
Collaboration between Neptune Mutual and SushiSwap
Explore Neptune Mutual's ongoing collaboration with SushiSwap offering several benefits.
Youtube Video
Playing the video that you've selected below in an iframe

Learn more about the various malicious activites, and how to stay safe from them.
Blockchain technology has been one of the biggest disruptive technologies of our time. It utilizes a decentralized model, meaning that control and data storage is done through a distributed ledger network instead of a centralized entity.
Under this model, information is validated through a distributed consensus that compares blocks of data stored in parallel on multiple nodes across the network. This makes it incredibly difficult to tamper with the information stored on the blockchain because any changes must be validated by all the distributed nodes on the network to achieve a consensus. In other words, if you have access to a single block in a blockchain, you cannot edit it without affecting the entire chain, and because of the consensus mechanism that compares blocks stored on different nodes then changing one block won't achieve anything.
However, even though blockchains are inherently secure by virtue of decentralization, the projects that interact with blockchains are still subject to a certain number of cybersecurity risks, and some of these attack vectors will be covered in this article.
Platform-based attacks against the ecosystem of the blockchain-based DeFi ecosystem are becoming more common today. These kinds of attacks make use of flaws in the various web-based content or their frameworks to exploit sensitive data, such as financial or personal information. Hackers are always looking for new methods to take advantage of websites and the visitors to those services. An assault on the domain name server of a website is one of the most prevalent ways.
The Domain Name System (DNS) system converts domain names into IP addresses. When a user enters a URL, their browser queries their Internet Service Provider (a.k.a. ISP) for the site's IP address. When you try to browse a website, your browser automatically goes to its IP address, but the website doesn't know what it's called because it can't connect directly to it. The DNS server looks up which website name is associated with this IP address and returns that information to your browser, allowing it to connect directly to the website without going through your ISP.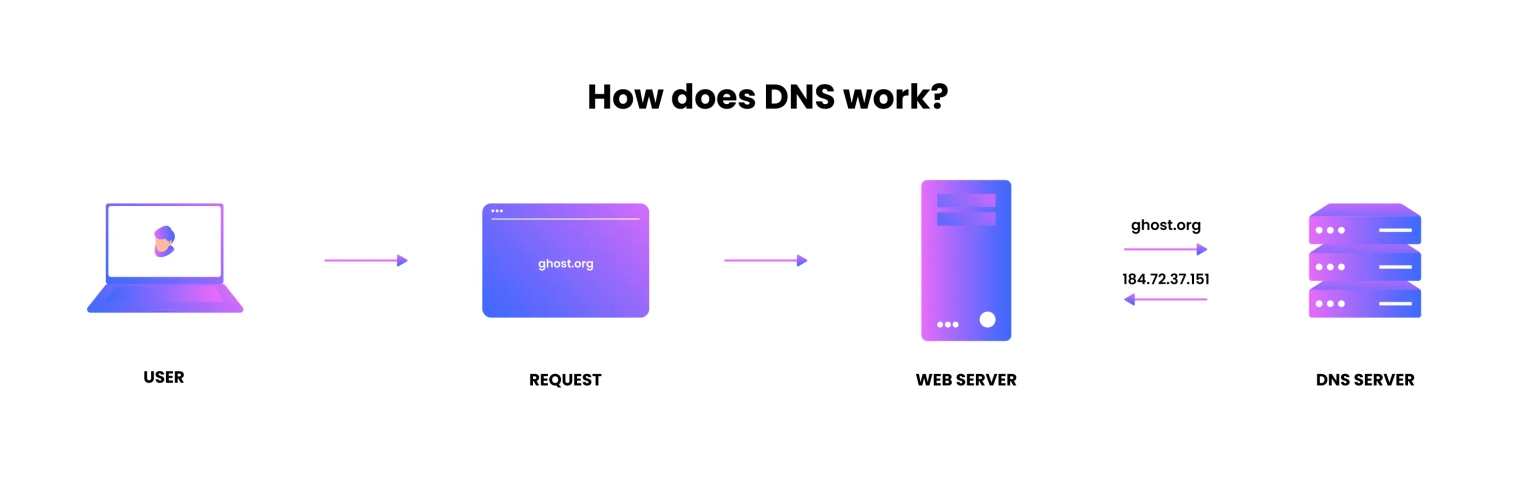
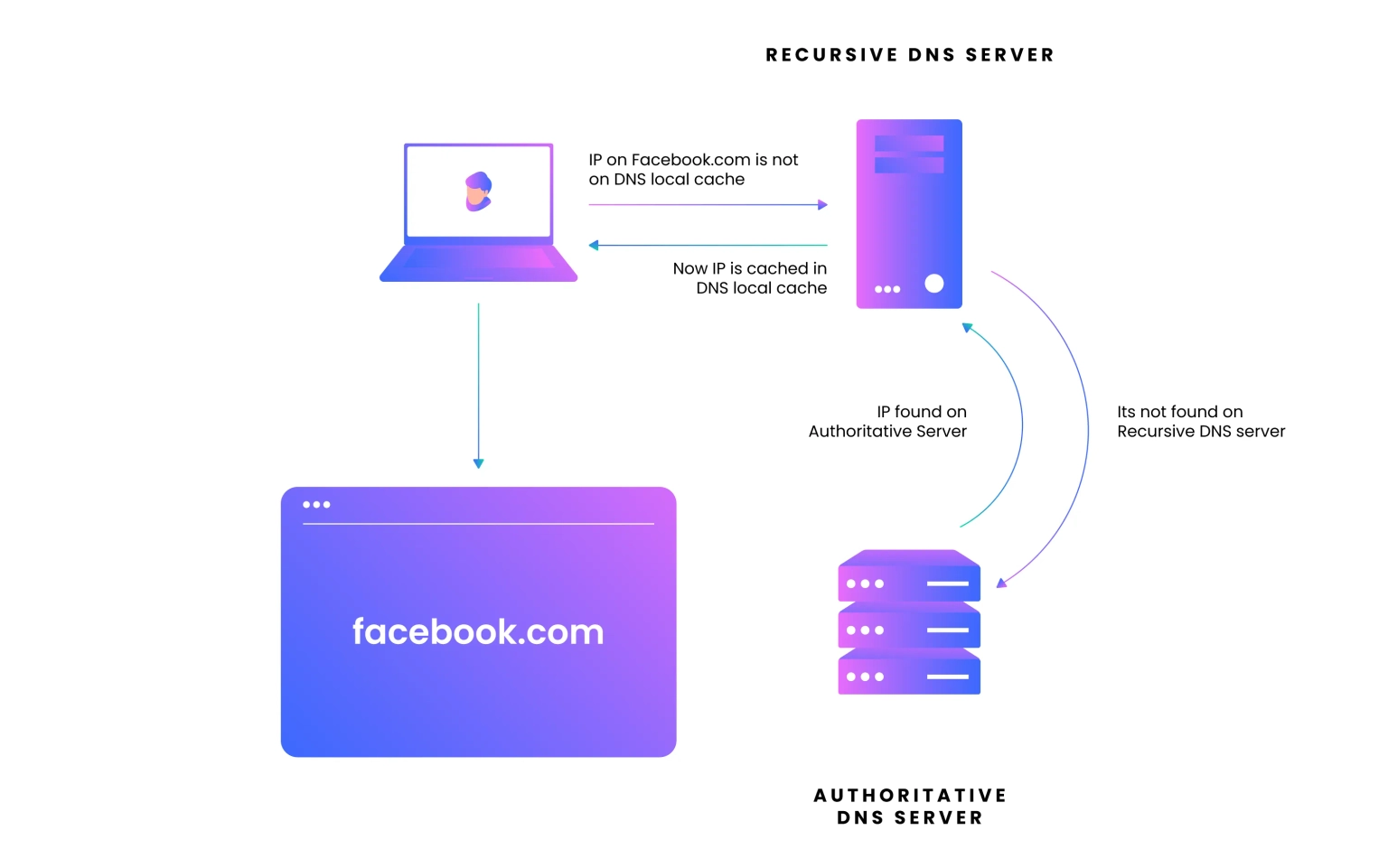
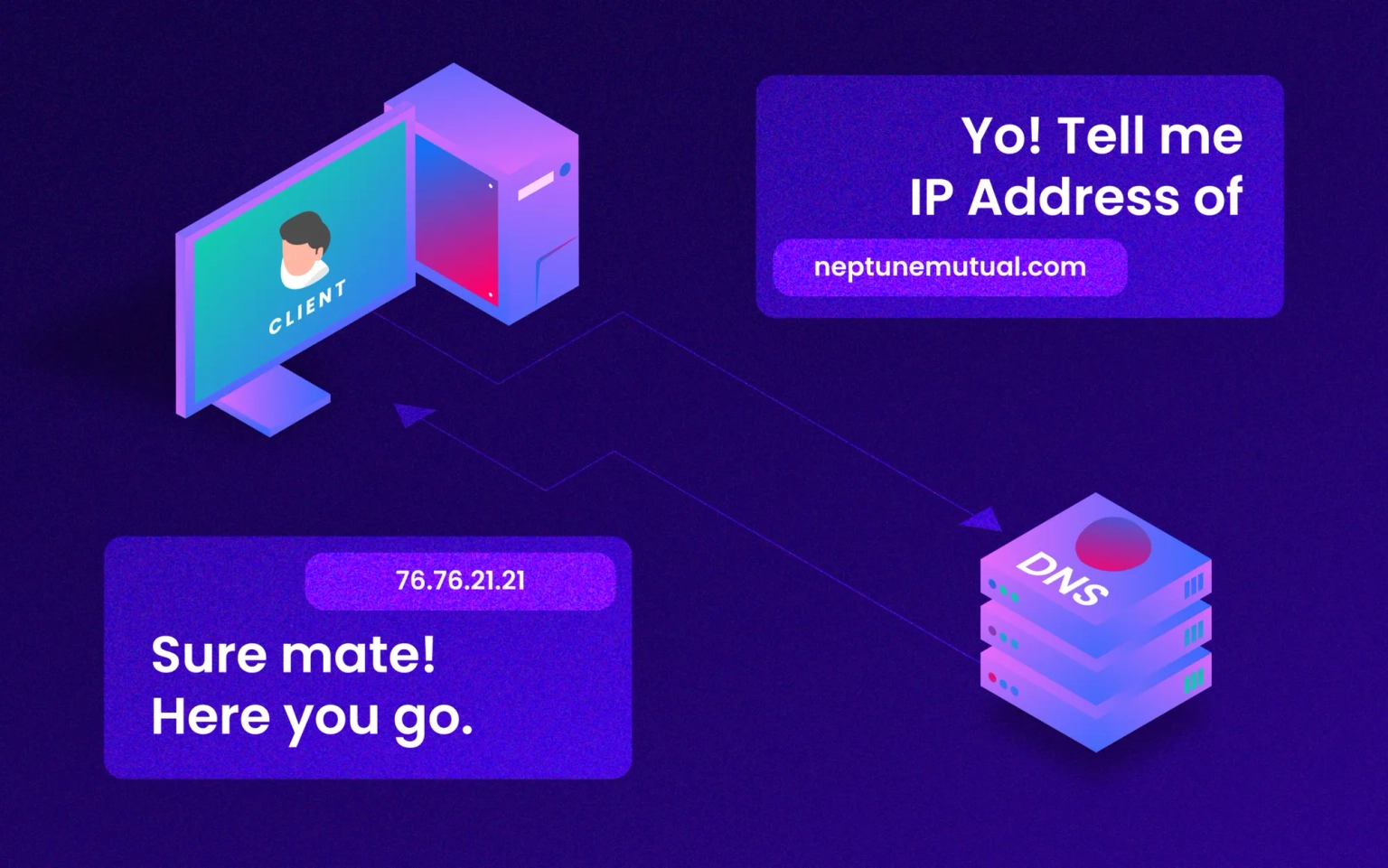
DNS is a hierarchical naming scheme used on the Internet for computers and other Internet-connected devices. It translates human-readable names into the numerical IP addresses that computers use to communicate over the network. A malicious actor attempts to manipulate the domain name system settings on your computer to gain your IP address by modifying what should be displayed when someone types in, say, "neptunemutual.com" instead of "www.neptunemutual.com" into their preferred browser.
