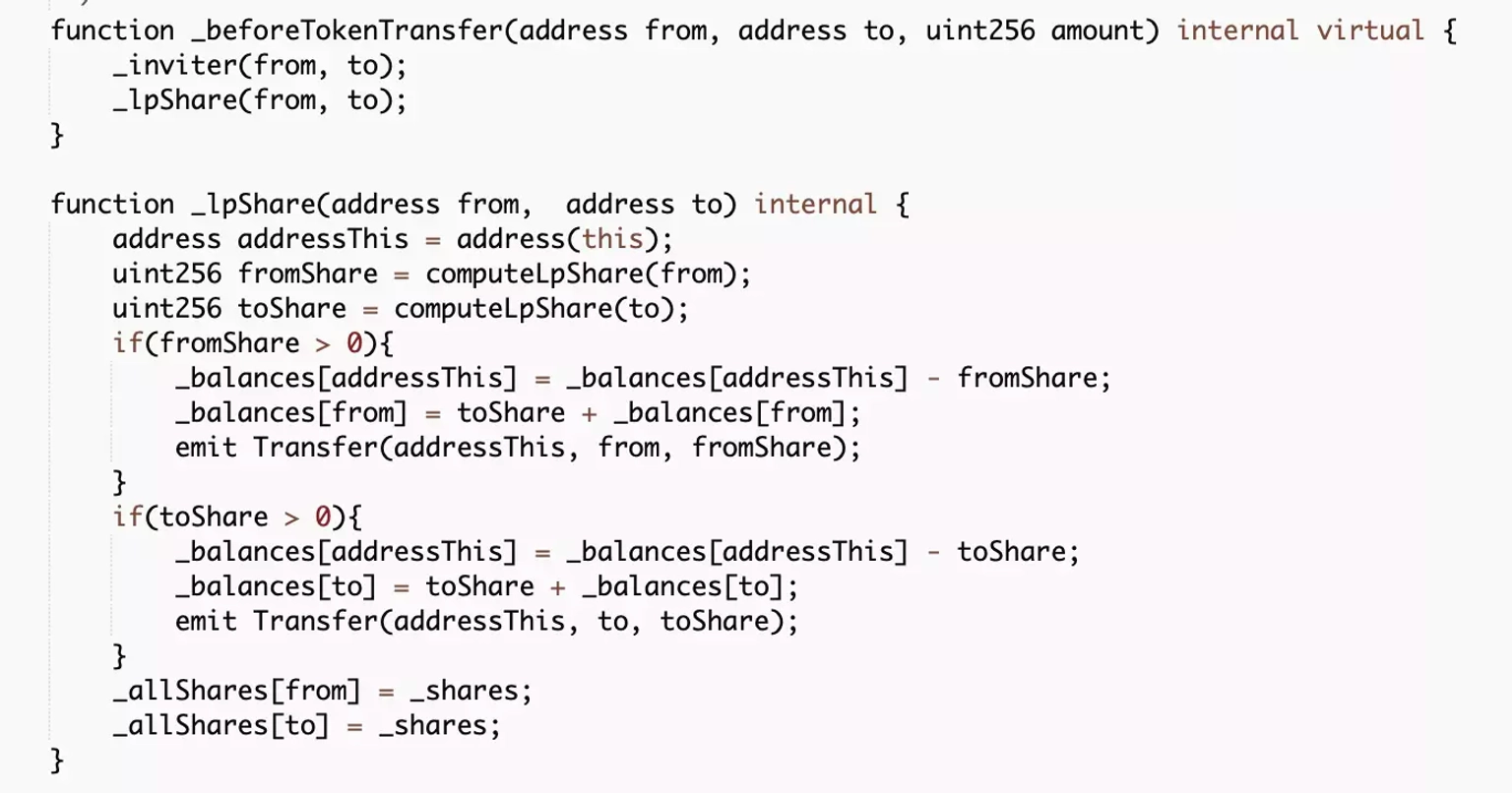
Step 4:
In the transfer logic, the function checks for the sender address in the 'from' parameter, the receiver address in the 'to' parameter, and the corresponding amount to be transferred in the 'amount' parameter.
However, in the lpShare function, the token provides rewards to the LP holders of the BSCUSD-ASKACR pair without checking the transfer amount.
Step 5:
Thus, the exploiter created multiple attack contracts and frequently transferred the liquidity to ensure that the 'to' address holds LP tokens.
