
Analysis of the Hedgey Finance Exploit
Learn how Hedgey Finance was exploited, resulting in a loss of assets worth $44.7 million.
Youtube Video
Playing the video that you've selected below in an iframe

How was Thoreum Finance exploited as a result of a smart contract vulnerability?
On January 19, 2023, Thoreum Finance was hacked as a result of smart contract vulnerability, causing the protocol to lose approximately 2260 BNB worth $580,000.
Thoreum Finance is a liquidity mining platform offering static rewards.
The vulnerability is caused by an incorrect implementation of the transfer function in their contract, in which if a wallet sent funds to itself, the amount of tokens in the wallet would be increased by as much as the sent amount.
Step 1:
We took a closer look at one of theattack transactions executed by the exploiter.
Step 2:
It is speculated that the deployer key was compromised, allowing the exploiter to deploy a new contract, before upgrading the proxy contract to the malicious contract.
Step 3:
The attacker deposited BNB in order to obtain $WBNB tokens, utilized a function of the contract to mint $THOREUM tokens, swapped everything on BiSwap, and finally transferred the tokens to themselves.
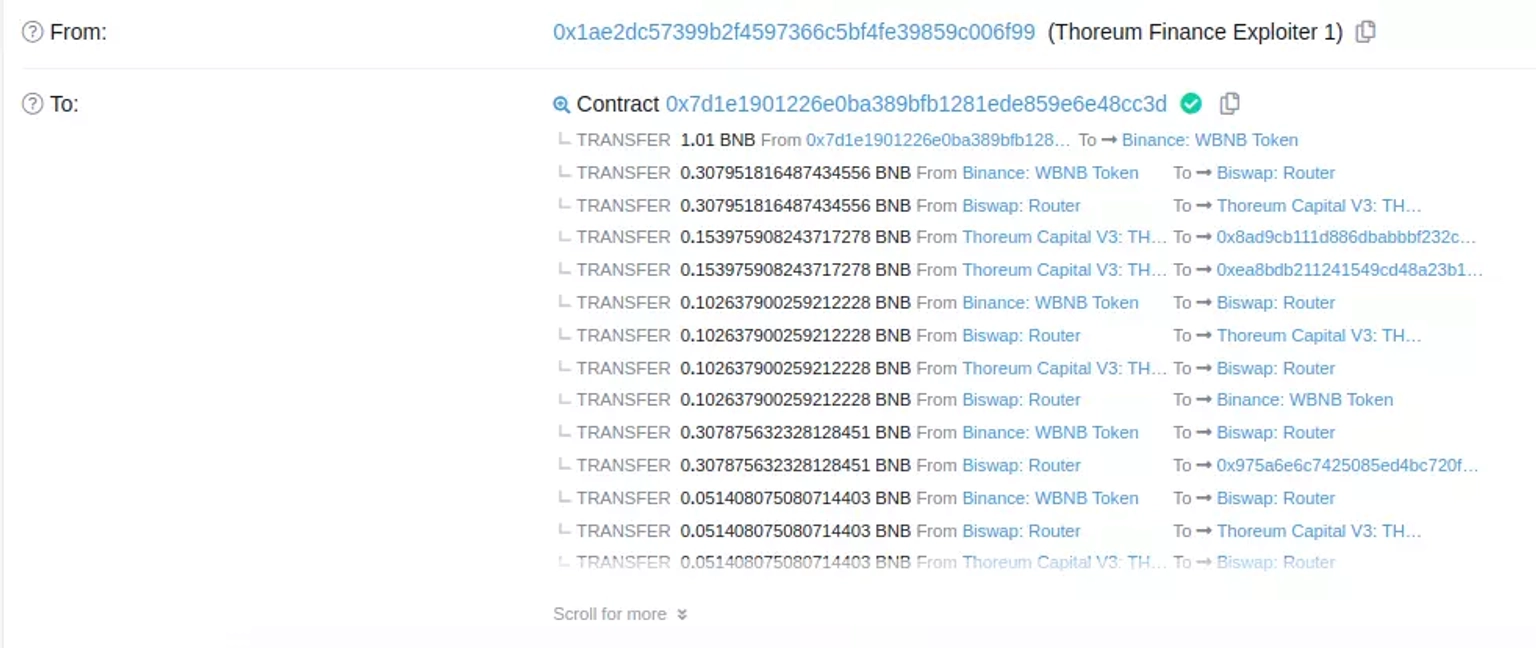
Step 4:
When this exploiter-deployed contract performed a transfer call to itself, its balance grew as a result of the the vulnerable logic in the transfer function.
Step 5:
This procedure was repeated several times after which the contract held more than 500,000 $THOREUM tokens.
