
Analysis of the Hedgey Finance Exploit
Learn how Hedgey Finance was exploited, resulting in a loss of assets worth $44.7 million.
Youtube Video
Playing the video that you've selected below in an iframe

Melody hacked due to a vulnerability that allowed the application's token address to compromise.
On October 25, 2022, Melody was hacked due to a vulnerability that allowed the application's token address to be compromised, resulting in the loss of approximately 2225 $BNB tokens.
Melody is a play-to-earn web3 entertainment, and social media application covering music creation, karaoke, and more.
The root cause of the attack is that the application's token address was compromised which allowed the hacker to bypass the access control.
Step1:
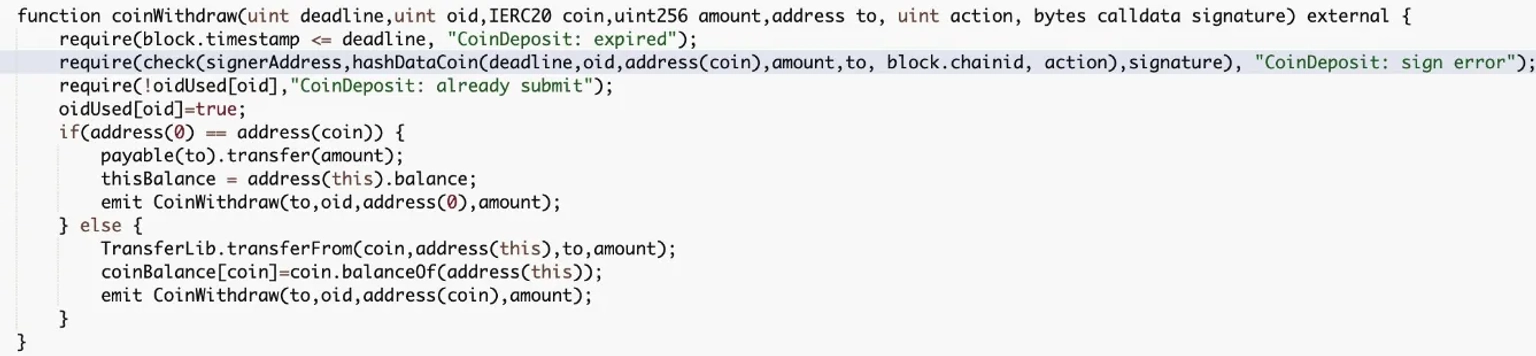
First, the hacker invokes the coinWithdraw function of the SGS contract, which is used to redeem the user's assets from the contract.
Step 4:
This operation can only be completed by users who have the valid signature.
Step 5:
The contract also has a check function that looks for three parameters: signeraddress, output from hashDataCoin function call, and signature.
Step 6:
The signeraddress is a state variable of the contract. This signature was actually the signeraddress when the isValidSignatureNow method was called.
Step 7:
The hacker most likely obtained the signeraddress to generate the signature of the malicious action, transferring $SGS tokens to them.
