
Analysis of the Curio Exploit
Learn how Curio was exploited, which resulted in a loss of approximately $16 million.
Youtube Video
Playing the video that you've selected below in an iframe

Obridge, a permission-less bridge suffered a typical instance of a contract vulnerability attack.
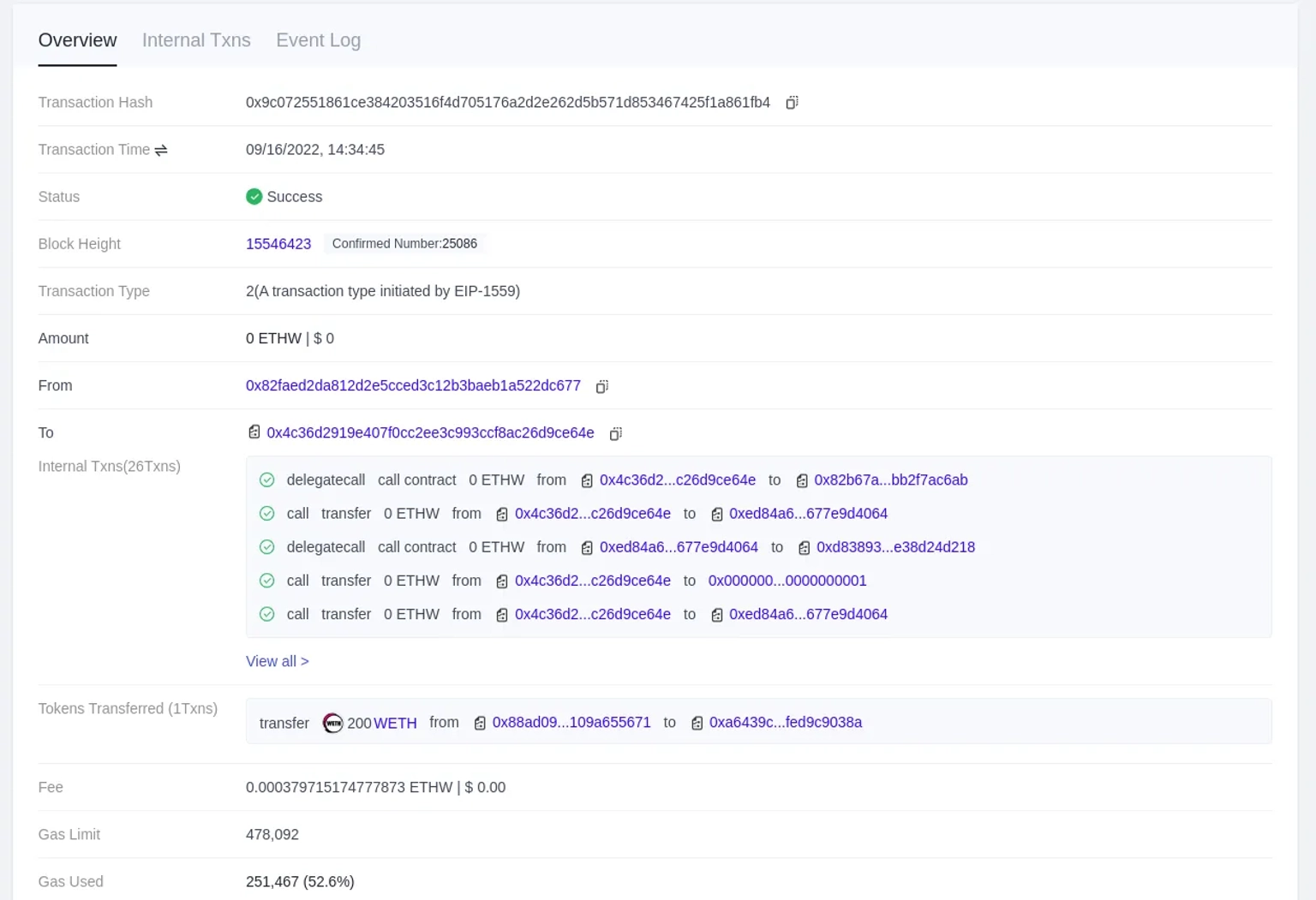
On September 16, 2022, a group of attackers successfully harvested a large amount of ETHW by replaying the PoS chain's message or call-data on EthereumPoW, also known as the PoW chain. The attackers sent 200 WETH through the Omni Bridge before replaying the same message on the PoW chain, earning an additional 200 ETHW.
The Obridge is a decentralized Omni Bridge for the web3 ecosystem. It is a permission-less and pool-less blockchain bridge based on atomic swap contracts.
ETHPoW, the proof-of-work blockchain hard forked from Ethereum, is backed by a group of miners who wanted to keep the PoW chain even after Ethereum’s recent transition to the proof-of-stake (PoS) chain.
Gnosis creates innovative market mechanisms for decentralized finance. Users can securely create, trade, and hold digital assets on Ethereum using their three interoperable product lines.
This is a typical instance of a contract vulnerability attack against a bridge. The fact that the Omni bridge on the PoW chain used the old chainId and did not verify the actual chainId of the cross-chain message was the core cause of the vulnerability.