Step 6:
The attacker used the same LP tokens and transferred 0 $AASKACR tokens to mint and distribute the $ASKACR tokens to the 'to' address in order to take away their share of profits.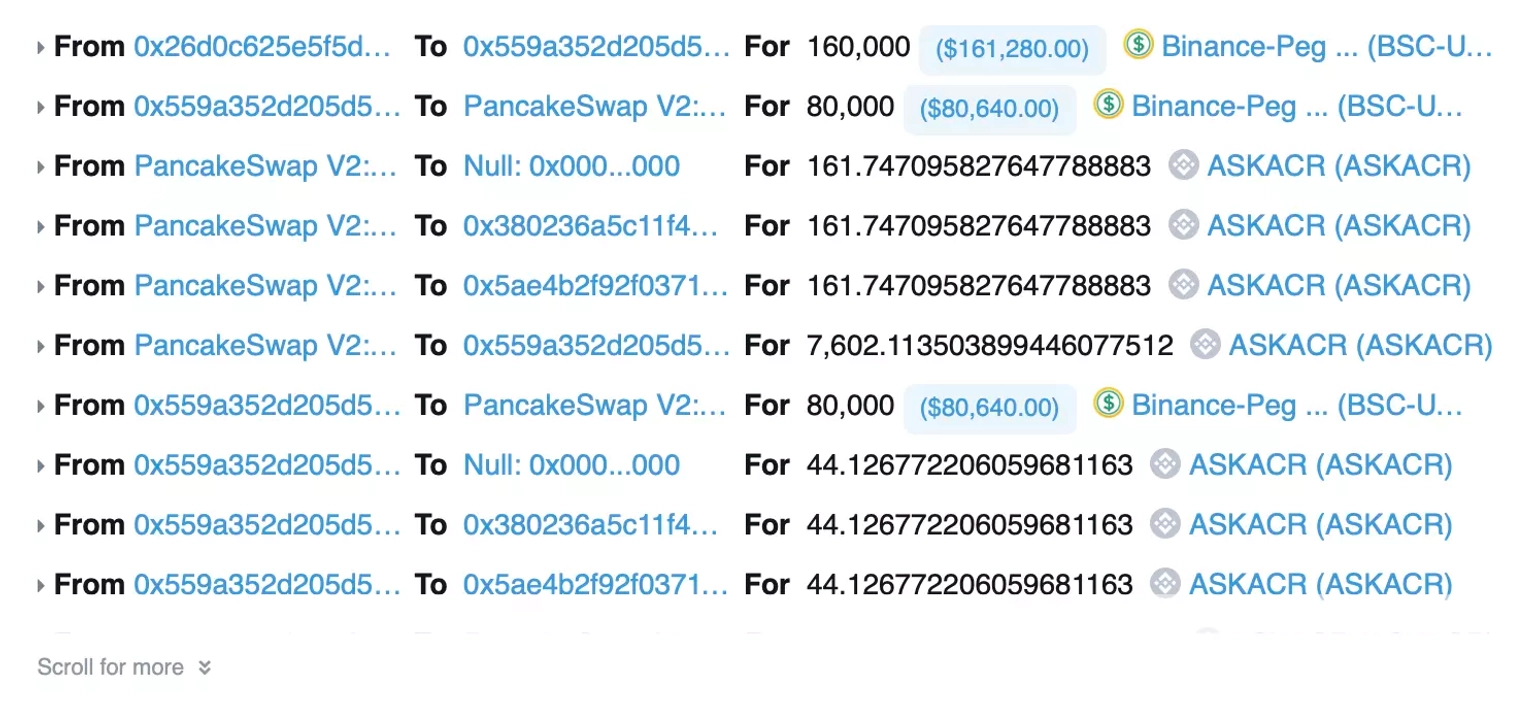
Following the attack, the price of the $ASKACR token dropped by more than 99%.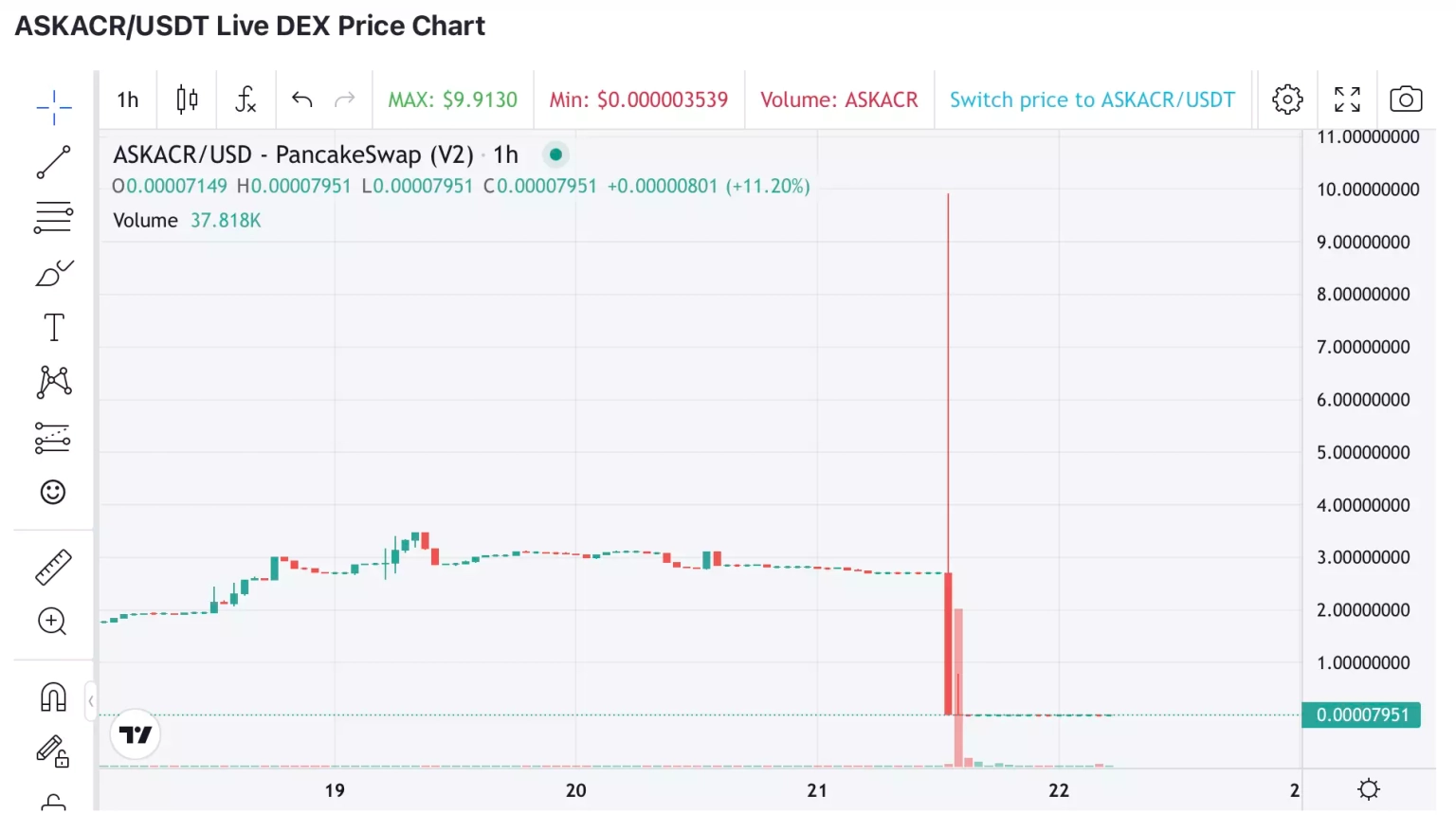
The unfortunate exploit of the ASKACR token on the BNB chain underscores the urgent need for robust, layered security measures in DeFi protocols. The vulnerability lay in the mechanism of distributing rewards, where the token's logic failed to scrutinize the transfer amount during the reward process. This loophole allowed the attacker to mint tokens and pocket profits that weren't rightfully theirs. It's a stark reminder that DeFi, for all its innovations, remains a space fraught with potential pitfalls, especially when it comes to smart contract vulnerabilities.
In scenarios like this, having a cover policy from Neptune Mutual could make a substantial difference. Our platform specializes in providing parametric coverage for precisely these types of smart contract vulnerabilities. Our policies are designed to eliminate the lengthy and cumbersome claims process usually associated with traditional insurance.
Users don't have to provide evidence of their loss to receive payouts; they can claim their insured amount as soon as an incident is officially resolved through our incident resolution system. And given that Neptune Mutual is operational on both Ethereum and Arbitrum, it adds an additional layer of accessibility for diverse DeFi users.
Neptune Mutual's dedicated cover pool could have significantly mitigated the financial impact of the ASKACR exploit. Had the ASKACR team set up a coverage pool with us, token holders affected by the hack could have received immediate payouts to cushion the financial blow. This would have also likely helped maintain some level of trust and confidence among the community, a crucial element that is often overlooked but is essential for any DeFi project's long-term sustainability.
Moreover, our security team would have offered comprehensive evaluations for DNS and web-based security, front-end and back-end security, and intrusion detection and prevention, further reinforcing the platform's overall security posture. In essence, partnering with Neptune Mutual provides a holistic approach to security that combines financial coverage and technical fortification.
Reference Source BlockSec