Step 8:
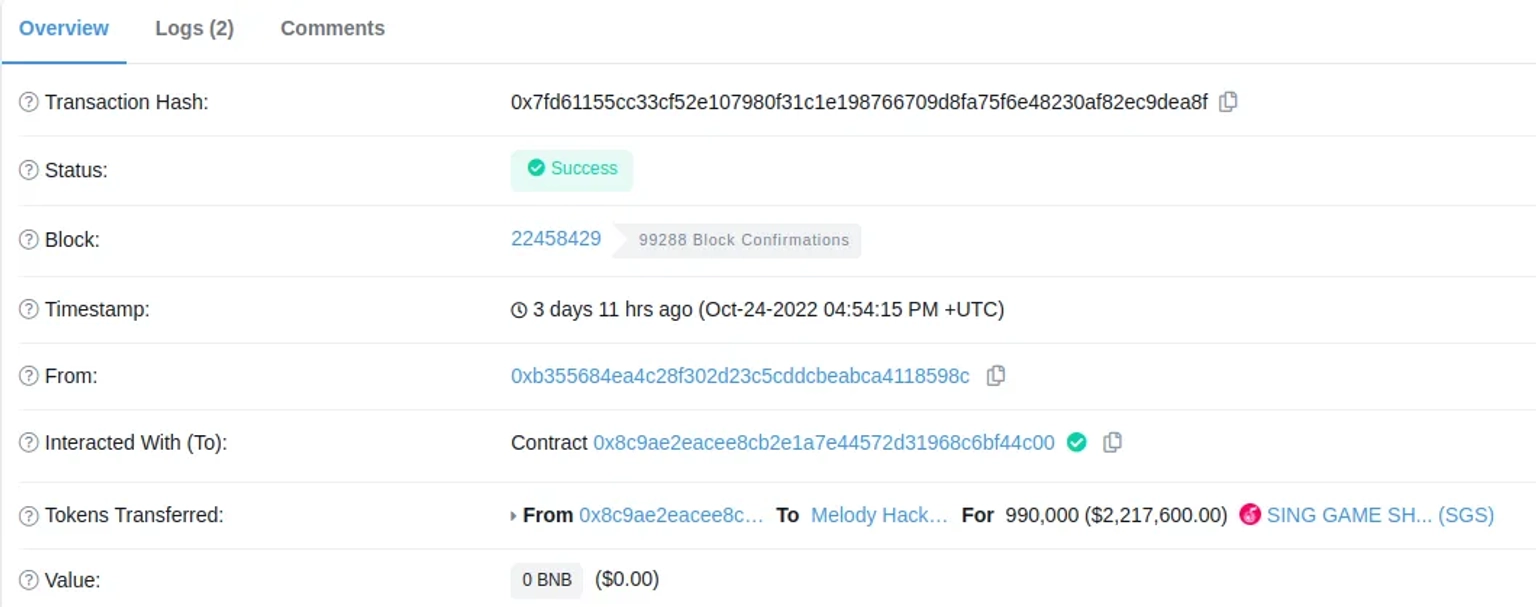
The hackers used PancakeSwap to exchange their 990,000 $SGS tokens for $WBNB.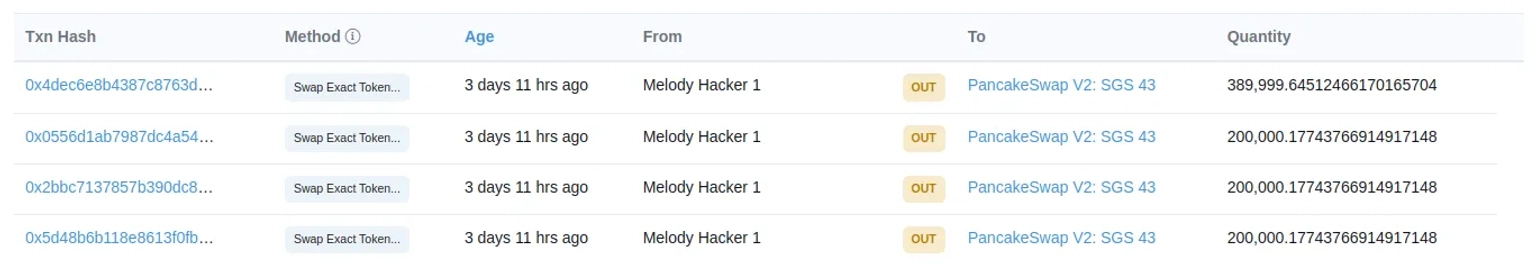
Following the incident, another attacker address repeated the attack, earning 2,450 $SGS and exchanging proceeds for 560 $WBNB.
The team took the contract to maintenance mode and restarted the withdrawal function after the bug was fixed.
The industry has heard about numerous hacks on a regular basis, therefore affirming the security of modules like the signature services are vital for any project team.
The private key of the wallet should always be kept secure.
Our security team at Neptune Mutual can validate your platform for DNS and web-based security, smart contract reviews, as well as frontend and backend security. We can offer you a solution to scan your platform and safeguard your protocol for known and unknown vulnerabilities that have the potential to have catastrophic long-term effects. Contact us on social media if you are serious about security and have the budget, desire, and feeling of responsibility to do so.