
Understanding the Grand Base Exploit
Learn how Grand Base was exploited, resulting in a loss of assets worth $2.5 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how SafeMoon was exploited which resulted in a loss of approximately $8.65 million.
On March 28, 2023, SafeMoon was exploited due to a smart contract vulnerability, resulting in a loss of approximately $8.65 million.
SafeMoon is working on building blockchain, NFT, and metaverse products to get more value out of the underlying crypto technology.
The root cause of the vulnerability is due to the presence of a public burn function.
Step 1:
The most recent change to the SafeMoon token contract added the burn function, along with four other functions. It was updated yet again to allow anyone to burn tokens instead of the sender.
Step 2:
The attack was initiated by the SafeMoon Deployer. So it is likely that the private keys of their contract deployer were compromised.
Step 3:
We attempted to analyze the attack transaction executed by the exploiter.
Step 4:
The exploiter took advantage of the public burn function, which allows any user to burn tokens from any other address.
function burn(address from, uint256 amount) public {
_tokenTransfer(from, bridgeBurnAddress, amount, 0, false);
}Step 5:
Thus, the attacker was able to remove SFM tokens from the SafeMoon-WBNB LP, alleviate the price of SFM tokens, and sell them at a grossly overpriced rate within the same transaction, which ultimately wiped out the remaining WBNB in the liquidity pool.
Step 6:
The attack was front-run by a MEV bot, who has since transferred approximately 27,380 $BNB worth $8.65 million to this address.
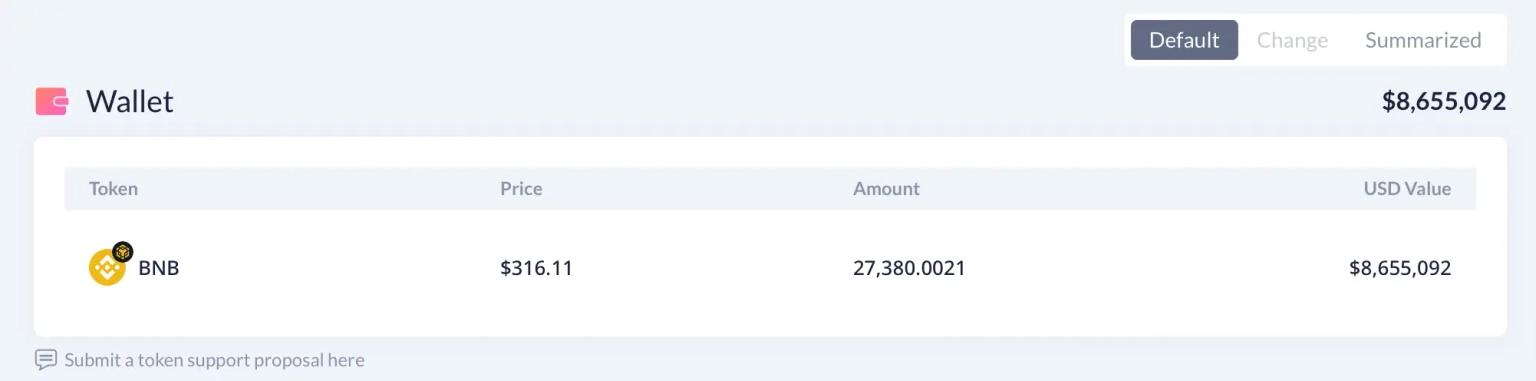
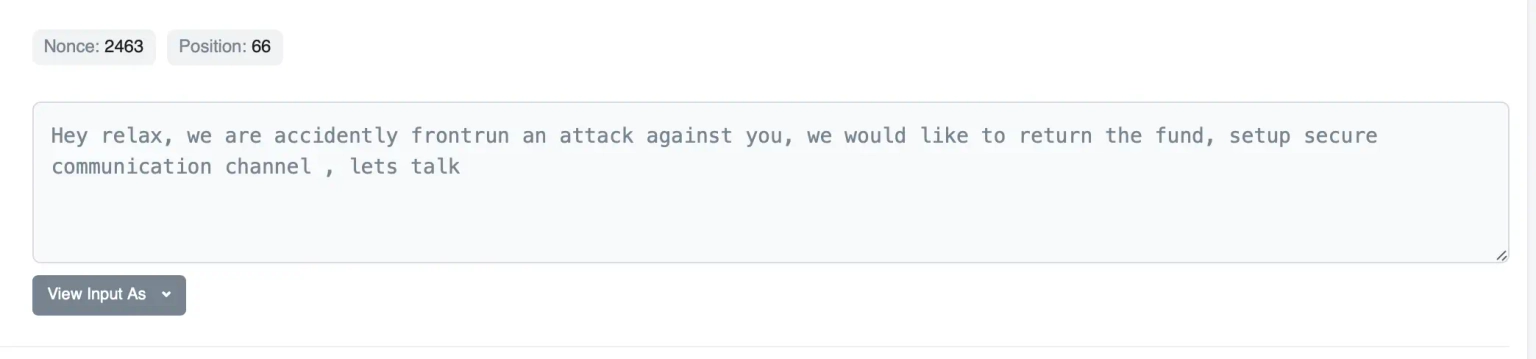
Step 7:
The exploiter further mentioned that they are waiting for the setup of a secure communication channel to return the funds back to the team.
After the attack, the team acknowledged its occurrence, indicated that it had an impact on the SFM:BNB LP pool, and assured everyone that their DEX were safe.
They further added that the team had a meeting with their key advisors to come up with a strategy for safeguarding token holders and the community as a whole. The team has patched the vulnerability and is working with a chain forensics consultant to identify the precise nature and scope of the attack after it appears that the vulnerability has been addressed.
The exploit on SafeMoon highlights the critical importance of security measures in DeFi protocols. The public burn function, added in the recent change to the SafeMoon token contract, was exploited, illustrating how new features can sometimes bring unforeseen vulnerabilities. As security experts at Neptune Mutual, we believe this incident could have been mitigated and the impact significantly reduced with robust security measures and protocols.
Firstly, the importance of regular smart contract audits cannot be overstated. Independent third-party auditors can identify vulnerabilities like the one exploited in this attack and recommend ways to mitigate them. In the SafeMoon incident, an audit could have flagged the potential dangers of the public burn function.
In addition, formal verification tools can ensure that a smart contract behaves as intended, detecting issues that might be overlooked manually. These tools could have alerted SafeMoon to the risks associated with allowing anyone to burn tokens from any address.
Security also extends to the handling of private keys, as it appears likely that the private keys of SafeMoon's contract deployer were compromised. Best practices such as using hardware wallets for offline private key storage, employing multi-signature wallets, and utilizing cold storage methods could help protect against such scenarios.
These measures, while vital, are not foolproof, and this is where we at Neptune Mutual come in. Had SafeMoon established a dedicated cover pool in our marketplace, the aftermath of the attack could have been much less severe. We offer parametric policies to cover losses stemming from smart contract vulnerabilities. Users do not need to provide loss evidence to receive payouts, and claims can be made as soon as an incident is resolved through our system.
Our marketplace operates on Ethereum and Arbitrum, two major blockchain networks, ensuring broad coverage for DeFi users. Furthermore, our security team assesses platforms for potential vulnerabilities across several areas, such as DNS and web-based security, frontend and backend security, and intrusion detection and prevention, providing an additional level of protection.
Reference Source BlockSec