
Collaboration between Neptune Mutual and SushiSwap
Explore Neptune Mutual's ongoing collaboration with SushiSwap offering several benefits.
Youtube Video
Playing the video that you've selected below in an iframe

Learn about the workings, types, impacts, and nuances of MEV in the blockchain ecosystem.
Maximal Extractable Value or MEV represents the maximum value that blockchain miners or validators can derive by altering transaction orders during the process of block creation. Initially termed Miner Extractable Value, MEV's name evolved to its current form to better capture its relevance across various blockchain models, including proof-of-work (PoW) and proof-of-stake (PoS) systems.
MEV arises when blockchain actors, such as miners or validators, resequence transactions within a block to their advantage, often at the expense of regular users. These actors possess the authority to determine the order in which transactions are processed on the blockchain. This power, however, can be leveraged for personal financial gain, creating potential ethical and fairness concerns within the blockchain ecosystem.
The Ethereum blockchain is well-known for its highly competitive and adversarial nature. Vulnerable smart contracts within this environment are prime targets for financial exploitation. The growing number of hacks and exploits underscores the intense examination and scrutiny these contracts face from individuals adept at identifying and leveraging weaknesses.
Yet, the intricacies of the mempool eclipse even the challenges of the blockchain. Serving as a repository for pending, unconfirmed transactions, the mempool is an essential but complex component of the blockchain system. If the blockchain is a battleground, the mempool is akin to a much more intimidating and obscure environment—a "dark forest."
In this dark forest of the Ethereum mempool, the most formidable predators are arbitrage bots. These bots relentlessly scan the pending transactions, seeking opportunities to profit. Ari Juels and Lorenz Breidenbach of Chainlink Labs' 2019 research paper, Flash Boys 2.0, goes in-depth on this subject. Their study not only sheds light on Maximal Extractable Value (MEV) and transaction reordering but also emphasizes the significant effects these practices have, such as transaction frontrunning on decentralized exchanges. Remarkably, it's reported that the total MEV extracted on the Ethereum Mainnet before the merge reached a staggering $675,623,114.
Arbitrage bots in the mempool typically focus on certain types of transactions to frontrun, employing complex algorithms to do so. Generalized frontrunners look for any transaction that presents a profitable opportunity, replicating it with their own addresses and executing it. This approach allows them to clone and gain from profitable internal transactions that arise from the transaction's execution trace.
In blockchain networks like Ethereum, an immutable ledger is maintained by a decentralized network of computers or nodes, commonly referred to as block producers. These include miners in Proof of Work (PoW) systems and validators in Proof of Stake (PoS) networks. Their fundamental task involves collecting pending transactions and assembling them into blocks, which are then validated and added to the global ledger. While these networks authenticate all transactions and ensure uninterrupted block production, they do not inherently secure the chronological order of transactions as they are submitted to the blockchain.
Given that each block has a limited capacity for transactions, block producers have the autonomy to choose which transactions from the mempool to include in their block. They typically prioritize transactions offering higher gas prices or transaction fees, as this maximizes their revenue. However, this is a preferential practice rather than a network-enforced rule. As a result, block producers have the liberty to rearrange transactions at their discretion, giving rise to the concept of maximal extractable value.
Contrary to sequencing transactions based on their submission times, block producers usually organize them according to the fees they carry.
Due to the specialized knowledge and expertise required to exploit MEV effectively, many block producers in blockchain networks outsource block construction to third-party entities. This group consists of searchers, builders, and relayers. Searchers scout for MEV opportunities and create bundles of multiple transactions, often incorporating other users' transactions. Builders then take these bundles and construct complete block payloads. Finally, relayers, serving as intermediaries, present these full blocks to the blockchain's block producers. It's crucial to recognize that this is just one of several methods currently employed by block producers to extract MEV, with the ecosystem constantly evolving.
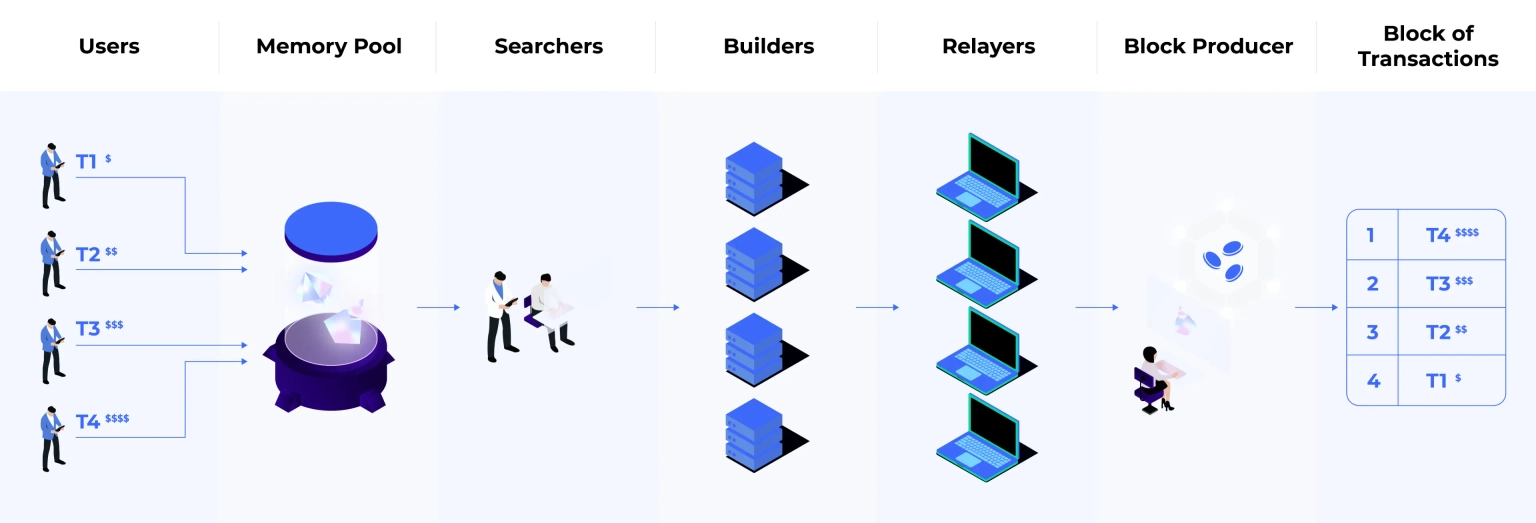
Regrettably, MEV extraction typically occurs at the expense of regular users, often in subtle ways that may not become apparent until after the transaction has been processed. This can lead to users experiencing less favorable trade outcomes, with MEV being directly extracted from their transactions.
