
Analysis of the Hedgey Finance Exploit
Learn how Hedgey Finance was exploited, resulting in a loss of assets worth $44.7 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how Allbridge was exploited which resulted in a loss of approximately $570,000.
On April 01, 2023, Allbridge was exploited due to price manipulation, resulting in the loss of 282,889 $BUSD and 290,868 $USDT, totaling approximately $570,000.
Allbridge is a bridge between EVMs like BNB-Chain, Ethereum, and Polygon and non-EVM compatible blockchains like Solana.
The root cause of the exploit is due to the manipulation of the swap price of their pool. The exploiter played the dual role of a swapper and liquidity provider to manipulate the price and then proceeded to drain the funds from the pool.
Step 1:
We attempted to analyze the attack transaction executed by the exploiter. This exploit was carried out by the hacker who had previously attacked UF Dao protocol.
Step 2:
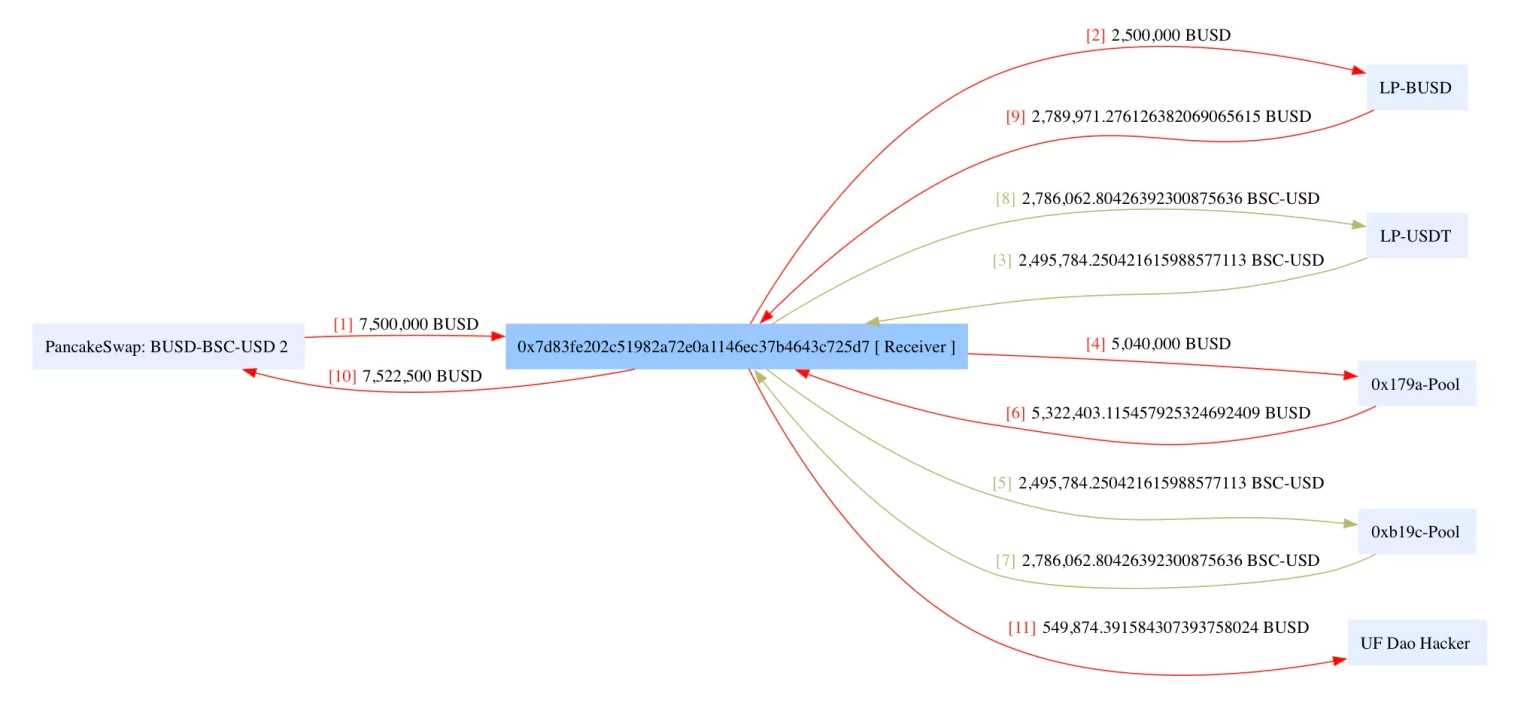
The attacker initially took a flash loan of 7.5 million $BUSD from PancakeSwap, swapped 2 million $BUSD for BSC-USD, and deposited 5 million to the $BUSD pool.
Step 3:
The exploiter then swapped the remaining 500K $BUSD for BSC-USD and used the balance to swap for $BUSD again in the Allbridge's Bridge contract, which resulted in a high dividend for the earlier liquidity deposit.
Step 4:
The BUSD liquidity in the pool was withdrawn to receive 4,830,999 $BUSD as the principal investment and a 554 $BUSD reward.
Step 5:
The attacker was then able to swap out $790,000 of BSC-USD from Bridge using only $40,000 of BUSD and further withdraw 1,995,193 $USDT from the $USDT pool. Then, the attacker swapped out 2,786,062 $USDT for 2,789,971 $BUSD, repaid the flash loan, and kept the remaining balance for profits.