When a user requests "neptunemutual.com" via a web browser, the text will be forwarded to this lookup database, which will then determine whether or not "neptunemutual.com" exists. If it does, the database will return its associated IP address, which will be used by the web browser to locate the server hosting the content.
These attack vectors can be briefly described under the some of the following headings:
DNS spoofing, also known as DNS cache poisoning, involves redirecting visitors to a fake website that impersonates the intended destination by using altered DNS records. When users arrive at the fraudulent site, they are prompted to log in to their account, which allows the threat actor to steal access credentials as well as any sensitive information entered into the bogus login form. Furthermore, these malicious websites are frequently infected with viruses or worms on end users' computers, granting the threat actor full access to the machine and its contents.
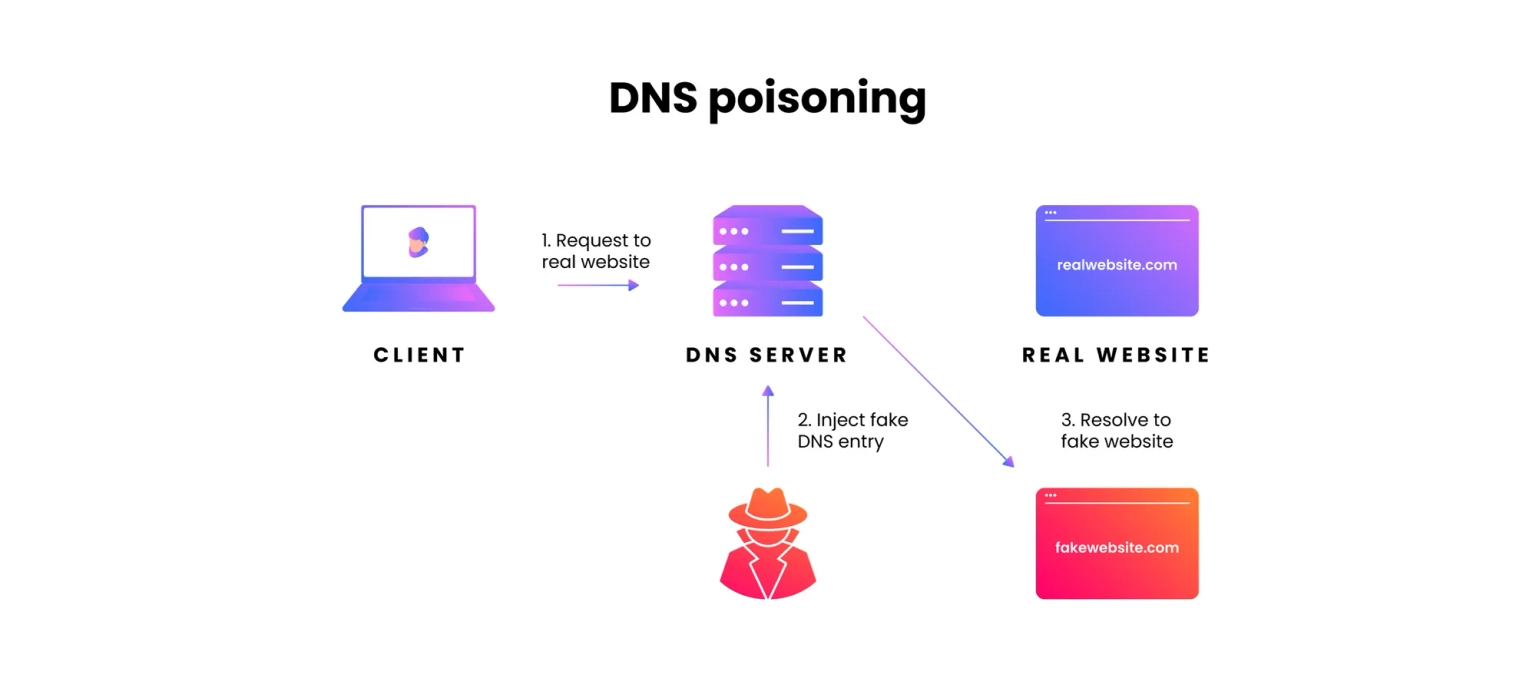
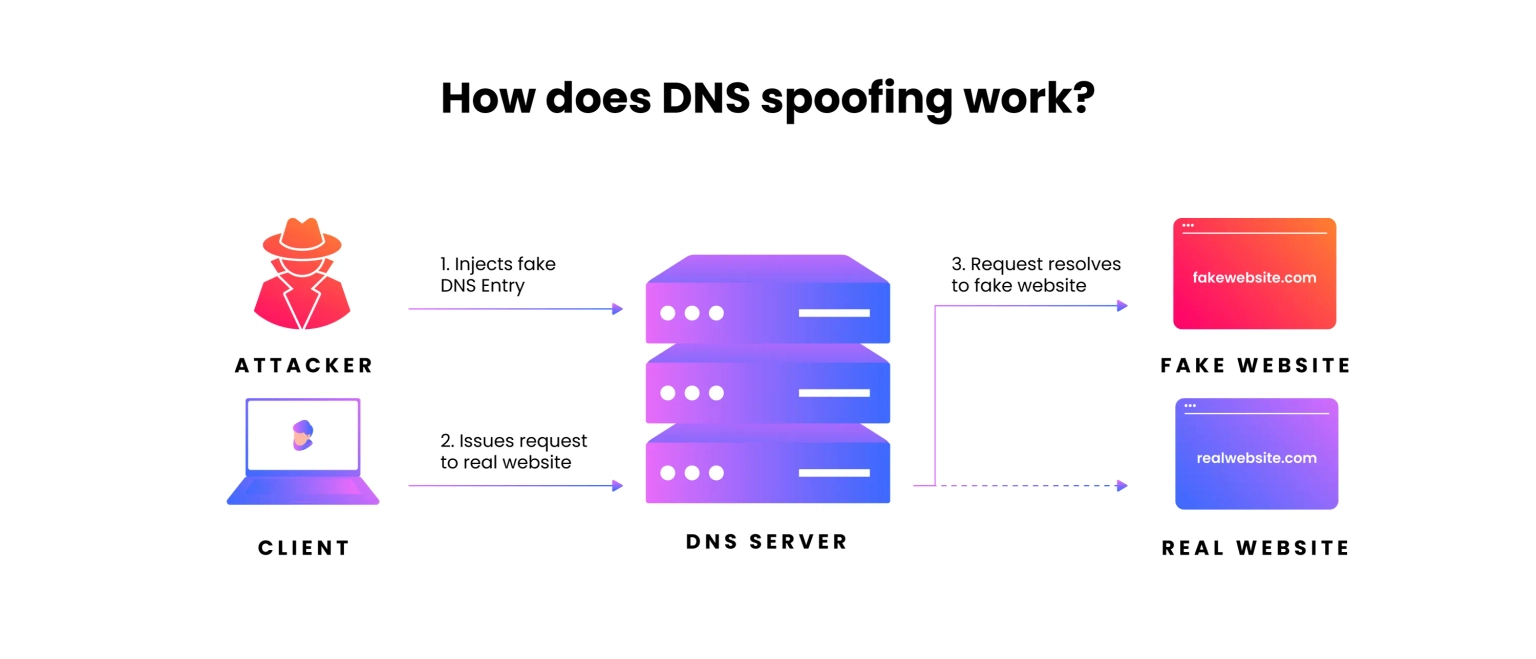
A DNS tunnel can be created by embedding other programs or protocol data in DNS queries and responses. In most cases, the malware comes with data payloads that can compromise a DNS server and grant attackers administrative access to the remote server and any programs running on it. DNS tunneling often relies on the external network connectivity of a compromised system, which provides a way into an internal DNS server with network access.