Compiling a comprehensive list of MEV extraction methods is challenging due to the evolving nature of the phenomenon and the tendency of searchers to conceal their strategies. However, there are several well-known examples of MEV that can be highlighted.
A sophisticated approach to MEV extraction is generalized frontrunning. In this method, a bot monitors the mempool, submits a duplicate transaction with a higher fee, and replaces the original user's address in the transaction payload with its own. This strategy proved to be particularly effective in a scenario where a generalized frontrunner intercepted and replaced a crucial transaction, thwarting a white-hat hacker's efforts to safeguard vulnerable user funds. These bots don’t analyze the purpose of the transaction; they employ algorithms to modify transactions in the mempool and simulate their execution to identify potential profits.
A direct form of MEV that impacts user experience involves bots executing frontrunning on decentralized exchanges (DEXs). These bots can detect large trades in the publicly visible mempool and act on them.
For example, upon spotting a significant trade, a bot can create a transaction bundle that executes its trade before the user’s transaction. This alters the asset's market price, causing more significant slippage for the user, i.e., a discrepancy between expected and actual trade prices.
After the user's trade executes, causing a further shift in the market price, the frontrunner sells their assets in a backrun trade, completing a sandwich attack. As a result, users experience suboptimal exchange rates, incurring hidden costs on DEXs by receiving fewer tokens than anticipated.
MEV also manifests in bots exploiting price disparities between different DEXs. This arbitrage opportunity emerges when an asset's price on one exchange deviates from another, often due to substantial trades. Bots take advantage of this by buying assets on the lower-priced exchange and selling them on the higher-priced one, effectively equalizing prices and securing profits. This type of arbitrage extends to interactions between on-chain DEXs and off-chain centralized exchanges, as well as across different blockchain networks.
The expansion of decentralized finance and DEX liquidity has increased the frequency and profitability of these arbitrage opportunities, leading to intense competition among bots. These bots engage in bidding wars, continuously raising the fees they offer to block producers to ensure the prioritization of their transaction bundles.
While arbitrage is a common market activity, MEV bots amplify this by monitoring the mempool, replicating trades, and offering higher fees to ensure their transactions are processed first.
MEV contributes to mitigating economic inefficiencies within DeFi protocols. A key example of this is the use of MEV to facilitate rapid liquidations, which are crucial in ensuring that lenders are reimbursed when borrowers' collateralization ratios fall below required thresholds.
Additionally, arbitrage traders who utilize MEV contribute to the alignment of token prices across various decentralized exchanges, reflecting broader market demands. By harnessing MEV for profit maximization, these economically motivated actors can aid in diminishing the inefficiencies of individual protocols, thereby improving the overall efficiency and resilience of the DeFi ecosystem.
Proponents of MEV also argue that it enhances blockchain network security. This is achieved by incentivizing miners or validators to actively participate in the competition for block production, which in turn strengthens the network's overall security and stability.
The adoption of MEV in blockchain networks can have negative implications, particularly impacting the end-user experience. One of the most noticeable effects is seen in scenarios like sandwich attacks on decentralized exchanges. These attacks often lead to substantial slippage during trade executions, creating unfavorable trading conditions for users and potentially eroding trust in the platform.
Another issue stemming from MEV is the increased network congestion caused by generalized frontrunners. These actors often pay higher gas fees to ensure their transactions are prioritized, which can lead to an overall increase in transaction costs for all network participants. This not only raises the cost of participation in the network but can also slow down transaction processing times, affecting the network's efficiency.
A more critical concern is the potential destabilization of the blockchain's consensus mechanism. This can occur when the MEV available to block producers exceeds the block reward. Under these circumstances, block producers might be tempted to reorganize previously confirmed blocks to capture MEV opportunities. Such practices threaten the blockchain's integrity and reliability, as they could lead to double-spending issues and reduce confidence in the network's immutability.