
Understanding the Grand Base Exploit
Learn how Grand Base was exploited, resulting in a loss of assets worth $2.5 million.
Youtube Video
Playing the video that you've selected below in an iframe

Learn how 0vix Protocol was exploited, resulting in a loss of approximately $2 million.
On April 28, 2023, the 0vix Protocol on the Polygon chain was exploited, resulting in a loss of approximately $2 million.
0VIX is a DeFi liquidity market protocol, built on Polygon, that enables users to lend, borrow and earn interest with their digital assets.
The root cause of the vulnerability is due to the flawed price calculation of GHST token.
Step 1:
The debt value `ovGHST` in the contract is calculated based on the balance of the GHST token in the contract vGHST. The exploiter was able to manipulate the conversion ratio of the `vGHST` by transferring large amounts of $GHST tokens directly to the `vGHST` contract.
Step 2:
We attempted to analyze the attack transaction executed by the exploiter.
Step 3:
The attacker took a large amount of flash loan using GHST tokens, and used them to mint $vGHST tokens.
Step 4:
The exploiter took another flash loan of approximately 24.5 million $USDC, and used roughly 6.15 million USDT as collateral for deposit to borrow $vGHST assets from 0VIX pools, and repeated the process to create a debt position.
Step 5:
They then self liquidated their vGHST debt to get back their collateral of USD while also keeping the USD they borrowed safe, hence leaving the account with bad USD debt.
Step 6:
In the end, the attacker took their the collateral and redeem vGHST tokens to $GHST, while all the borrowed assets during the flash loan are paid back keeping the remaining assets as profits.
Step 7:
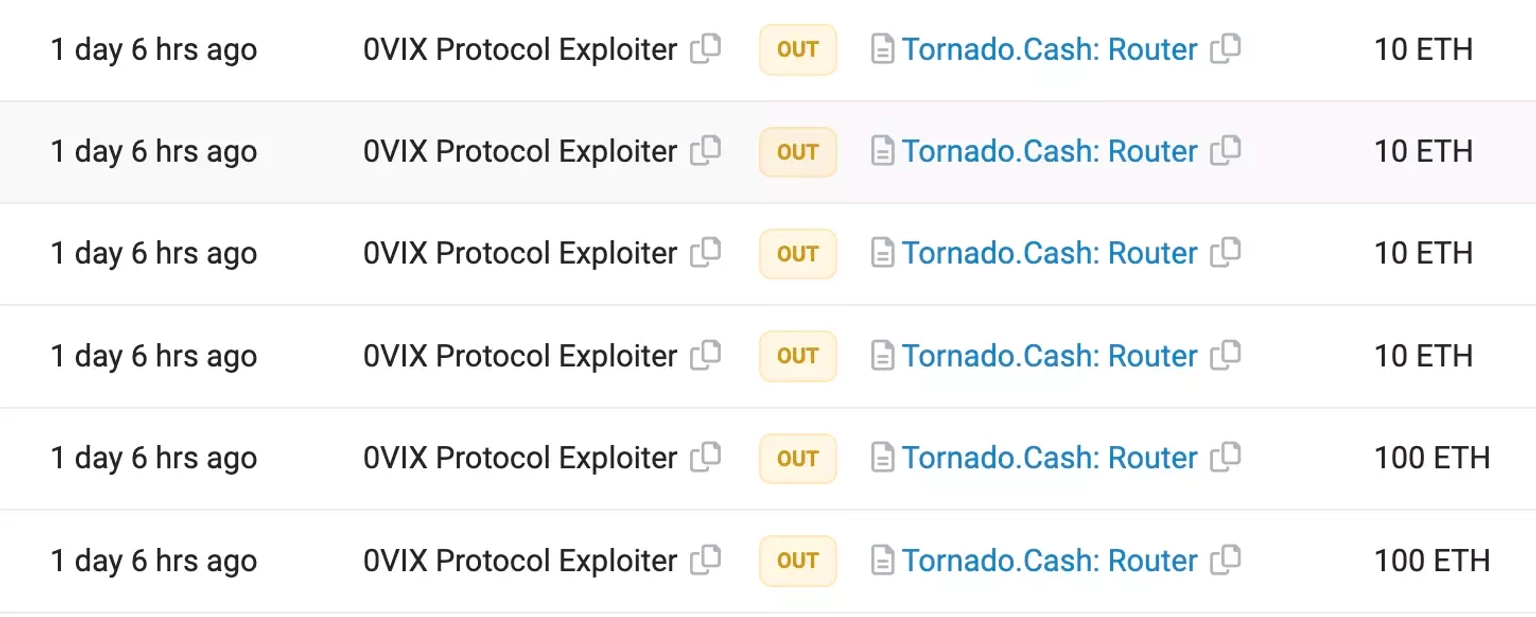
The stolen funds include 1.453 million $USDC, 584,444 $USDT, and 9565 $GHST, totaling approximately $2.048 million. Funds worth approximately 760 ETH were transferred to Tornado Cash, whilst the remaining stolen assets are held at this address.
The team acknowledged the occurrence of the incident via this tweet. They stated that the POS and zkEVM markets have been paused, which includes pausing oToken transfers, minting, and liquidations; however, only the POS markets were affected due to the exploit.
The team has been in touch with Chainalysis and PeckShield to investigate the exploit. They have also sent an on-chain message to the attacker, offering them 10% bounty rewards for returning the rest of the stolen funds.
A later tweet mentioned that the law enforcement process has begun due to the absence of funds being returned.
The successful exploit of the 0vix Protocol was a direct result of price manipulation that arose from the attacker's ability to exploit a donation-debt position. The protocol's dependence on the current token balance for price determination was the crux of the problem. Applying a price oracle with proper data sources or an independent audit of the price calculation method could have significantly mitigated the risk of such an exploit.
However, even with the best security measures, no system can ever be 100% secure. This is where the crucial role of protocols such as Neptune Mutual comes in.
Neptune Mutual offers parametric coverage policies to users. These policies could have significantly reduced the financial impact on affected users from this exploit. If the team behind 0vix Protocol had pre-emptively established a dedicated cover pool with Neptune Mutual, users who suffered losses due to this exploit could have been compensated without needing to provide evidence of their losses. This immediate compensation helps users recover quickly from unforeseen financial shocks, enhancing the robustness and resilience of the DeFi ecosystem.
Moreover, Neptune Mutual goes beyond providing such coverage. They also include a security team that conducts evaluations of the platform for various potential vulnerabilities, including DNS and web-based security, frontend and backend security, and intrusion detection and prevention. Had 0vix Protocol utilized Neptune Mutual's comprehensive security evaluation, this exploit might have been caught and rectified before it was used to siphon off assets.
Finally, it's worth noting that the marketplace of Neptune Mutual is available on Ethereum and Arbitrum, two popular blockchain networks, making it easily accessible for a wide variety of projects. Integrating Neptune Mutual's coverage into their security infrastructure should be an important consideration for all DeFi protocols looking to enhance user protection and trust.
Reference Source PeckShield