
Analysis of the Hedgey Finance Exploit
Learn how Hedgey Finance was exploited, resulting in a loss of assets worth $44.7 million.
Youtube Video
Playing the video that you've selected below in an iframe

Skyward Finance experienced a vulnerability exploit and lost over 1.08 million Near tokens.
On November 02, 2022, Skyward Finance experienced a vulnerability exploit and lost over 1.08 million $NEAR tokens worth approximately $3.2 million.
Skyward Finance is an on-chain asset issuance IDO platform that facilitates price discovery and equitable token distribution on the NEAR protocol.
The vulnerability was caused by a lack of check and parameter validation in one of the smart contract's functions.
Step 1:
In the exploit transaction, the hacker effectively withdrew wrap.near tokens multiple times within one transaction.
Step 2:
The exploiter purchased a large quantity of $SKYWARD tokens on Ref Finance before redeeming them on Skyward Finance via Treasury.
Step 3:
The vulnerability existed in the contract's redeem_skyward function, which is used to redeem the treasury from the protocol.
Step 4:
This function did not validate whether the passed in values of token_account_ids are duplicate entries.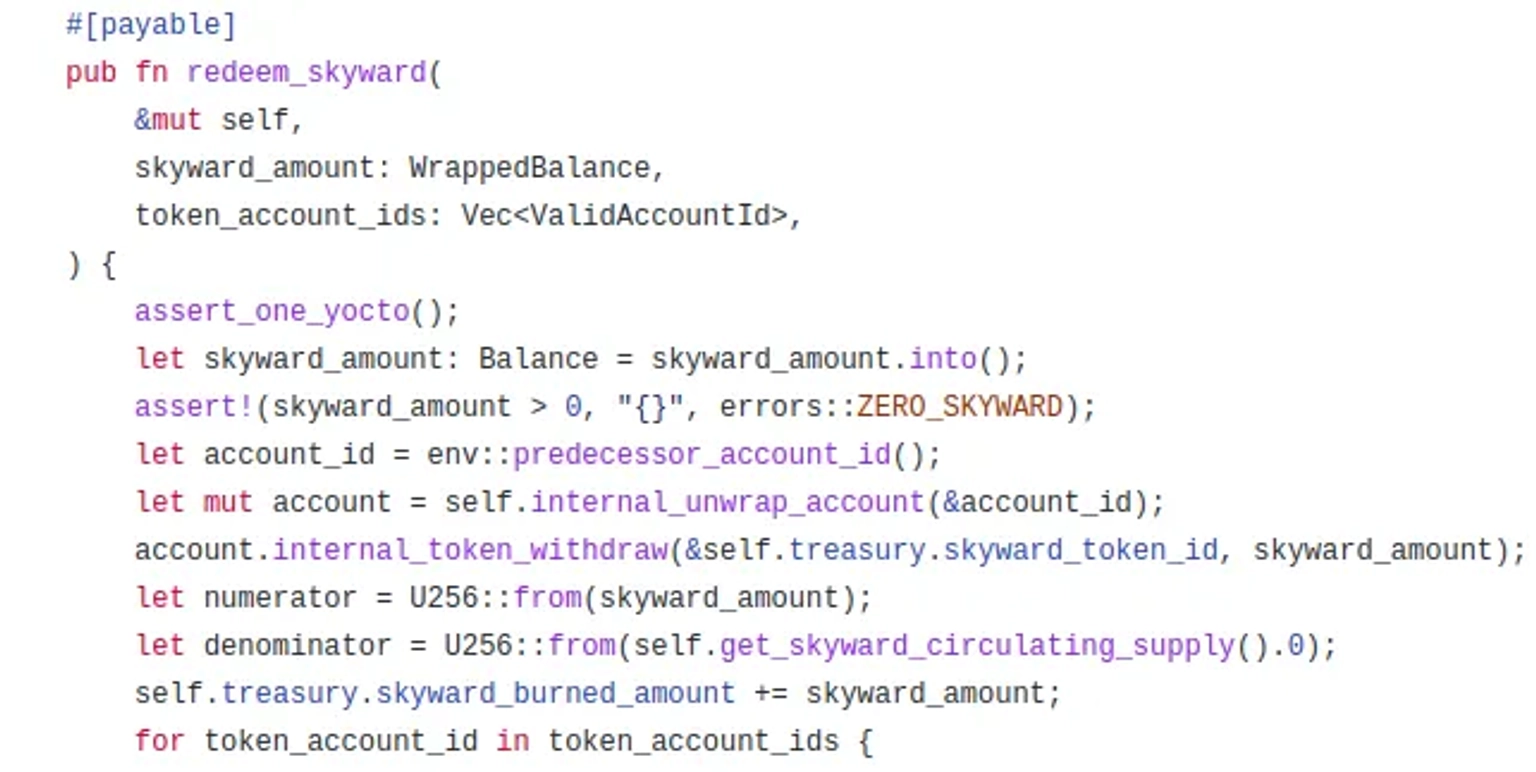
Step 5:
The attacker can thus claim treasury token rewards multiple times by using the same token account id.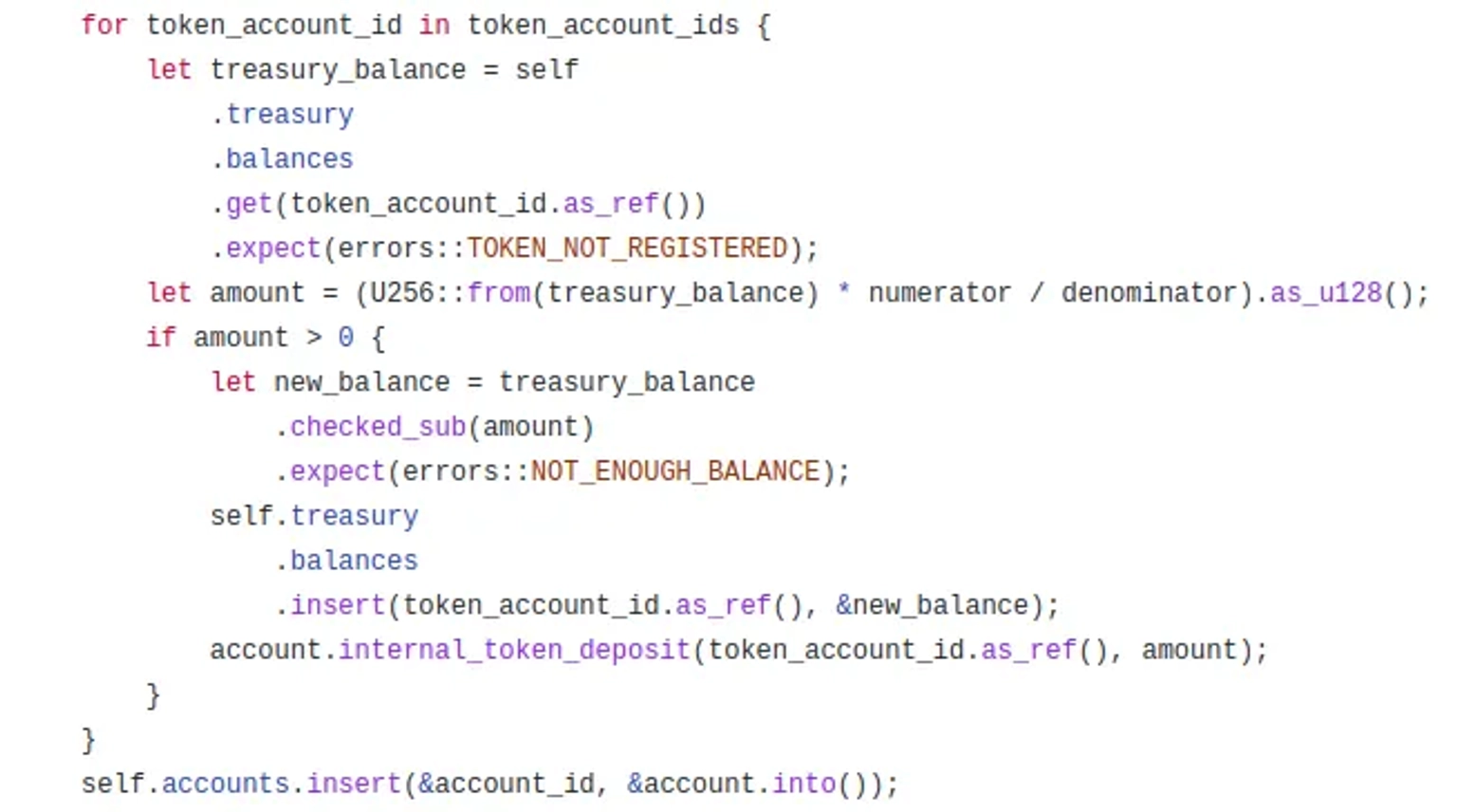
Step 6:
The attacker sent in duplicate token_account_id and used the loop values to deposit the rewards multiple times.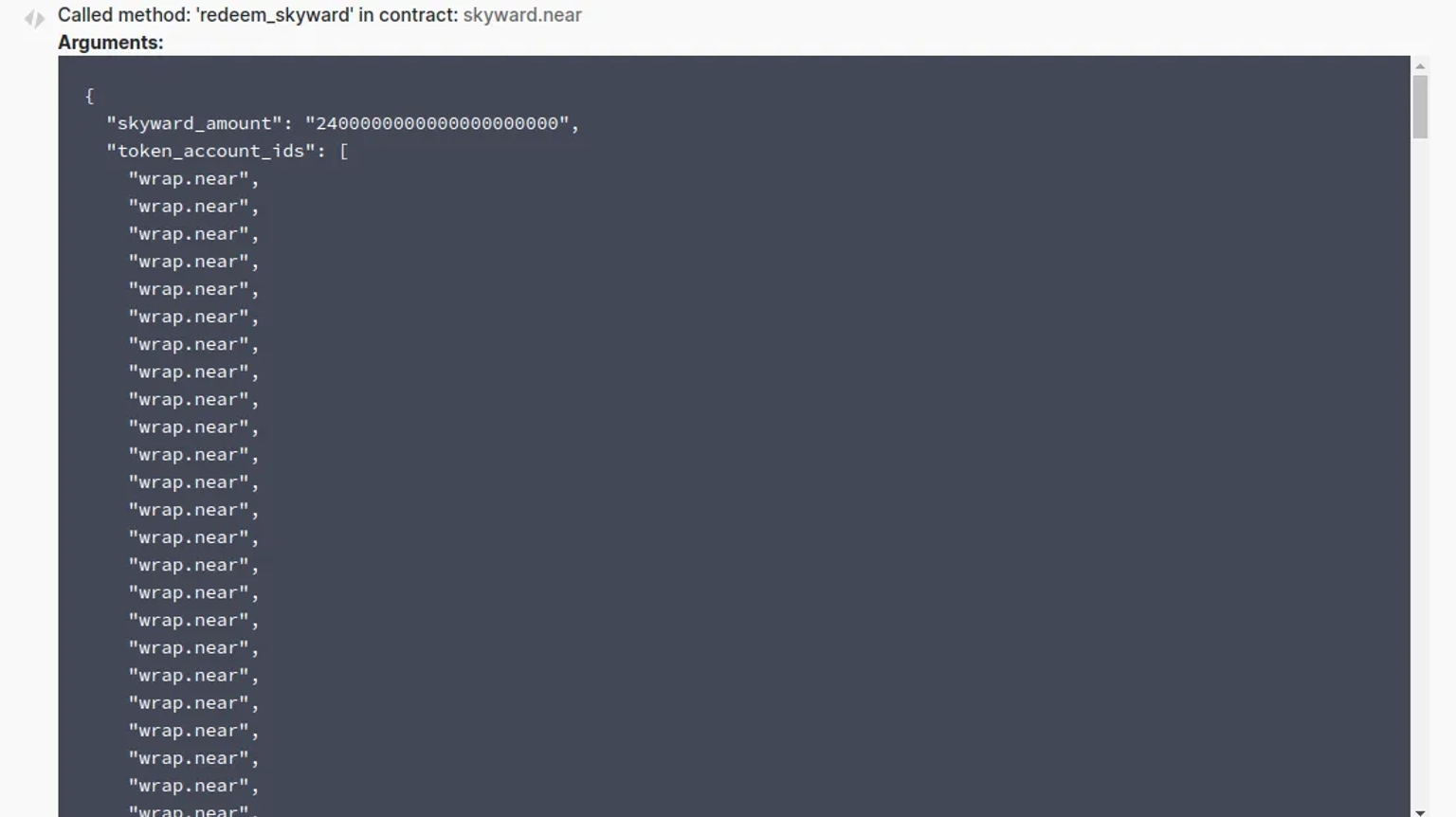
The team informed that the Skyward Treasury was drained due to this attack, effectively rendering the Treasury and the $SKYWARD token worthless. They added that the contracts are fully locked, meaning that no one can pause or prevent future issues with the $SKYWARD token.
The lack of a recovery plan during hacks or exploits is typically indicative of an exit scam. A few of these activities leading to rug-pull in this industry are premeditated and self-made by the team in order to avoid prosecution or gain media attention before planning for their next venture.
This exploit could have been avoided if proper validation techniques had been used to ensure that no duplicate token_account_ids were passed during the functional call. It is also recommended that such values are not passed as parameters, because they can be easily manipulated.
Our security team at Neptune Mutual can validate your platform for DNS and web-based security, smart contract reviews, as well as frontend and backend security. We can offer you a solution to scan your platform and safeguard your protocol for known and unknown vulnerabilities that have the potential to have catastrophic long-term effects. Contact us on social media if you are serious about security and have the budget, desire, and feeling of responsibility to do so.