Step 6:
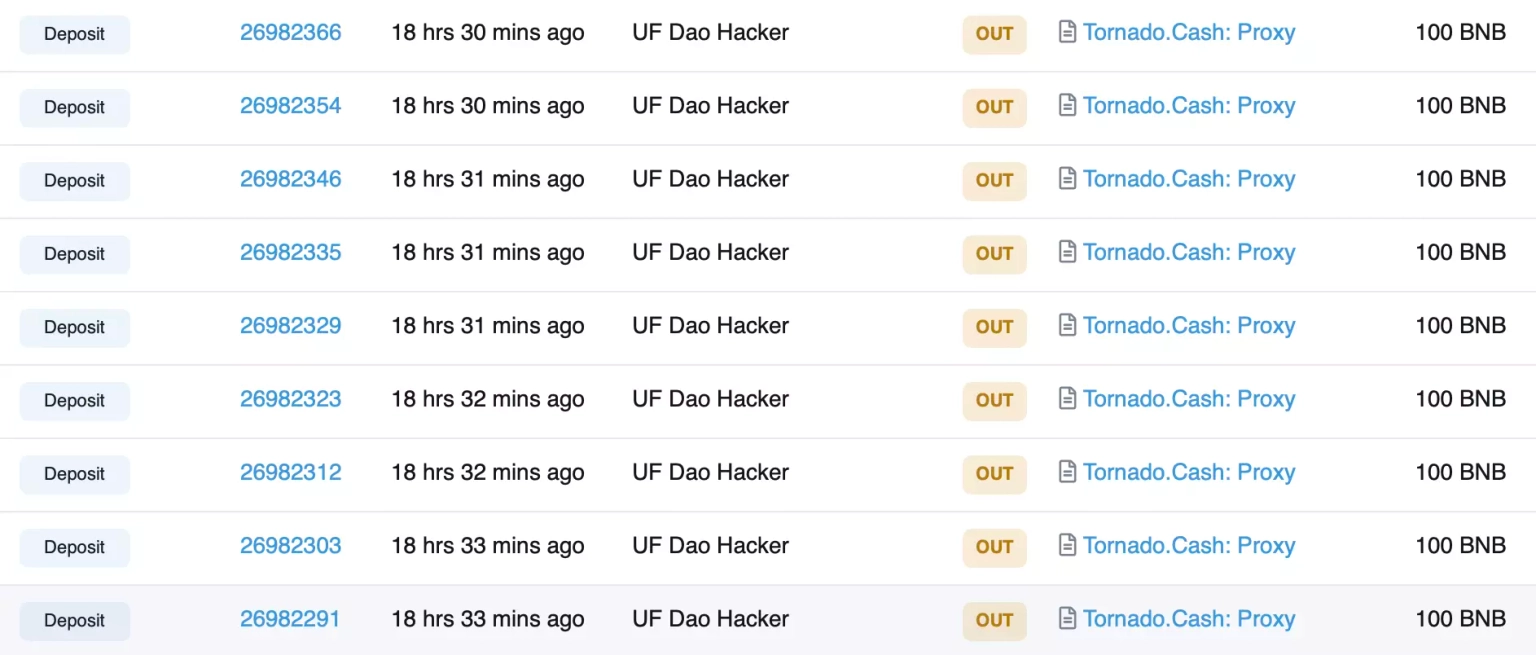
The exploiter later sent 1,700 BNB, which also included profits from previous attacks, to Tornado Cash.
Following the attack, the team acknowledged the incident and temporarily shut down the bridge.
A later post-mortem report by the team stated that the exploit targeted their BUSD/USDT pools on BNB Chain, and they have proposed a white-hat bounty for the recovered assets.
The attack on Allbridge underscores the necessity of sophisticated and robust security measures for DeFi protocols. This exploit saw an attacker manipulate the swap price of their pool and subsequently drain funds. Such an attack could have been mitigated or prevented with the proper security safeguards in place.
Regular smart contract audits by independent third parties are crucial as part of a comprehensive security strategy. These audits can help identify potential vulnerabilities, such as price manipulation susceptibilities, and propose ways to rectify them before attackers can exploit them.
Beyond the audit stage, DeFi protocols should take precautionary measures to prevent price manipulation. Measures such as oracle systems and time-weighted average prices (TWAPs) can help to maintain price stability and prevent malicious actors from being able to drastically manipulate prices to their advantage.
Even with the best security measures in place, vulnerabilities may still be exploited. That's where we at Neptune Mutual can provide a safety net. If Allbridge had set up a dedicated cover pool in our marketplace prior to this attack, the impact could have been significantly reduced. At Neptune Mutual, we offer parametric insurance policies designed to cover losses stemming from smart contract vulnerabilities.
For users who have suffered a loss of funds due to such vulnerabilities, our policies do not require evidence of loss to receive payouts. As soon as an incident is resolved through our incident resolution system, users can claim their payouts. Currently, our marketplace operates on two leading blockchain networks: Ethereum and Arbitrum, thus providing broad coverage for DeFi users.
In addition, our security team would have evaluated the Allbridge platform for potential vulnerabilities in several areas, including DNS and web-based security, frontend and backend security, and intrusion detection and prevention. This comprehensive approach can help identify and address potential attack vectors, offering an extra level of protection.
Reference Source CertiK