Step 6:
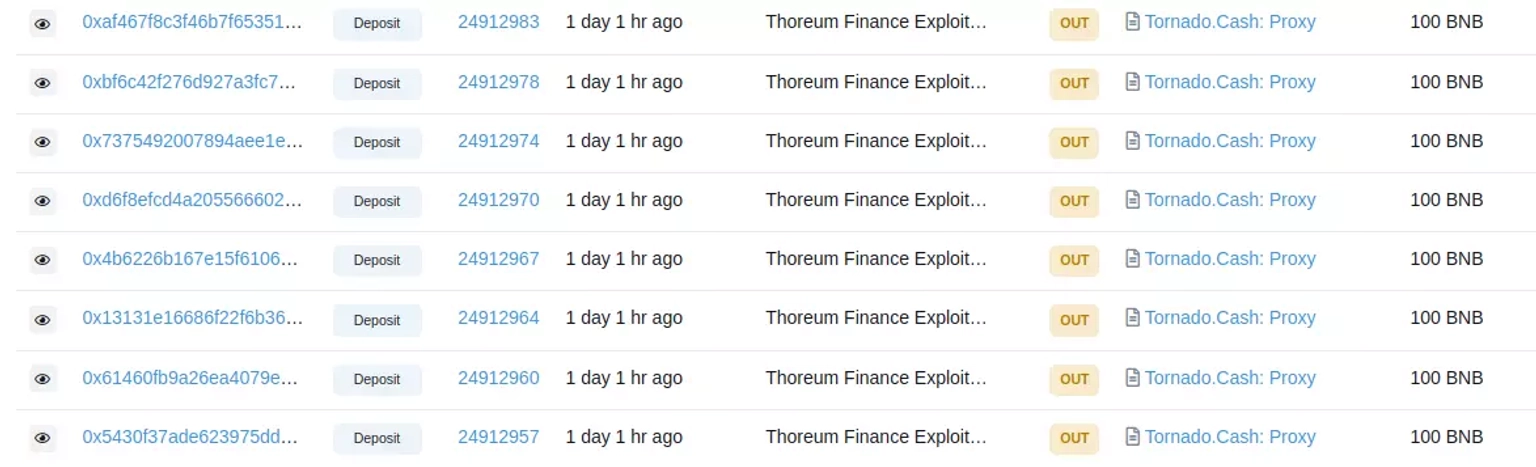
In the same transaction, all of the obtained $THOREUM tokens were converted to $WBNB tokens and sent to this address.
Step 7:
Later, that address transferred about 2250 $BNB tokens to Tornado Cash.
The team had a planned upgrade to their V4 version. During this, they notified their users on Twitter that the V4 of their upgrade is under maintenance due to certain errors.
They had temporarily halted trading in order to investigate and fix the issue, after which trading resumed as usual.
The team later published a detailed post-mortem report of the incident.
The unfortunate hack that targeted Thoreum Finance serves as a stark reminder of the persistent threats lurking in the decentralized finance landscape. This breach highlighted a critical flaw in the implementation of their transfer function. When funds were sent to the same wallet, the tokens within that wallet were mistakenly inflated by the sent amount. This subtle vulnerability allowed the attacker to exploit the protocol repeatedly, amassing over 500,000 THOREUM tokens.
At the heart of such incidents is the urgency for comprehensive security measures that encompass not only robust coding practices but also a safety net for unforeseen pitfalls. In the face of evolving attack vectors, Neptune Mutual stands as a safeguard against potential catastrophes. Had Thoreum Finance opted to integrate a dedicated cover pool within our marketplace, the aftermath of this breach could have been considerably mitigated.
The crux of our offering lies in our specialized parametric cover policies, which ensure that affected parties have a streamlined path to recovery. Users who purchase these policies don't need to provide exhaustive loss evidence to initiate a claim; as soon as an incident is resolved through our governance system, payouts can be swiftly claimed. Our marketplace accessibility on renowned blockchain networks like Ethereum and Arbitrum further underscores our commitment to making this protection widely available.
However, our involvement doesn't merely encompass insurance. Neptune Mutual takes a holistic approach to security, evaluating platforms for vulnerabilities through our seasoned security team. From DNS and web security checks to advanced intrusion detection and prevention, our comprehensive evaluation process ensures that platforms are fortified against potential threats.
Thoreum Finance's quick response and post-mortem analysis reveal the dedication of teams in this space to rectify and learn from such breaches. However, proactive measures are equally crucial. The value of employing hardware wallets, multi-signature wallets, and cold storage strategies for securing private keys offline and mitigating risks cannot be understated.
Reference Source Ancilia