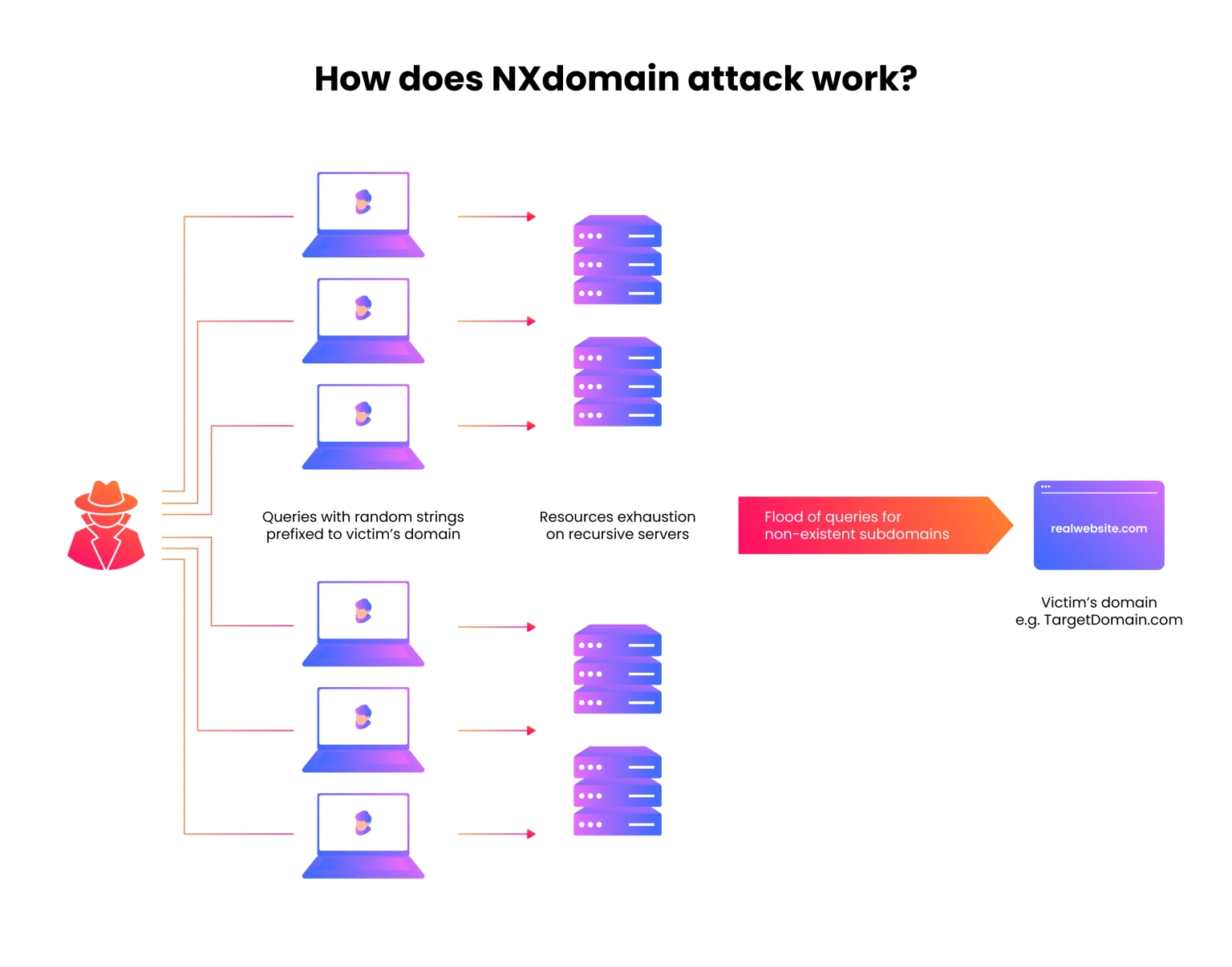
A DNS NXDOMAIN flood DDoS attack tries to overload the DNS server by sending a large number of requests for invalid or non-existent records. DNS proxy servers typically respond to these attacks by repeatedly querying the DNS authoritative server. As a result, both the DNS authoritative server and the DNS proxy server are occupied with invalid requests, causing the response time for valid requests to slow down until it eventually stops altogether.
Our security team at Neptune Mutual can validate your platform for DNS and web-based security, as well as frontend and backend security. We can offer you a solution to scan your platform for known and unknown vulnerabilities that have the potential to have catastrophic long-term effects. Subtle remediation strategies will be outlined in our guidelines, and changes to your existing platform can be adjusted instantly.