Step 1:
It was observed from the Omni bridge source code that the logic to verify chainID was present, but the verified chainID used in the contract was pulled from a value stored in the storage named uintStorage.function _isDestinationChainIdValid(uint256 _chainId)
internal returns (bool res) {
return _chainId == sourceChainId();
}
/**
* Internal function for retrieving chain id for the source network
* @return chain id for the current network
*/
function sourceChainId()
public view returns (uint256) {
return uintStorage[SOURCE_CHAIN_ID];
}
Step 2:
Chain IDs, which were created in 2016 to facilitate the hard fork of Ethereum Classic, serve as a fingerprint for a specific network and assist blockchains in confirming the unique identity of on-chain assets.
Step 3:
The chain ID designated by ETHPoWs was discovered to be incorrect, and was apparently already in use by a Bitcoin Cash testnet.
Step 4:
The exploiter took advantage of this situation to first transfer 200 WETH via the Gnosis chain's Omnibridge. The same transaction was then replayed on the PoW chain to obtain an additional 200 ETHW.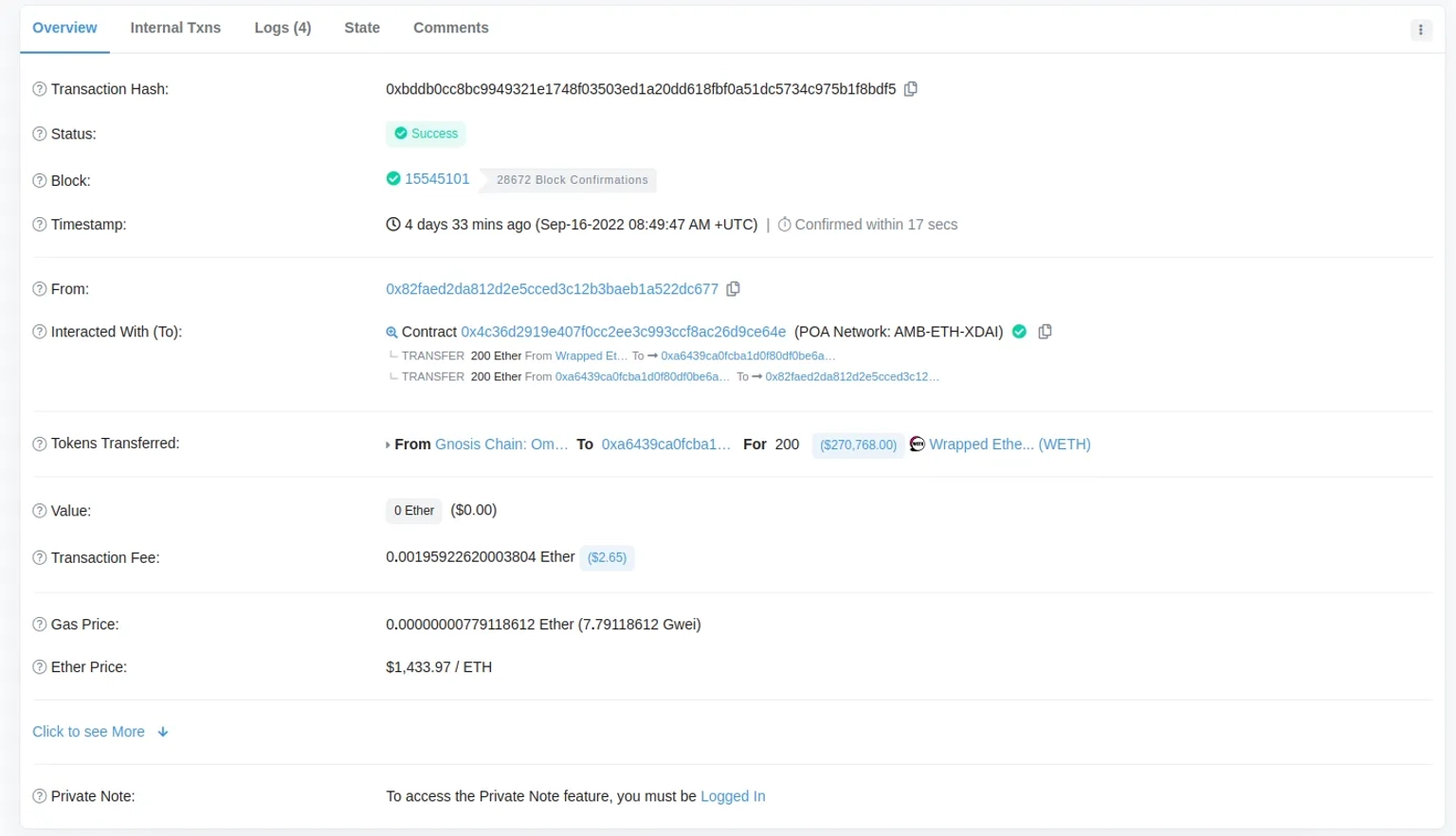
The price of the ETHW token plummeted about 90% on the back of the news.
In order to prevent such an exploit, Solidity developers working on the bridges must correctly verify the actual ChainID of the cross-chain messages.
Our security team at Neptune Mutual can validate your platform for DNS and web-based security, smart contract reviews, as well as frontend and backend security. We can offer you a solution to scan your platform and safeguard your protocol for known and unknown vulnerabilities that have the potential to have catastrophic long-term effects. Contact us on social media if you are serious about security and have the budget, desire, and feeling of responsibility to do so.